3 min read
Thales Key Blocks and payShield HSMs: How They Work
 Martin Rupp (guest)
:
19. August 2021
Martin Rupp (guest)
:
19. August 2021
- Home >
- Thales Key Blocks and payShield HSMs: How They Work
Thales Key Blocks are an essential cryptographic key wrapping format. In comparison to other key block formats, they are proprietary and only work with Thales payShield HSMs. In what follows, we delve into detail about this key block format.
Description of the Thales Key Blocks Format
Thales Key Blocks are compatible with the X9.TR-31 format. They implement and extend it further by providing additional features.
The Payment Card Industry Security Standards Council (PCI SSC) requires that the retail banking industry implement ANSI X9.24/TR-31-compliant key blocks, however, TR-31 is a technical report, not a norm.
The ANSI standard defines “general” key blocks as structures with a header field, a payload field containing encrypted sensitive data (including the key itself), and an extra-field for checking the header’s integrity and the data.
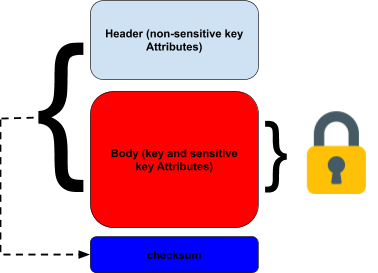
Illustration: a generic TR-31 key block
Based on this very generic scheme, it is possible to refine a TR-31 key block to add more features and sub-components.
Thales Key Block Structure
The Thales Block Structure defines four blocks instead of the three blocks defined by the TR-31:
- Header (16 bytes)
- Optional header
- Encrypted key data
- Authenticator
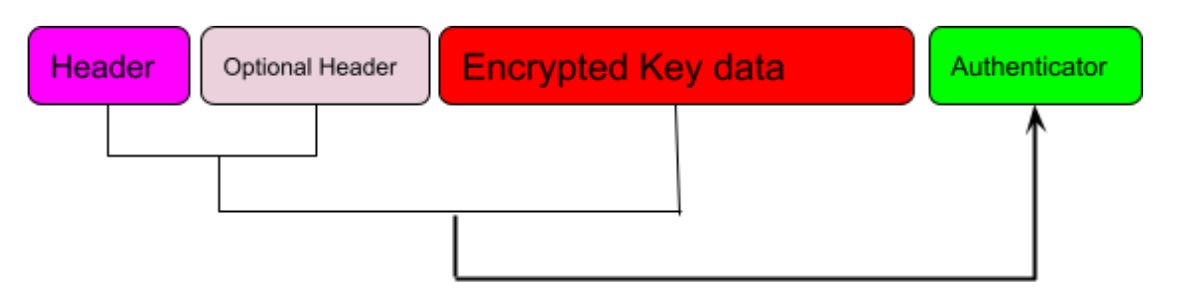
Illustration: Thales Key Block Format
The main difference is the addition of an optional header block that allows for more flexibility in key management. The header contains a field that registers the value of the Thales HSM Local Master Key (LMK) used for ciphering. Therefore, in theory, only Thales Key Blocks can only be used with Thales machines.
The header contains a field that informs if there are optional headers, and if so, how many there are. The optional header uses TLV (tag-length-value) encoding and is used for additional information that may vary in nature.
Here is a list of the optional headers typically permitted in a Thales Key Block.
|
Optional Header Blog Tag |
Usage |
|
KS |
Key set identifier |
|
KV |
Key block version values |
|
00 |
Status (T=Test, L=Live, etc.) |
|
01 |
Algorithm and mode used to encrypt the data block |
|
02 |
Algorithm and mode used to authenticate the data block |
|
03 |
Validity start date |
|
04 |
Validity end date |
|
05 |
Free usage (for information, etc.) |
|
PB |
Padding block |
Analysis of the Thales Key Block Format
Thales Key Block provides two types of key encryption: Triple DES and AES Keyblock LMK (e.g., encrypted by the LMK). In both cases, an Initialization Vector (IV) is used by taking bytes from the header, which as a result, directly binds the header and the encrypted key data.
For example, the Atalla Key Block uses all eight bytes of its header fields, while the Thales Key Block uses only a part of its header field for IV computation.
Any type of key specified in the header can be ciphered that way. The encryption is done exclusively in CBC mode, which can be a problem since CBC mode is not very resistant to some padding oracle attacks.
The encryption keys are derived from the HSM LMK (AES or Triple DES).
The authenticator part is used by computing a 3DES CBC-MAC or an AES CMAC from the ciphered data, the header’s concatenation, and the optional header. The keys used are also derived from the LMK.
Using Thales Key Blocks Format with Thales HSMs
 Because the Thales Key Blocks only work with payShields HSMs (payShield 8000, 9000, 10,000, etc), we must explain how to use them in this environment.
Because the Thales Key Blocks only work with payShields HSMs (payShield 8000, 9000, 10,000, etc), we must explain how to use them in this environment.
Only local keys are used to cipher the key blocks. Theoretically, this provides greater security.
Thales payShield supports multiple LMKs. This means that an HSM can be cryptographically separated into several groups to manage key blocks.
Thales Key Blocks, which can be created and maintained with Thales HSMs, typically include ZMKs (for exporting keys from one HSM to another), PMKs (PIN Master Key to cipher pin blocks), etc.
Centrally Managing Key Blocks with CKMS
Retail banking is becoming a more hybrid environment, with local data centres, HSMs, mainframes, and cloud infrastructures. Banks need to effectively manage key lifecycles no matter what HSM or location and guarantee a high level of payment security. Cryptomathic provides a banking-grade, PCI-compliant, and HSM-agnostic key management system called CKMS that, natively, supports all TR-31 implementations, including the Thales key block version. CKMS is able to deliver keys both automatically and manually to Thales payShields.
Using TR-31 key blocks, for external storage and transportation of keys is the modern way to go - having many advantages over the legacy methods (of using variants or simple encryption of keys). Thales have added their extensions to the design creating a more extensible solution and Cryptomathic have ensured that they can support this and all other implementations which is why we believe CKMS is the most adaptable solution on the market today.
Centralized, HSM-agnostic and cloud-ready key management - as offered by CKMS - allows for the effective use of resources, high security, and comfortable auditability for banks and financial institutions.
References and Further Reading
- More articles on Key Blocks (2019 - today), by Dawn M. Turner and Martin Rupp
- More articles on Key Management (2015 - today), by Matt & Peter Landrock, Stefan Hansen, Dawn Turner, and more
- Information Supplement: PIN Security Requirement 18-3 - Key Blocks (2019), by the PCI Security Standards Council