3 min read
eIDAS Regulation & European Interoperability Framework Explained
The European Interoperability Framework (EIF) adopted in 2017 is the primary thrust in the EU’s effort to improve the efficiency of public service...
Enjoy expert insights into the latest innovations and talking points from the world of cryptography.

3 min read
The European Interoperability Framework (EIF) adopted in 2017 is the primary thrust in the EU’s effort to improve the efficiency of public service...
3 min read
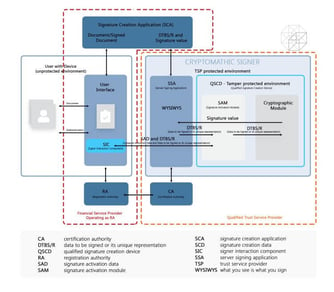
The eIDAS regulation provides both the technical and legal framework for electronic identification and digital signatures that the banking sector...

4 min read
This article explains the four primary cloud KMS pattern combinations and which are best suited for use with Cryptomathic’s Key Management System...

3 min read
A study published in early 2018 by the European Union Agency for Network and Information Security (ENISA), revealed that 90% of the respondents...

2 min read
User interface design and usability are the deciding factors in attaining a good user experience for most IT deployments, including key management...

3 min read
Bring your own key (BYOK) is a popular term relating to key management for cloud applications. However, a lack of standardization makes it confusing...

3 min read
Banks continue to feel the profound transformational effects that digital technologies have on their business. This can be seen in the creation and...

3 min read
Hardware Security Modules (HSMs) are used in all card payment systems (as well as various other applications that require strong security) to protect...

3 min read
As part of the global drive for digital transformation, legally binding digital signatures are at the forefront of many businesses’ ambitions to...