3 min read
NIST Releases Quantum-Resistant Cryptography Standards. Act Now!
 Edlyn Teske
:
22. July 2022
Edlyn Teske
:
22. July 2022
An over five-year-long process has come to a preliminary end: On July 5, 2022, NIST issued the long-awaited announcement of the winners of Round 3 of the NIST Post-Quantum Crypto (PQC) Standardization Process, that is, which quantum-resistant cryptographic algorithms NIST has selected for standardization.
This is the list:
- Public-Key Encryption/Key Encapsulation Mechanisms (KEM): CRYSTALS-KYBER.
- Digital Signatures: CRYSTALS-Dilithium (as primary), Falcon, and SPHINCS+.
Furthermore, the BIKE, Classic McEliece, HQC, and SIKE Public-Key Encryption/KEM algorithms were selected as candidates for a 4th round of evaluation for potential standardization at a later time.
We have been waiting for this to happen!
This announcement has long been awaited, not only in the US, but across most of the world. As we read in the European Union’s May 2021 Enisa report: “Since the NIST standardisation process is going, the report makes no claim on the superiority of one proposal [of a PQC algorithm] against another. In most cases, the safest transition strategy involves waiting for national authorities to standardise PQC algorithms and provide a transition path.“ And Germany’s BSI states in their latest report: “BSI welcomes the NIST process as a method of defining standards in a transparent international process that can then be used worldwide. It is particularly opposed to a separate process for standardising German or European algorithms. A "proliferation" of international standards would both hamper interoperability and reduce the market opportunities of crypto producers. In addition, a splitting of personnel and research resources would lead to a lower evaluation quality for those algorithms that are ultimately selected.”
Indeed, this multi-year evaluation process of the 80+ initial submissions involved significant participation of the international crypto research community and included three “NIST PQC Standardization Conferences” and ample vivid discussion on NIST’s pqc-forum. Thanks to this process, algorithms were improved and parameters were adjusted to increase security and/or performance; a number of contenders in the competition were broken early in the process, others later, with the break of the Rainbow algorithm happening only a few months ago. However, while the winning algorithms certainly have undergone some scientific scrutiny, they still have to withstand the test of time!
The clock is ticking
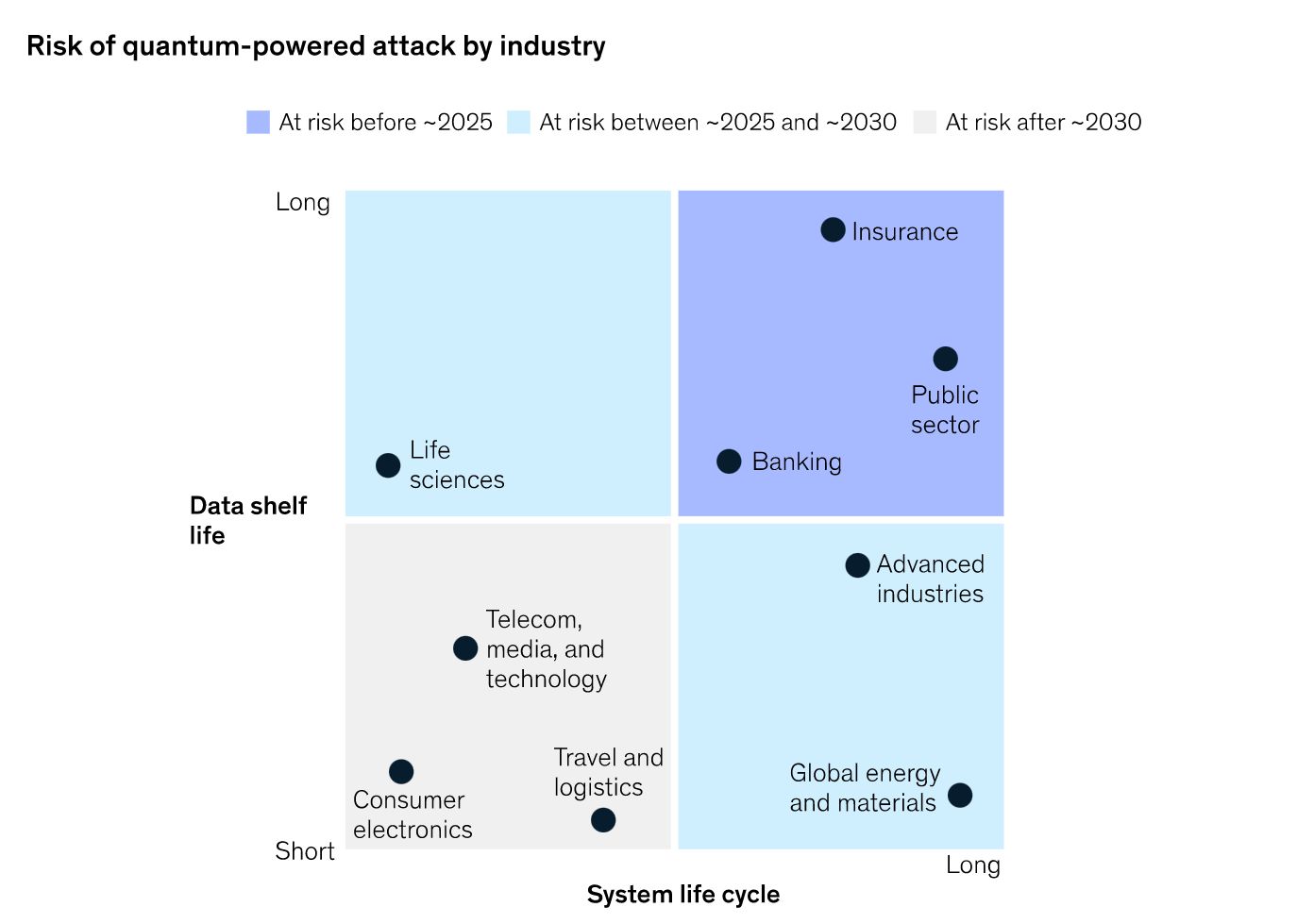
Meanwhile, there is no time to waste getting post-quantum ready! As this illustration from an article by McKinsey suggests, for any entity whose sensitive data have a long shelf life, or whose security systems have a long lifecycle, the risk of quantum computing is imminent. For example, data that are being encrypted today by a quantum-vulnerable algorithm, such as RSA, can be intercepted by an adversary now for decryption later when the quantum computing technology is available to do so. Thus, these sectors, such as in particular the financial, insurance, or government sector, must act now, by integrating post-quantum cryptography into their security infrastructure to avoid compromise of their long-term certificates or encryption mechanisms further down the road.
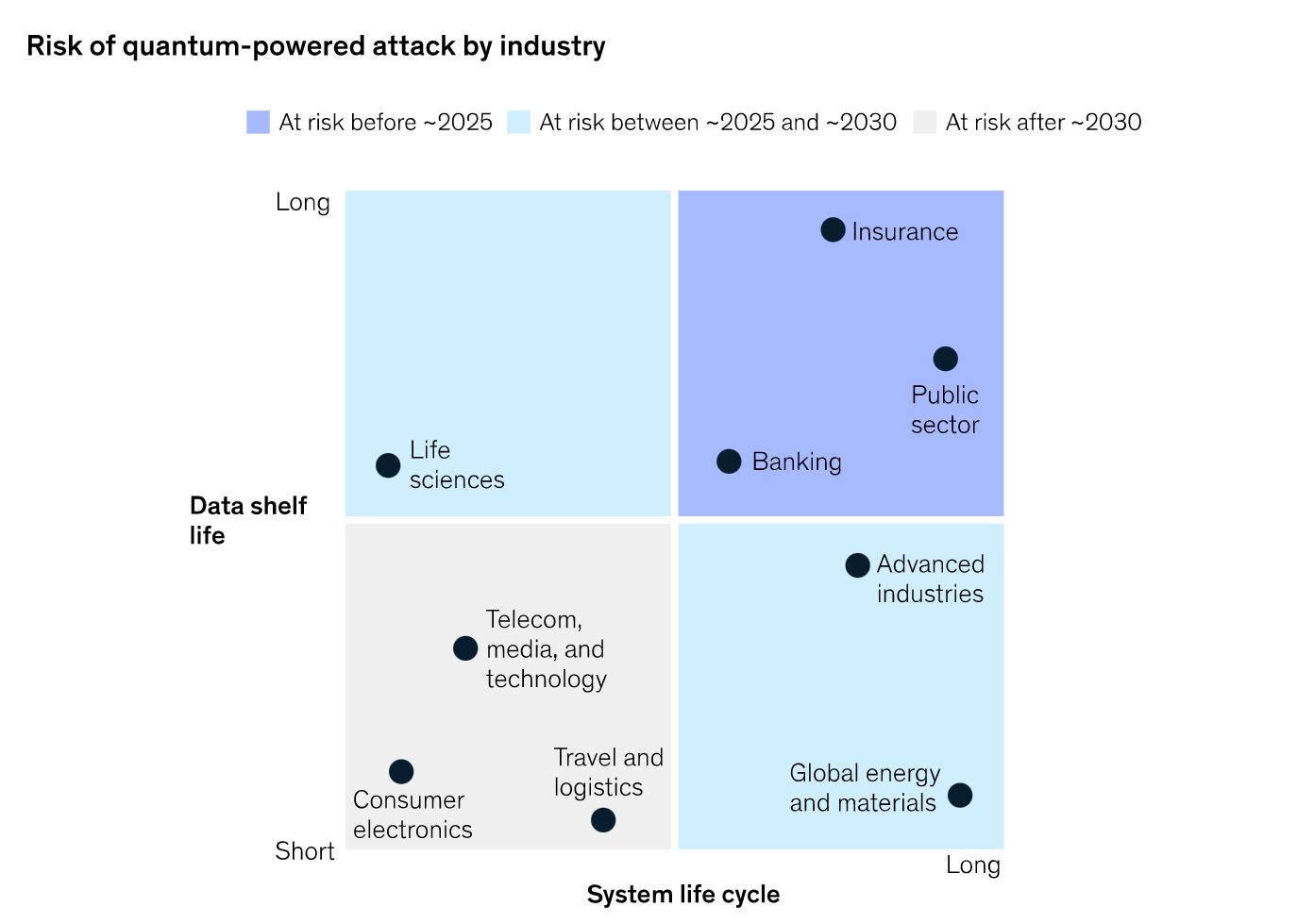
(Source)
Hopefully, the NIST announcement will
-
stimulate manufacturers of Hardware Security Modules to add these quantum-safe cryptographic algorithms to their offerings,
-
cause crypto providers to add support for these algorithms, and
-
increase users’ demand for post-quantum crypto solutions.
 However, this process takes time! Algorithms have now been selected that will be standardized, but the standards aren’t out yet and won’t be out until at least 2024. Furthermore, just like with any currently deployed crypto algorithms, there is no guarantee for the security of any of these newly chosen algorithms. Cryptoanalysis will continue, and new findings may render one or the other algorithm less secure than previously believed. This is nothing new, it has happened before when DES was broken, when SHA-1 was broken, when RSA with moduli of size 1024 and below became insecure, and so forth.
However, this process takes time! Algorithms have now been selected that will be standardized, but the standards aren’t out yet and won’t be out until at least 2024. Furthermore, just like with any currently deployed crypto algorithms, there is no guarantee for the security of any of these newly chosen algorithms. Cryptoanalysis will continue, and new findings may render one or the other algorithm less secure than previously believed. This is nothing new, it has happened before when DES was broken, when SHA-1 was broken, when RSA with moduli of size 1024 and below became insecure, and so forth.
In fact, all current standards are the result of an ongoing process of integrating new research findings. To add more complexity to the topic, it must be asked if classical post-quantum cryptography is enough?
Or whether quantum cryptography, such as quantum key distribution, is the only quantum-safe alternative?
Act now despite uncertainties: become Crypto-Agile!
The Cryptomathic Crypto Service Gateway (CSG) is designed to provide this crypto-agility.
CSG is a centralized cryptographic management platform, which acts as an abstraction layer between crypto applications and Hardware Security Modules (HSMs).
CSG ensures that authenticated users are authorized to execute specified cryptographic operations and specified crypto algorithms. This process of authorization is controlled by the CSG policy engine and configured through CSG policy, which is built into the CSG platform – thereby enabling changes to crypto parameters (by designated security personnel) without touching the application code.
The complete separation of the security policy from the application code allows for easy policy updates, should this be required by sudden breakthroughs in cryptoanalysis, changes in standards or best-practices recommendations, or to achieve quantum readiness.
Cryptomathic is a market leader in key management and crypto-agility solutions. Download the eBook on Post Quantum Computing and Crypto Agility or contact us to discuss your needs.