5 min read
BYOK for Google Cloud Unlocks Opportunities for Financial Institutions
 Ulrich Scholten (guest) & Stefan Hansen
:
02. March 2021
Ulrich Scholten (guest) & Stefan Hansen
:
02. March 2021
This article discusses the concerns surrounding key management for cloud environments and how Cryptomathic addresses them by bringing banking-grade cryptographic key management to the Google Cloud - in the context of a hybrid-cloud banking architecture.
The Rationale
In a process of digital transformation and the platformization of service offers, banks and financial institutions are increasingly migrating IT services from on-premise, self-managed data-centers to public cloud services.
With the promise of lower capital costs to improve bottom lines, there are definitely significant advantages to embracing the native elasticity and resilience that cloud computing can bring to the banking and financial sector. These advantages align well with modern goals for rapid and agile development and delivery of products and services, to differentiate banks and others from their competition.
However, for many business-critical financial applications, security concerns are the largest barrier-to-adoption for cloud computing. The aggregation of sensitive data, critical business processes, and other corporate IP on a publicly-accessible platform may open flanks to cybercriminals as well as inadvertent exposure of critical data to third parties. Professional design and management of data security is vital.
Challenges
Cryptography is the security foundation for any significant application - to protect data and communication and to authenticate processes and people. For many banking applications, their core value is actually delivered through cryptography:
- Banking and financial transactions are ultimately composed of cryptographic functions
- Ownership of a set of cryptographic keys completely defines a bank’s online existence
Most organizations strongly rely on cryptography for their digital business, however, banks and financial institutions have a specific interest in high-assurance cryptographic processes, as any compromise can lead to fraud that can directly divert funds into attackers’ accounts.
Data Security and Privacy
With the decision of placing sensitive data in the Cloud, the data security and privacy assurances depend, to a certain extent, on the hosting company. The software and hardware infrastructure (IT architecture), the level of physical protection of the IT architecture and its perimeters (physical infrastructure), as well as the personnel involved and their security-related processes (procedures) are all critical considerations.
In a hosted environment and without specific precautions, this is out of the banks’ control, data may be exposed to personnel at the hosting provider or to third parties (without the bank’s knowledge).
Vendor Lock-in
The cloud service provider could handle the protection of data and communication. However, this could lead to a sticky lock-in situation if the cloud infrastructure provider owns the data encryption keys. Any future switching of providers could be difficult and potentially lead to data loss or tedious migration procedures. Lock-in needs to be avoided.
Hybrid-Cloud
It is unlikely that a bank can limit its totality of operations to one cloud location. The bank may want to use the Google Cloud for storage or even for applications, the MS Azure cloud to operate MS Dynamics and Office 365, and the SAP cloud to use management applications in the context of the HANA environment. This brings about the dilemma of key ownership. This challenge grows even more complicated when adding SaaS provided by different service providers on one or more cloud service platforms to the mix. In addition, the local data-center will be needed for on-premise services. Data transit must not be limited by distributed key management or key ownership.
Auditability and Compliance
A major challenge for the finance and banking sector is its high level of regulation. Within annual audits, banks need to provide proof of compliance to security standards (e.g. PCI DSS). It can be tedious or impossible for the audited organization to demonstrate compliance when the cryptography and keys are out of their control. But successful audits are prerequisite for the banking license and hence mandatory.
Harness Google’s Cloud Advantages
The silver bullet will be to benefit from Google’s Cloud hosting advantages without suffering under the imperfections of cloud hosting. This is where BYOK, offered by Cryptomathic CKMS, comes into the picture.
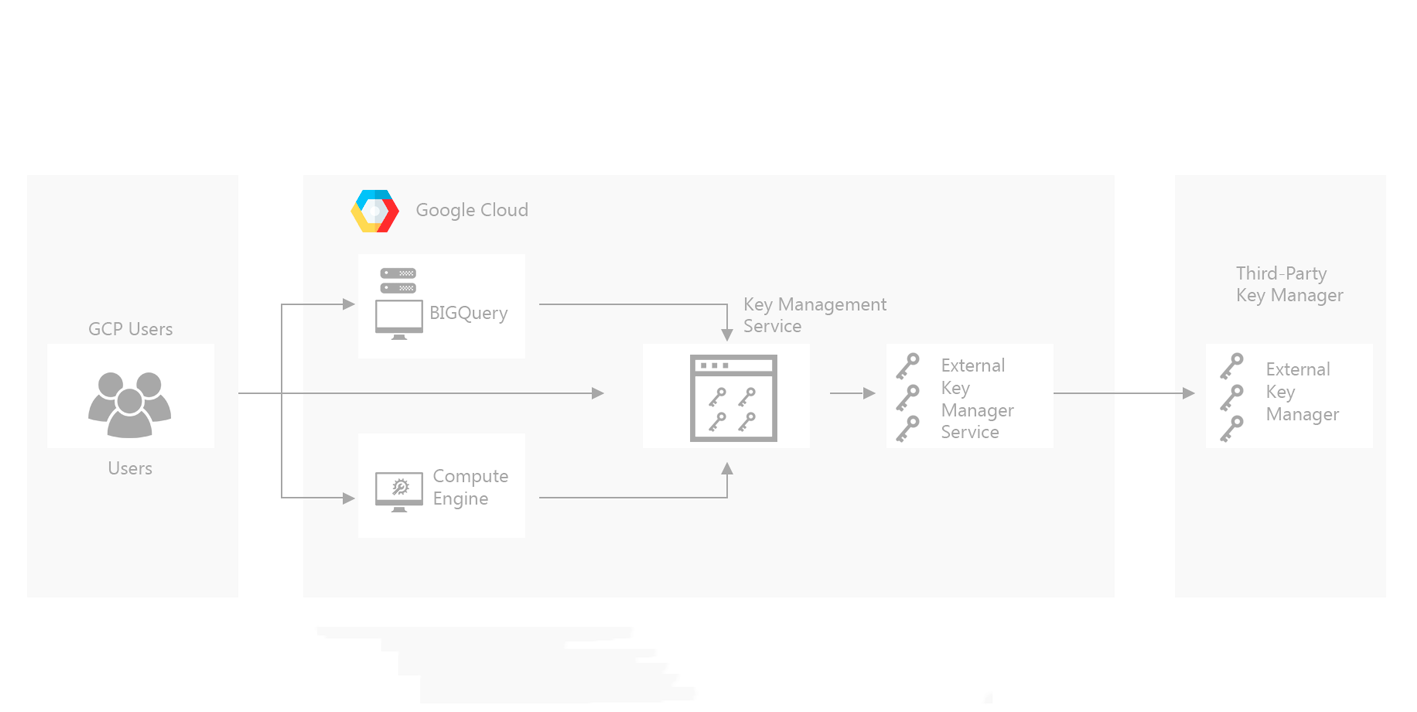
BYOK for Google’s Cloud Key Management
To keep customer data safe, Cryptomathic CKMS seamlessly integrates with the Google Cloud for a centralized key management approach, operating as an external key management system for the Google Cloud.

This banking-grade solution builds on the industry-standard AES-256 which Google uses for bit encryption to protect customer data in its cloud. This is a reliable and banking-compliant standard. It allows Cryptomathic to create a secure and continuous cryptographic architecture spreading from the bank to the Google Cloud.
To provide banks with control over managing their data security, Cryptomathic uses the “bring-your-own-key” approach, which further enhances Google’s already hardened encryption framework.
By choosing the BYOK option, the bank exclusively owns and controls their encryption keys. The user (banks):
- Creates and maintains possession of their keys.
- Determines when their data is active or at rest.
- Restricts anyone inside or outside of Google from accessing their rest data without holding possession of the user’s keys.
- Maintains the control to move data and applications across a secured hybrid cloud.
With the BYOK option, Google does not retain the user’s keys. Instead, Google only holds them long enough to complete the user’s request.
.png?width=1920&name=Cloud-EKM-providing-bridge-between-KMS-and-External-Key-Manager%20(1).png)
Benefits of Using Google Cloud with Cryptomathic CKMS for BYOK
The Google Cloud security architecture and Cryptomathic’s BYOK integration gives banks full control over their data's encryption within the public cloud. BYOK provides the following benefits:
- Added peace of mind. Google cloud already encrypts user’s cloud data using AES-256, the industry’s leading stand. Since Google does not retain users’ BYOK keys, it cannot decrypt or read their data at rest.
- Comprehensive security solution. The bank’s BYOK encryption keys cover all types of data at rest, including boot and data persistent disks, which are not covered by all solutions.
- Quicker without the added overhead expense. Since the Google Cloud already encrypted users’ data at rest, the BYOK option provides banks with more control without the additional overhead that normally would result.
- Included free with Google Cloud. Google does not charge more for users who choose the BYOK option.
Banking-Grade Key Management in a Hybrid-cloud Environment
The services on the Google Cloud can be interwoven with services and data of in-house provenance, from external sources through the PSD2 API or from MS Dynamics and the integrated ecosystem partners.
Services and data can be integrated into composite new competitive value propositions, services and evolve gradually, guided by customer requirements and market demand.
Of overall importance is the flexibility and agility of the crypto key management architecture. Key lifecycle management needs to be automated and central, to be auditable and to keep banks in control.
Data and applications might need to change the hosting location, e.g., move from Cloud to local data-center or across different cloud platform providers. It would be undesirable with a cloud service vendor having a stake in the bank's service strategy.
Cryptomathic’s Crypto Key Management System (CKMS) delivers automated key updates and distribution to a broad range of applications across the hybrid Cloud. CKMS manages the entire lifecycle of all keys (symmetric and asymmetric), supports robust business processes and allows you to confidently comply with and pass internal & external audits. It operates as an external key management system to cloud environments, bringing banking-grade security and compliance to the Google Cloud.

CKMS has integration points to many cloud applications like MS Azure or Amazon AWS and integration points to all leading HSMs and IBM Common Cryptographic architectures. More than 2 decades of experience in the banking sector makes Cryptomathic and its CKMS the reliable and risk-free partner for any digital transformation process across the hybrid cloud.
References and Further Reading
- Selected articles on Bring Your Own Key (2017 - today), by Matt Landrock, Stefan Hansen, Ulrich Scholten and more
- Cloud Threat Report 2020 (2020), by Oracle Corporation & KPMG International Limited
- Selected articles on Key Management (2012-today) by Ashiq JA, Dawn M. Turner, Guillaume Forget, James H. Reinholm, Peter Landrock, Peter Smirnoff, Rob Stubbs, Stefan Hansen and more
- Selected articles on Key Management in the Cloud (2017-today) by Edlyn Teske, Matt Landrock, Rob Stubbs, Stefan Hansen, Ulrich Scholten, Joe Lintzen and more
- Key Management in a Multi-Cloud Environment - A blessing or a curse? (2017), by Johannes “Jo” Lintzen
- Buyer’s Guide to Choosing a Crypto Key Management System - Part 1: What is a key management system (2018), by Rob Stubbs
- Buyer's Guide to Choosing a Crypto Key Management System; Part 2: The Requirement for a Key Management System (2018), by Rob Stubbs
- Buyer’s Guide to Choosing a Crypto Key Management System - Part 3: Choosing the Right Key Management System (2018), by Rob Stubbs
-
NIST SP800-57 Part 1 Revision 4: A Recommendation for Key Management (2016) by Elaine Barker
-
CKMS Product Sheet (2016), by Cryptomathic
