2 min read
Emulator Detection: Key for Mobile Banking & Payment App Security
Attacks on mobile banking and payment applications frequently begin with the use of an emulator for the mobile operating system, where the targeted...

2 min read
Attacks on mobile banking and payment applications frequently begin with the use of an emulator for the mobile operating system, where the targeted...

6 min read
The ever-growing number of applications and uses for mobile devices has long been a hot topic. Using mobiles to electronically sign transactions and...

2 min read
The European Union is leading the way in the move towards the creation of a single digital market. There are many advantages a digital business has...

6 min read
With the growing need for cryptography solutions to protect digital assets and communications, the ever-present security holes in modern computer...

2 min read
Microsoft’s Azure Key Vault Managed HSM allows customers to safeguard their cryptographic keys for their cloud applications and be...

3 min read
This article looks at some reasons for popularity of the IBM mainframe platform in the banking sector and touches upon its limitation for...

2 min read
A number of serious security vulnerabilities, collectively known under the names of “Meltdown” and “Spectre” [1][2], have recently been discovered in...

3 min read
The European Interoperability Framework (EIF) adopted in 2017 is the primary thrust in the EU’s effort to improve the efficiency of public service...
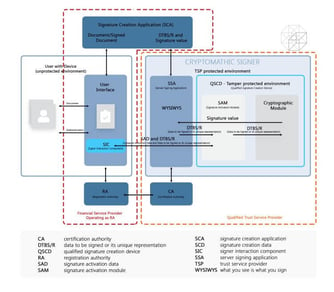
3 min read
The eIDAS regulation provides both the technical and legal framework for electronic identification and digital signatures that the banking sector...