3 min read
Cryptomathic adds XML signing to its WYSIWYS Solution
With support for signing XML documents in its WYSIWYS solution, Cryptomathic now provides the means to offer the much-desired What You See Is What...
Guillaume Forget is Managing Director at Cryptomathic GmbH, where he leads the German subsidiary operations. Guillaume is also responsible for ensuring Cryptomathic’s unique technology, IP portfolio and innovation capacity can meet the market´s desire for a high level of security assurance. Guillaume has wide industry knowledge and is an evangelist in the eSignature and What You See Is You Sign space, where he has co-authored several papers and patents. To date, Guillaume has successfully co-ordinated numerous key Cryptomathic projects, including large scale central signing deployments across Europe.

3 min read
With support for signing XML documents in its WYSIWYS solution, Cryptomathic now provides the means to offer the much-desired What You See Is What...

5 min read
This article was originally published in the Banking Automation Bulletin, Issue 352
3 min read
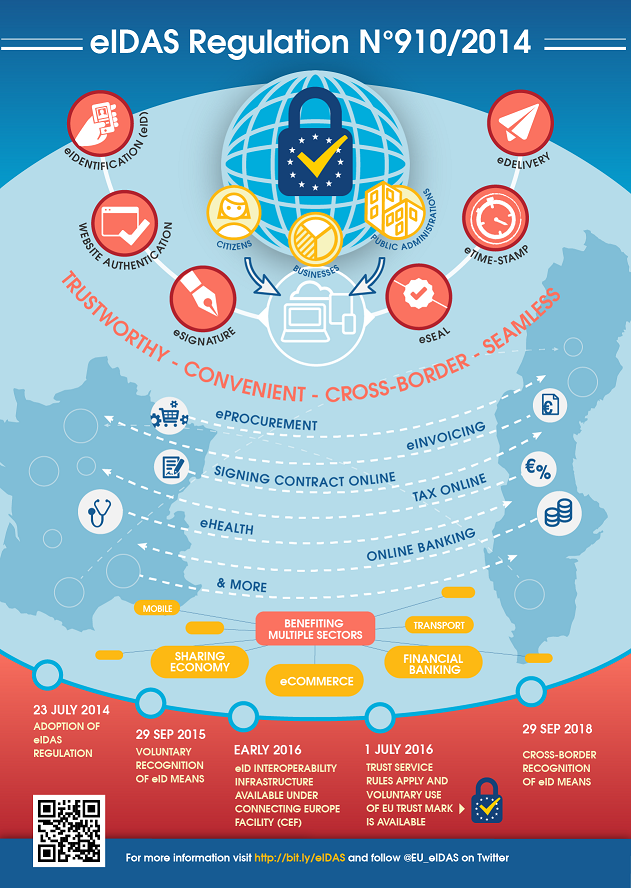
As of 1st July 2016, the first phase of the EU’s new regulation on electronic identification (eIDAS) will become enforceable. But amid all the...

3 min read
...continued from Part 1 The threat model Malicious mobile device hackers have a variety of goals. Foremost is monetary gain, but retribution,...
3 min read
With mobile devices being used for more credentialing based activities, the question of mobile security is becoming increasingly important. The...