2 min read
UK Survey Reveals the Need for eIDAS Qualified Electronic Signatures
The Conveyancing Association (CA) in the UK has revealed the findings of its 2022 Lender Survey, which it strongly believes will assist in...

2 min read
The Conveyancing Association (CA) in the UK has revealed the findings of its 2022 Lender Survey, which it strongly believes will assist in...

2 min read
Just a month ago, NIST announced its selection of three digital signature algorithms and one key establishment mechanism (KEM) for future use in...

3 min read
Traditionally, end-to-end lifecycle key management was achieved through inefficient paper-based procedures and highly resource intensive tasks...

3 min read
Encryption has become the most essential part of securing data online. The biggest headache to the Cybersecurity industry is a data breach. The last...

3 min read
With the ever increasing number of online services and electronic transactions, business owners are becoming ever more dependent on the use...
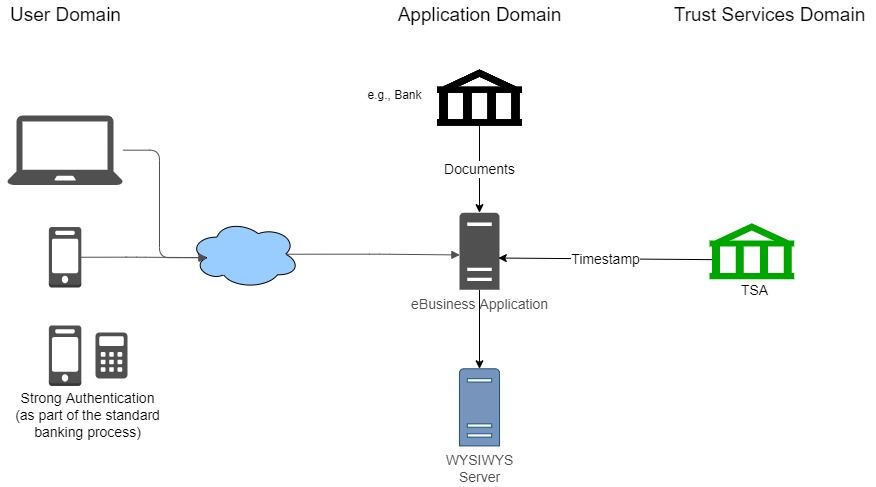
2 min read
In this article, we proposeWhat-You-See-Is-What-You-Timestamp (WYSIWYT) as an attractive alternative to Qualified Electronic Signatures, for certain...

5 min read
Certain industries have a necessity to protect confidential information as well as a requirement for authentication - proving that a document was...
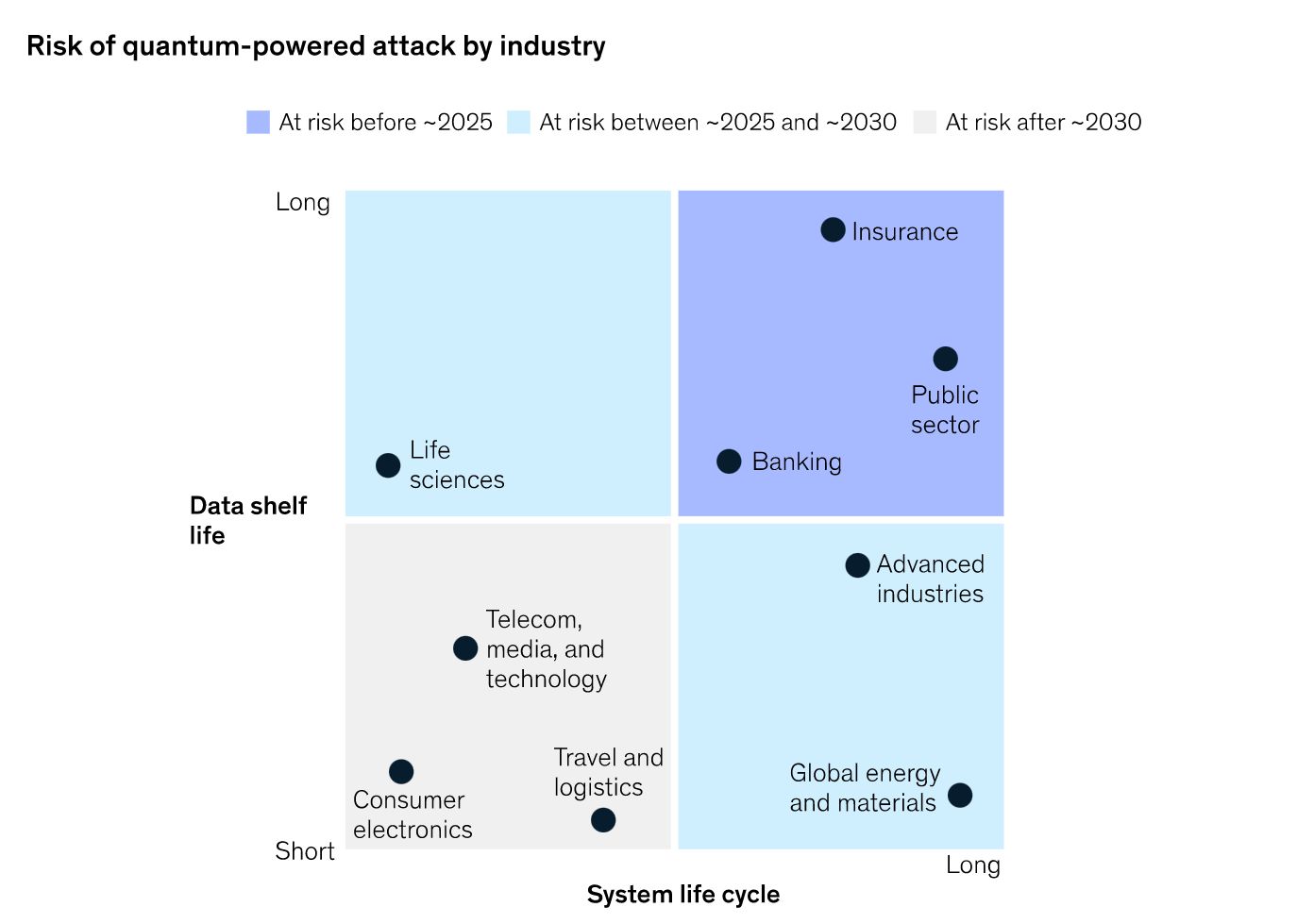
3 min read
An over five-year-long process has come to a preliminary end: On July 5, 2022, NIST issued the long-awaited announcement of the winners of Round 3 of...
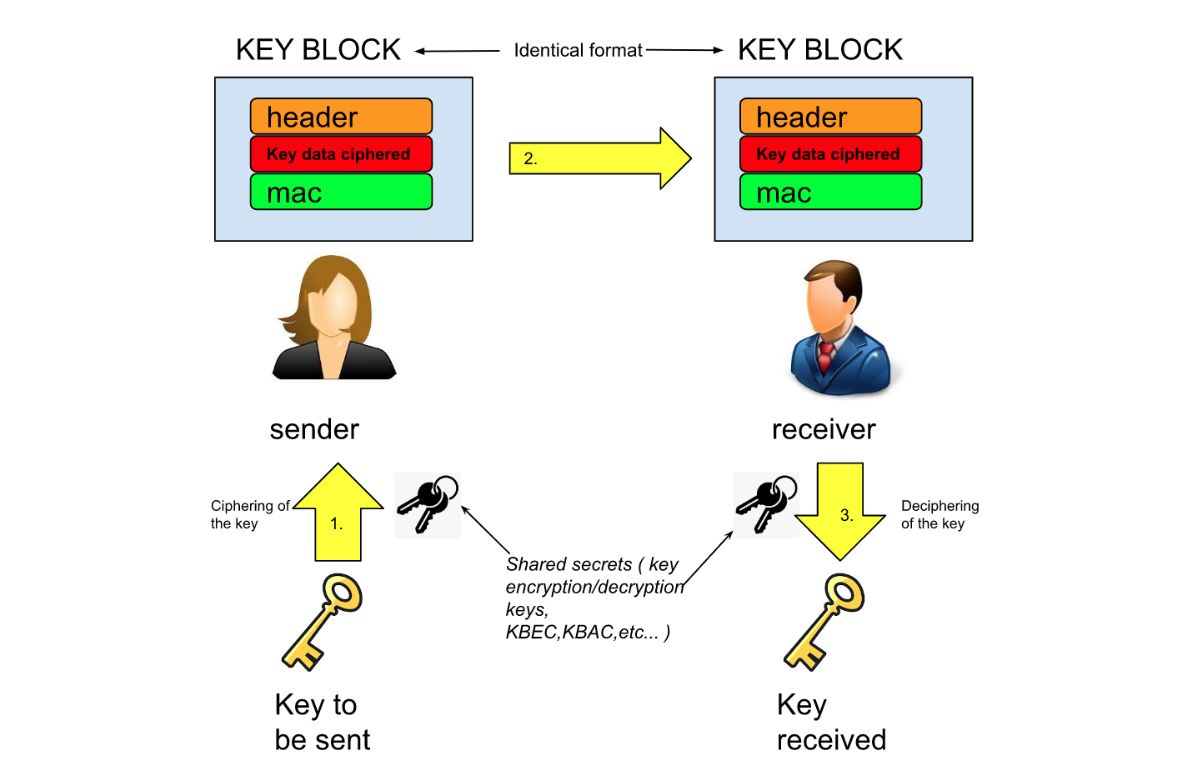
2 min read
There are several types of key block formats used in different industries, especially the retail banking industry. The systems that use these key...