- Home >
- Solving Common Mobile Banking Security Issues
An investigation conducted by "Which?", a consumer watchdog group based in the UK, found serious vulnerabilities in the security of banking security systems, including mobile banking apps. The investigation was a cooperative effort between Which? and independent security experts 6point6. It scrutinized the deficiencies in banking systems that could give scammers and cybercriminals unauthorized or unwitting access to customers’ funds and accounts. This article suggests comprehensive and dynamic security solutions for banking apps.
Top Mobile Banking App Security Issues
While most large banks have implemented mobile app security measures, some have not fully stepped up. Some of the top mobile banking app security issues include:
- Failing to block users from logging into banking websites from two different computer networks (e.g. two different Wi-Fi networks or a Wi-Fi network and cellular network at the same time).
- Failing to log out users when they switch to other apps or use forward/back buttons to leave their banking session and return to it.
- Not meeting the latest regulations for strong customer authentication (SCA) during login processes to prevent unauthorized access to users’ accounts.
- Not implemented at a minimum, two-factor authentication for both mobile and internet banking users.
- Failures in authentication checks that allow users to bypass these checks upon login if they designate their device as “trusted”.
- Not implementing limited functionality protocols that prevent users from changing sensitive information via mobile apps.
- Making it too easy for a user to recover their account number via their app by requiring only basic details to authenticate the user’s identity, such as basic pre-set security questions for forgotten passwords.
- Failing to alert users when passwords are changed.
- Failing to allow users to use special characters in their passwords.
- Not providing sufficient code obfuscation that could allow hackers to steal sensitive information or identify weaknesses within the app.
- Failing to perform root and emulator detection that can expose banking apps to security weaknesses.
Digital Transformation: Good or Bad for Banks Security?
Using cutting-edge technologies, the rise of mobile banking apps has helped fuel the trend of the banking industry’s digital transformation. A recent digital banking report from Business Insider concluded that 89% of users surveyed use mobile banking, while 70% use it as their primary means to access their banking accounts.
Both banks and their customers benefit from the digital transformation trend. Much of the distrust toward mobile banking has dissipated thanks to better user experiences and, of course, improved security strategies and tools. Unlike other industries, the development of mobile banking apps requires adhering to stringent security regulations and processes.
Securing data with mobile banking apps is often a complex issue because of three major factors:
- Internal business processes
- Software security measures
- User behavior
Often, when there is a failure in one factor, the other two cannot effectively compensate. This is where the likelihood of a security breach is further increased. However, with well-rounded and robust security controls that encompass all three factors, these breaches can be avoided.
Keeping Cybercriminals at Bay Through Banking-grade App Security Controls
Despite the fact that users should never share their usernames and passwords, we do not advocate client “education” as a significant security mechanism. This will never bring sufficiently secure protection. Apps will only remain secure if the procedures and technologies are highly failsafe and even protected against involuntary faulty operations by the client.
Logging into public Wi-Fi hotspots when using their banking apps will always be a typical scenario, even though such networks are not secure. The always-on millennials will not wait until they go home to connect to their secured Wi-Fi. Accustomed to logging into local speedy Wi-Fi, they won't use the app exclusively while connected to their cellular network to protect their personal information. They will not compromise on user experience. The app shouldn't either.
Secure Distribution and Secure Enrollment
Channeling customer activities helps reduce some of the security risks related to mobile banking. Featuring the app’s link to the app stores on their website helps banks direct their customers to their official app instead of a counterfeit one. Secure enrollment is a second “must”, no matter from where the customer signs up. The App, Infrastructure and Backend shall allow for this. Continuous checks for APP Integrity from the Bank’s backend and careful monitoring of device health will add an additional supervision layer.
Secure Communication
The communication between the app and the back-end server must be secure to protect the data being sent and to ensure the app only communicates with the intended system. Securing communication channels can involve several mechanisms, including protection for access tokens and cookies, encrypted transport protection (HTTPS) and HTTPS tunneling, and additional mechanisms to authenticate both the mobile device and the back-end system.
Secure Authentication
Secure communication begins with authentication. Using multi-factor authentication (MFA) adds security over two-factor authentication by adding features like biometric protection, secrets, and certificate pinning. The latter will only be “banking-grade” and protected against tampering if the back-end provides managed certificate whitelisting and an automated certificate life-cycle management, along with very short certificate life cycles.
Such a solution relies on hardware security modules in the backend to create, host, and manage the certificates. This prevents access to certificates by third parties, even if they intrude on the heart of the banking infrastructure. The environment should be crypto-agile by default. Meaning that when new standards or policies emerge (e.g. driven by recent breaches) and should be able to evolve rapidly. Automated continuous checks from the backend, tunneling, etc. will round up the secure communication.
Secure App Design
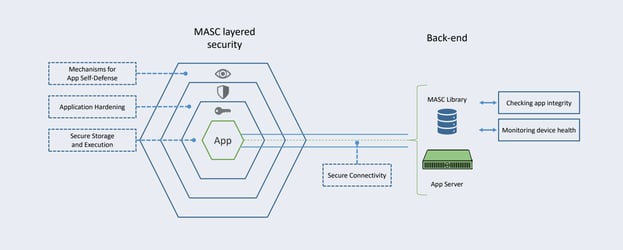
Mobile apps often provide open flanks to cyber criminals. Three approaches to repel hackers are:
- Active Mechanisms for the App’s self-defense
- Application Hardening
- Secure Storage and Execution
Methods to detect tampering attempts in the app, especially by debuggers, simulators, and emulators should be considered. Malevolent physical access to the device and app should also be prevented. Finally, this security layer should be able to detect the rooting or jailbreaking of the device and respond accordingly. All monitoring and health checks should be integrated with the banking backend and fraud systems.
Application hardening mechanisms should be employed to make the app difficult to attack or modify. This includes obfuscating the source code of the application and especially, the relevant data and constants that are used to connect to servers.
Secure storage and key protection is the third pillar in secure app design.
The app must be able to efficiently protect the various cryptographic keys by preventing their possible recovery by an attacker. Usage of secure storage, such as using a secure element or SIM card, should also be offered if possible. Otherwise, this can be achieved with dedicated obfuscation methods.
Cryptomathic Helps in Developing Secure Mobile Banking Apps
 Often, app development is conducted by banks in conjunction with app development companies. The experience and focus are set on user experience and app performance.
Often, app development is conducted by banks in conjunction with app development companies. The experience and focus are set on user experience and app performance.
Designing the security infrastructure for banks is a demanding task. Errors committed during the App design phase cannot be eliminated at a later stage.
To fill that void, Cryptomathic brings extensive experience in banking-grade security, providing a security software development kit (SDK) for banking apps (Android and iOS).
Cryptomathic MASC consists of multiple layers of complementary defense mechanisms and smartphone app security components. This enables app developers to focus on developing user-friendly business applications while leaving the critical and specialist security-related parts to MASC.
Cryptomathic MASC is built upon an evolutionary security framework that is designed to protect against the ever-changing threat landscape. MASC protection measures are constantly being refined and updated (along with the standard mobile app updates) to remain resistant and resilient to both known and unknown attacks.
Going beyond pure app protection, MASC forms the bridge between the App itself, the communication channel and the banking backbone, providing protection for the complete mobile banking process.
Getting the Apps Protected
Knowing where deficiencies lay in banking security systems, especially with mobile banking apps, and how they can be prevented can help banks and their customers avoid falling prey to cybercriminals. Adhering to security standards and implementing strong security policies, including cryptographic tools, helps you solve mobile banking app security issues. It greatly reduces the risk of most security gaps banks and their customers may encounter with mobile banking apps.
Cryptomathic MASC provides a comprehensive and dynamic protection environment helping app developers and banks alike. MASC is a proven solution and has protected banking apps since 2013.
References and Further Reading
- Read more articles about application security for mobile banking applications (2018 - today), by Martin Rupp, Stefan Hansen and more
- Which? investigation finds worrying gaps in bank security systems (January 07, 2021), by Finextra
- Which? Banking Security and Payment Methods (Retrieved February 03, 2021)
- State of mobile banking in 2020: top apps, features, statistics and market trends (2019), by Alicia Phaneuf
- MASC Mobile App Security Core (2019), Web page by Cryptomathic
- PCI Mobile Payment Acceptance Security Guidelines for Developers version 2 (September 2017), by the Emerging Technologies, PCI Security Standards Council