3 min read
Key Management Strategies for SaaS: Avoid the pitfalls in the Cloud
This article discusses key management strategies for the SaaS cloud model, and unique security problems to be dealt with because of lack of user...

3 min read
This article discusses key management strategies for the SaaS cloud model, and unique security problems to be dealt with because of lack of user...
4 min read
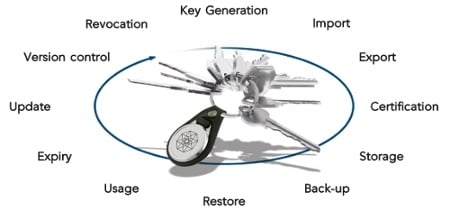
Typical Services Provided by Key Management Systems Key management is the administration of tasks involved in all aspects of cryptographic key usage...