2 min read
Secure AWS BYOK Service for DynamoDB
In this article we will explain what AWS DynamoDB does and how Cryptomathic's AWS BYOK Service is an option for providing secure key management as a...
Dawn M. Turner is a professional author with a passion for technical regulations and standards, as well as for their relevance and impact on corporate operations and industry in general. Dawn has more than 10 years of IT industry experience in hardware, programming & systems & network engineering. Her educational background includes a Certificate in computer operations & programming, CompTIA and Microsoft certifications, including A+, MCSE and MCP, Associates degree with major in business & minor in computer science, Bachelors of Science degree with major in business forensics & minor in accounting and an MBA with concentrations in finance & economics.

2 min read
In this article we will explain what AWS DynamoDB does and how Cryptomathic's AWS BYOK Service is an option for providing secure key management as a...
3 min read
This article discusses using Cryptomathic’s BYOK and key management service for securely managing cryptographic keys used in AWS applications.

3 min read
As defined by Regulation (EU) No 910/2014 (eIDAS), which took effect on 1 July 2016, an electronic signature creation device is software or hardware...

5 min read
Here we look at what it means to “bring your own key”, “control your own key” and “hold your own key” and what the differences are between these...
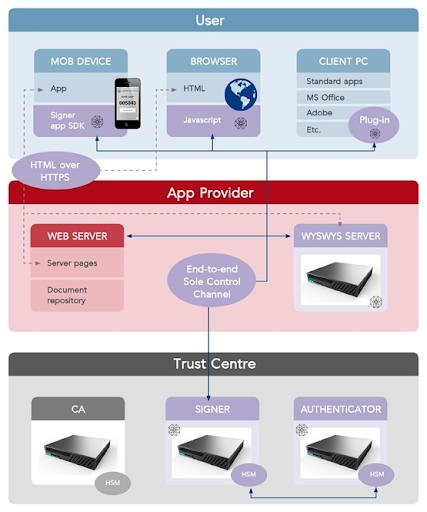
3 min read
The demand for remote digital signatures to enhance security and customer experience continues to grow across the EU, as the banking and financial...

4 min read
For years, there has been persistent chatter that quantum computing is coming and that organizations should be prepared for its arrival. But what...

5 min read
There is no question that quantum computing is coming. However, organizations need to question themselves as to whether they will be vulnerable to...

3 min read
Most current public-key cryptography (asymmetric) algorithms are vulnerable to attack from large-scale quantum computers. In its efforts to...

3 min read
Microsoft’s Azure Key Vault Managed HSM allows customers to safeguard their cryptographic keys for their cloud applications and be...