4 min read
Payment & Banking Cryptography: The Benefits of z/OS & the Z Platform
This article looks at some reasons for popularity of the IBM mainframe platform in the banking sector and touches upon its limitation for...
Dawn M. Turner is a professional author with a passion for technical regulations and standards, as well as for their relevance and impact on corporate operations and industry in general. Dawn has more than 10 years of IT industry experience in hardware, programming & systems & network engineering. Her educational background includes a Certificate in computer operations & programming, CompTIA and Microsoft certifications, including A+, MCSE and MCP, Associates degree with major in business & minor in computer science, Bachelors of Science degree with major in business forensics & minor in accounting and an MBA with concentrations in finance & economics.

4 min read
This article looks at some reasons for popularity of the IBM mainframe platform in the banking sector and touches upon its limitation for...
3 min read
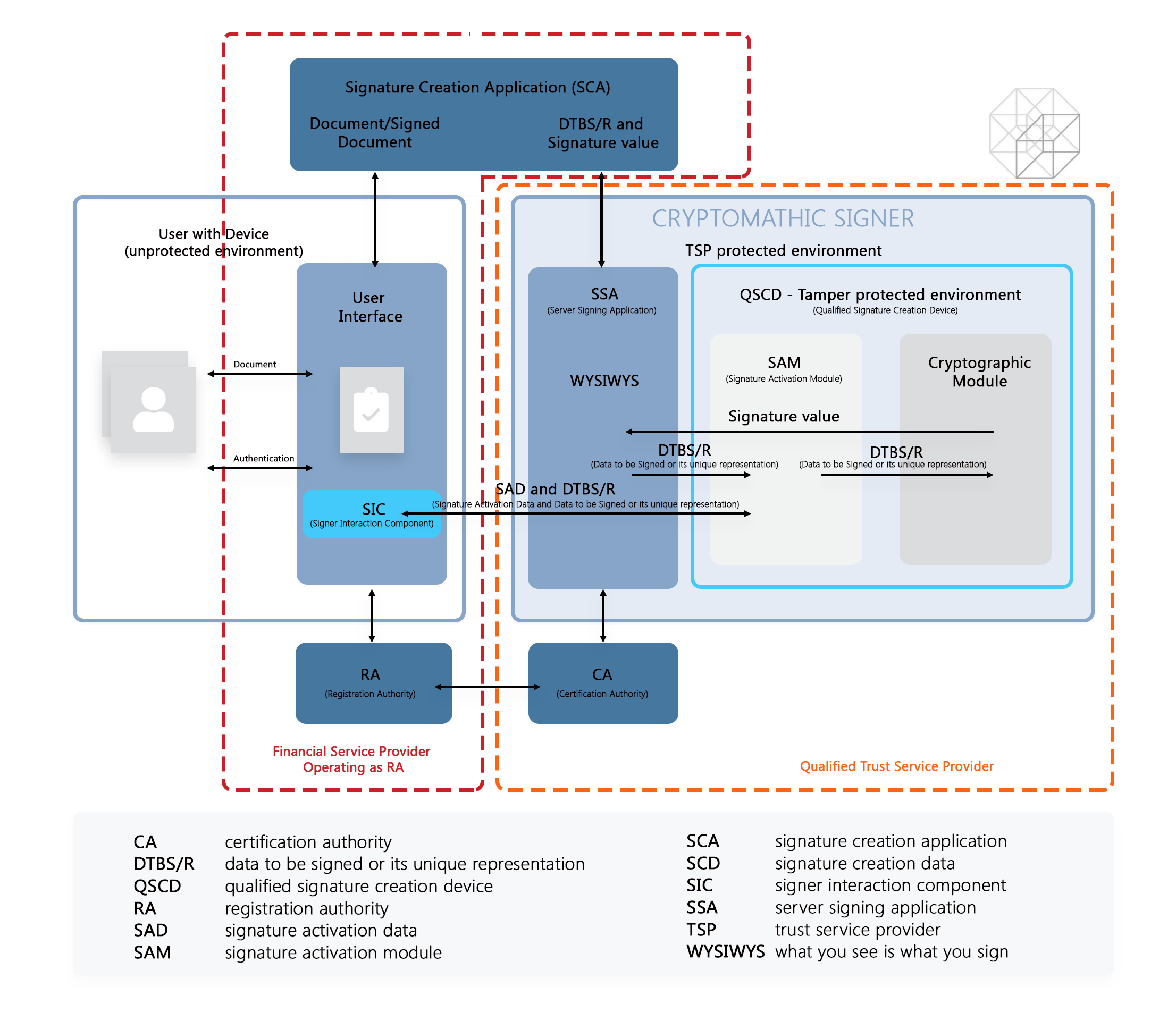
The eIDAS regulation provides both the technical and legal framework for electronic identification and digital signatures that the banking sector...
5 min read
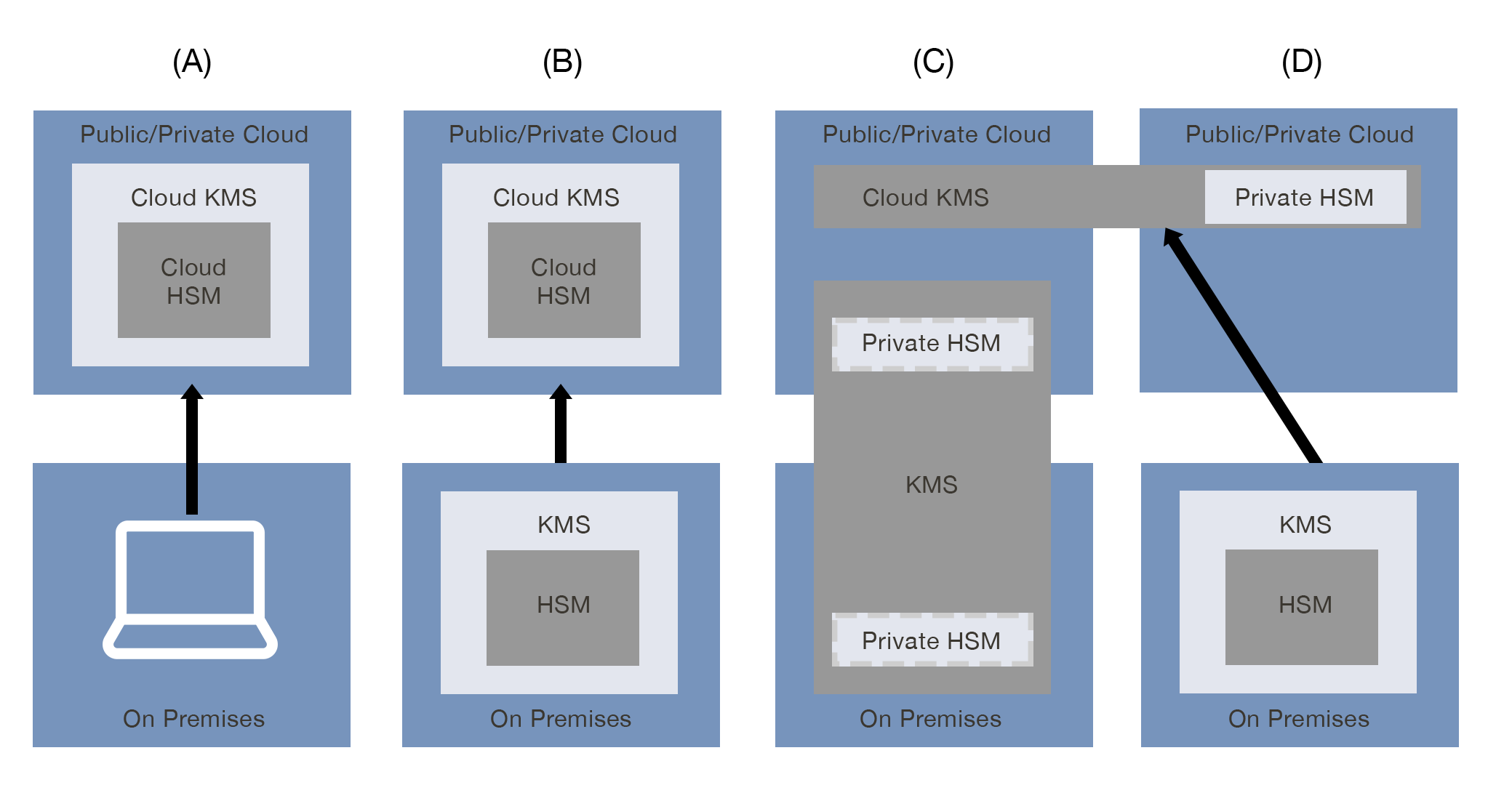
This article explains the four primary cloud KMS pattern combinations and which are best suited for use with Cryptomathic’s Key Management System...

3 min read
Bring your own key (BYOK) is a popular term relating to key management for cloud applications. However, a lack of standardization makes it confusing...
2 min read
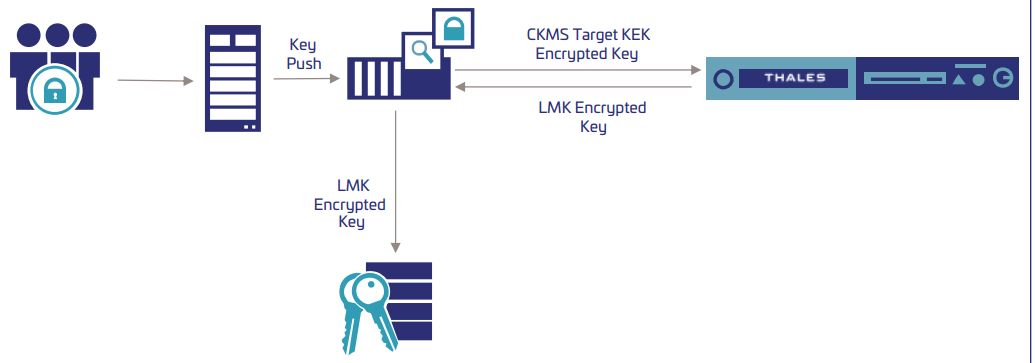
Banks and financial institutions must adhere to a rigorous set of security and regulatory practices to protect data, communications, and processes.

3 min read
The protection and secure management of cryptographic keys is crucial for ensuring that cryptography is used in the most effective way to keep data...

4 min read
Recent global events have demonstrated that high-profile hackers and state-sponsored security breaches have been steadily increasing since 2020. It...
3 min read
This article discusses the misuse of X.509 certificates and keys in the SolarWinds attack and how Cryptomathic CKMS and CSG could help protect...

3 min read
The Key Management Interoperability Protocol standard intends to provide interoperability across various key management environments and hence to...