5 min read
Qualified Digital Signing and Electronic Signature UK Law
This article aims to demystify electronic signature UK law and explain how it supports all types of electronic transactions in accordance with UK...

5 min read
This article aims to demystify electronic signature UK law and explain how it supports all types of electronic transactions in accordance with UK...

5 min read
Here we look at what it means to “bring your own key”, “control your own key” and “hold your own key” and what the differences are between these...

2 min read
eIDAS will not only usher in a new era of innovation and transparency in how organizations do business, but this regulation is also paving the way...
8 min read
PSD2 breaks up the ways in which banks do their business, by forcing them to open up their APIs. By doing so, PSD2 challenges the way in which data...

3 min read
Cryptography is the backbone of data security technology. In this article, Jo Lintzen, MD at Cryptomathic Inc. explains the preparations for...

4 min read
Encryption key management systems are now essential for all companies needing to lockdown data in the cloud, says Matt Landrock, CEO, Cryptomathic...
3 min read
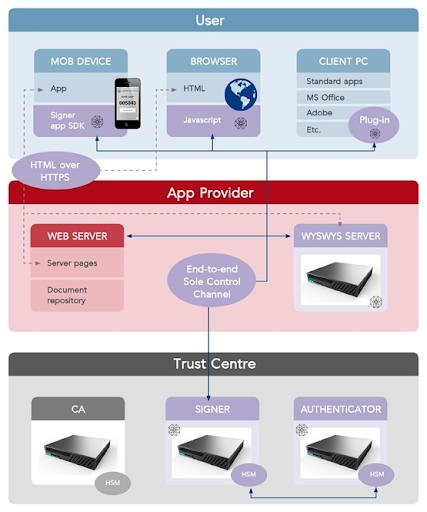
The demand for remote digital signatures to enhance security and customer experience continues to grow across the EU, as the banking and financial...

2 min read
One aspect of key management is dealing with what happens when a symmetric cryptographic key is no longer needed. The section ‘Key Replacement,...

2 min read
This article describes from a CISO perspective how to manage and protect security assets in large organisations, i.e. the cryptographic keys and...