4 min read
Payment Security & Key Management: The Four Corners Model
The “Four Corners” model, also called the “Four Party Scheme”, is utilized in almost all standard card payment systems across the globe. Here, we...

4 min read
The “Four Corners” model, also called the “Four Party Scheme”, is utilized in almost all standard card payment systems across the globe. Here, we...

3 min read
EMV Personalization is a process used to get card data into cards, mobile phones, and wearables. The process includes a variety of complicated...

5 min read
To bank safely online, you need additional mobile app security mechanisms that go beyond standard OS security features. In this article, we take an...

3 min read
As the use of mobile phones for mobile banking and payment applications increases, so too do the security threats. Most smartphones use only two...

4 min read
Among all the various key block formats, the TR-34 format is undoubtedly one of the most sophisticated. The TR-34 norm is an implementation of the...

3 min read
This article proposes a few answers to a series of frequently asked questions (FAQs) about key blocks and their use with PCI.

4 min read
In the “four corner model”, acquirers are apparently the less active party as their role seems ‘only’ to forward the transaction flow originating...

3 min read
An issuer is one of the corners in the ‘four corner’ model. An issuer is a financial organization (e.g. a bank) that produces payment cards and...
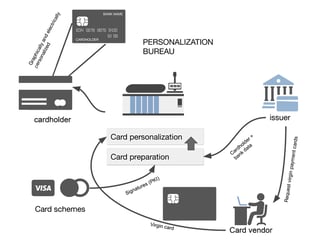
3 min read
The EMV personalization data processing in itself is not the topic of this article, we will instead focus on the cryptographic schemes involved in...