4 min read
Stay Ahead of Emulator-Based Attacks: Securing Mobile Banking Apps in 2025
Attacks on mobile banking and payment applications frequently begin with the use of an emulator for the mobile operating system, where the targeted...

4 min read
Attacks on mobile banking and payment applications frequently begin with the use of an emulator for the mobile operating system, where the targeted...

3 min read
With the increasing adoption of mobile banking and payment apps, financial institutions face greater challenges in securing cardholder data. The...

3 min read
For an internal event atCryptomathic, we invited some our clients from the financial and trust service sectors to share their insight on future...

4 min read
The recent instability of a major bank that catered to US tech startups caused concern for several prominent tech companies and venture capitalists,...

3 min read
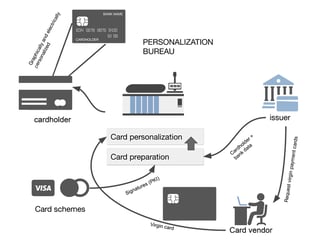
EMV Personalization is a process used to get card data into cards, mobile phones, and wearables. The process includes a variety of complicated...

5 min read
To bank safely online, you need additional mobile app security mechanisms that go beyond standard OS security features. In this article, we take an...

3 min read
As the use of mobile phones for mobile banking and payment applications increases, so too do the security threats. Most smartphones use only two...
3 min read
The EMV personalization data processing in itself is not the topic of this article, we will instead focus on the cryptographic schemes involved in...

4 min read
IBM’s mainframe computers have been a rock-steady part of banks’ security infrastructure for many years. Originating from the local data-center...