
Part 2 – Accelerating Time-to-Market
With the increase in e-commerce and electronic communications on the one hand and the growing challenges of cybercrime and data protection regulation, on the other hand, cryptography is becoming an increasingly important business enabler.
This is especially true in the banking and financial services industry, where large sums of money attract cybercriminals, but also in emerging industries such as FinTech, IoT, and blockchain, whose business models are heavily dependent on cryptography to provide the necessary security and privacy.
Developing New Cryptographic Applications
Consequently, many organizations are developing new cryptographic applications, and with the need to be increasingly agile in today’s competitive markets, they need to do so at pace. However, the difficulty of scoping and delivering a cryptographic project increases with the number of actors and platforms it must accommodate. If the project involves layering additional security onto a pre-existing system without impacting either performance or availability, then the challenges are even greater. The potential complexity of cryptographic project workflows is illustrated in Figure 1.
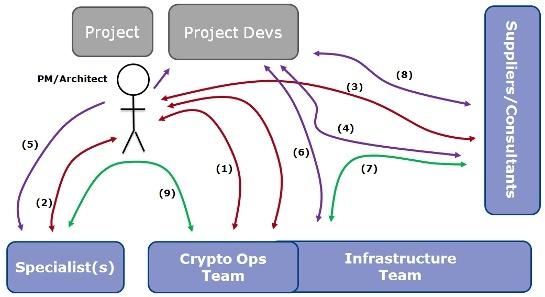 Figure 1: Cryptography Development Project Workflows
Figure 1: Cryptography Development Project Workflows
These workflows are likely to have multiple iterations, and it may prove impossible to achieve all the objectives within the imposed constraints. As a result, using cryptography often becomes, or is perceived as, responsible for holding up entire projects. Responding to these development challenges requires organizations to move away from the project-by-project model and embrace a more proactive and sustainable approach to developing and managing cryptography.
Avoiding Choke Points with Crypto Service Gateway
Cryptomathic's Crypto Service Gateway (CSG) is the world's first embodiment of an integrated cryptographic service model, ideally suited to the demands of 'application-level cryptography.' This model improves workflows making it easier for organizations to enhance their business systems to provide end-to-end protection and security of sensitive data. Organizations can protect as much or as little business data as is considered necessary - within transaction flows or data at rest - in a disciplined and controlled manner.
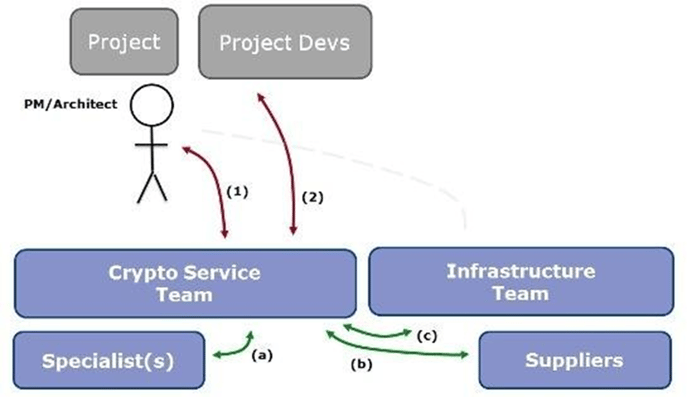 Figure 2: Improved Workflows with CSG
Figure 2: Improved Workflows with CSG
CSG provides a fully integrated cryptographic environment that scales easily with the number and size of applications within your business. Rather than working with a range of complex, often proprietary HSM interfaces that require much detailed cryptographic knowledge, developers can work with a single, simple crypto API and spend more time focusing on the business logic.
Furthermore, crypto policy definition can be left in the hands of a small team of security specialists who can enforce it across all applications, so it is no longer a challenge that every project has to address individually; subsequent changes in crypto policy (e.g., changes of algorithm or key length) become easy to implement across the board, without having to modify each application.
This new crypto service model also works to the advantage of project managers, providing a range of advantages such as:
- CSG removes the need for the project to purchase HSMs for both the
 development and production parts of the project - this activity can be deducted from what is typically the critical path for the project, leading to savings of 6 to 8 weeks elapsed time (particularly where cryptography is introduced late and unplanned into the scope of a project).
development and production parts of the project - this activity can be deducted from what is typically the critical path for the project, leading to savings of 6 to 8 weeks elapsed time (particularly where cryptography is introduced late and unplanned into the scope of a project).
- The adoption of CSG will naturally lead to an increasing range of proven tools and techniques that do not have to be a re-proven per-project basis. These techniques will have proven cryptographic capabilities, which assist in reducing the number of unknowns for all projects.
- CSG provides central policy enforcement to significantly reduce the elapsed time required for independent scrutiny of cryptography within a new project or enhancement. This is built in as standard to CSG, as are comprehensive levels of auditing and logging. As a result, certain activities can either be dropped completely from the development project plan, or become a single, modest task rather than a whole set of complex tasks.
- Projects using CSG will have faster access to all available specialist expertise in the organization. There may be challenges or difficulties, but the project isn't on its own. Your project’s challenge may have been faced by others previously, and a solution or explanation may be available.
- As deploying cryptographic solutions using CSG becomes your organization’s norm, this leads to a natural reduction in a single point of failure dependencies within the production systems’ support and enhancement teams.
The result is that projects can be completed more quickly, on a lower budget, and with less risk; the resulting business applications are more maintainable.
The Enlightenment Opportunities Using CSG
Businesses often view the inclusion of cryptography at the outset of a project as a necessary evil. Consequently, they frequently opt for a 'tactical solution' because the proper 'production-strength solution' will cost the project perhaps 30% more and, more importantly, add an extra 5 weeks to the project's duration. However, once the tactical solution has been developed, and the service is operational, what is the likely appetite for going back and putting in the production-strength solution (and risk-breaking something) compared to other business priorities that promise a higher return on investment (ROI)? In contrast, using an integrated service model allows the organization to design cryptography correctly from the outset, reducing time and costs.
A clear vision of how your organization can harness an enabler such as Cryptomathic’s Crypto Service Gateway is fundamental. This vision can be modest or aggressive and could have one, several, or all of the following characteristics:
- Internal and external compliance
- CSG’s central policy enforcement uses a fine-grained but straightforward policy language, which allows administrators to control exactly what keys and commands different system users have access to. The policy language is simple enough to show to auditors and business architects who do not have programming experience.
- CSG has extensive usage and audit logging, digitally signed for non-repudiation, which, together with the policy language, allows projects to demonstrate both theoretical and actual compliance with regulations easily.
- Proactive monitoring of existing HSM estates
- CSG enables maintenance and measurement of overall systems’ SLAs for applications that use cryptography, where the cryptographic capabilities cannot and must not be seen as a system weak point or performance 'chokepoint'.
- CSG allows better HSM utilization to be achieved consistently and resiliently.
- HSM vendor independence
- The use of CSG can assist an organization in controlling its level of vendor dependency. Many organizations have policies that stipulate that they wish to have dual or multiple sources of equipment supply. In recent years, however, the HSM marketplace has been consolidating, making vendor independence a moving target. Without CSG, substituting a different manufacturer’s HSM equipment is rarely straightforward. It requires significant effort, while there are invariably more exciting business-focused activities for your development and support personnel to undertake.
- Use of CSG gives an organization the freedom to adopt the latest and most technically- and commercially effective HSM equipment. This can be achieved far more readily than for new and existing systems.
- Proactive cryptographic lifecycle management
- Proactive changes to the cryptographic functionality within a business system have always been highly desirable but rarely achievable, such changes having invariably been undertaken on a special project basis. Using CSG, it is now possible to ensure that such events can be accommodated without disproportionate impacts on the underlying business applications. If the unexpected need to cease using a cryptographic technique, e.g., in response to the discovery of weakness, having CSG available to assist in a timely resolution could prove vital.
- CSG can be readily integrated with Cryptomathic’s Crypto Key Management System (CKMS) to achieve seamless and transparent key changes.
- The ability to manage HSM firmware upgrades and incremental HSM deployments centrally contain the cost to the organization in both the production and development environments.
Conclusion
CSG enables organizations to be more agile while reducing the cost of developing, operating, and maintaining their cryptographically enabled business applications.
Cryptomathic can assist your organization in determining the benefits and ROI achievable from deploying CSG. This exercise will likely prove very illuminating and result in a strong business case for using CSG.
Turning Cryptography into a Service Part 1 – Increasing Efficiency & Resilience
References and Further Reading
Selected articles on HSMs (2013-today), by Ashiq JA, Peter Landrock, Peter Smirnoff, Rob Stubbs, Steve Marshall, Torben Pedersen and more
 Rob Stubbs
Rob Stubbs

