4 min read
TR-34 Key Blocks for the TR-34 Exchange Protocol: Basic Principles
Among all the various key block formats, the TR-34 format is undoubtedly one of the most sophisticated. The TR-34 norm is an implementation of the...

4 min read
Among all the various key block formats, the TR-34 format is undoubtedly one of the most sophisticated. The TR-34 norm is an implementation of the...

3 min read
This article sheds light on the intersection of legal and technical aspects when hosting data on AWS as a European company.
3 min read
This article discusses using Cryptomathic’s BYOK and key management service for securely managing cryptographic keys used in AWS applications.

3 min read
As certain industries are moving ahead with digital transformation projects, online signing processes are a step forward in optimizing business...

3 min read
On April 19, 2022, information about a severe vulnerability in recent versions of Java shook up the security community.

3 min read
This article proposes a few answers to a series of frequently asked questions (FAQs) about key blocks and their use with PCI.

3 min read
As defined by Regulation (EU) No 910/2014 (eIDAS), which took effect on 1 July 2016, an electronic signature creation device is software or hardware...
5 min read
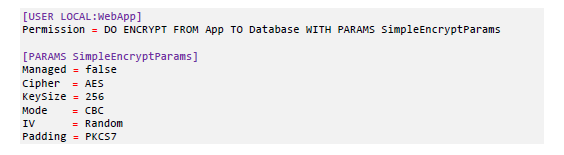
Today's businesses rely heavily on cryptography to authenticate people and processes, secure communications, and safeguard critical data.

3 min read
The last few years have been exciting for all stakeholders involved in the implementation and use of the eIDAS toolbox. Some important milestones...