3 min read
Optimizing eIDAS with Digital Signature Deployment Models
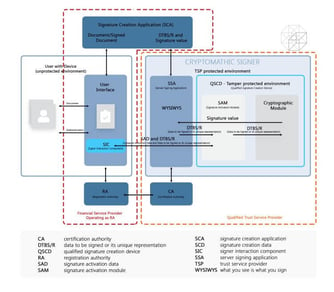
The eIDAS regulation provides both the technical and legal framework for electronic identification and digital signatures that the banking sector...
3 min read
The eIDAS regulation provides both the technical and legal framework for electronic identification and digital signatures that the banking sector...

4 min read
This article explains the four primary cloud KMS pattern combinations and which are best suited for use with Cryptomathic’s Key Management System...

3 min read
A study published in early 2018 by the European Union Agency for Network and Information Security (ENISA), revealed that 90% of the respondents...
3 min read
The PCI Council requires most actors of payment networks to implement ANSI X9.24/TR-31-compliant key blocks to wrap and securely transmit, transfer,...

2 min read
User interface design and usability are the deciding factors in attaining a good user experience for most IT deployments, including key management...

3 min read
Bring your own key (BYOK) is a popular term relating to key management for cloud applications. However, a lack of standardization makes it confusing...

3 min read
Banks continue to feel the profound transformational effects that digital technologies have on their business. This can be seen in the creation and...

4 min read
This article discusses how tokenization may reduce false declines with credit card transactions that could negatively impact merchants.

3 min read
A crypto-abstraction layer (CAL) is, in its most general sense, an application programming interface (API) - also known as a library- that hides...