2 min read
Key Blocks in ANSI X9.24-1-2017: An Introduction
 Martin Rupp (guest)
:
modified on 18. February 2020
Martin Rupp (guest)
:
modified on 18. February 2020

- Home >
- Key Blocks in ANSI X9.24-1-2017: An Introduction
Key Blocks have been invented as a standard way for protecting the integrity of symmetric cryptographic keys and for identifying what the keys can be used for. Key Blocks are used to protect Triple-DES keys (Key Blocks can be used as 3DES key bundles), but also AES keys (often using AES key wrapping).
The Atalla Key Block format historically paved the way for Key Blocks and led to general standards, including the one we’re studying (ANSI X9.24-1-2017) and the ASC X9 TR 31-2018 (which describes a possible implementation of an ANSI X9.24-1-2017-compliant key block).
The Motivation behind Key Blocks
Key Blocks are an important method to help protect payment security. They prevent the misuse of cryptographic keys and protect the keys from malevolent hackers who could exploit weaknesses and substitute other keys- and perform similar attacks against payment systems. 3DES key bundles are one possible use of key blocks.
They prevent the re-arrangement of 3DES keys that could allow an attacker to crack a 3DES cipher by attacking two separate individual DES ciphers.
Key Blocks as Described by the ANSI X9.24-1-2017
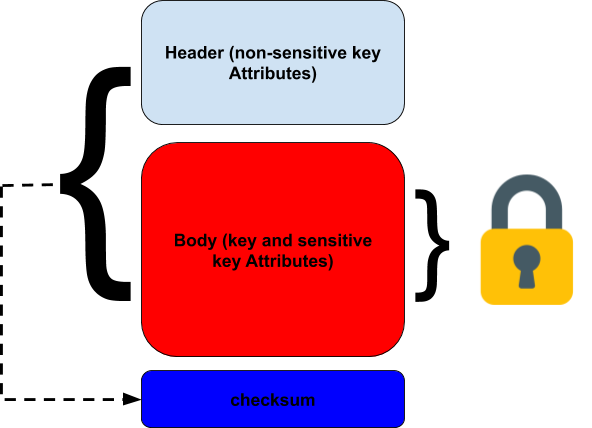
The ANSI standard defines “general” key blocks as a structure that provides a key with a header field containing non-sensitive data and a payload field containing encrypted sensitive data (including obviously the key itself). The integrity of the header plus the payload must be checked by adding an extra field. It must not be possible to change anything in the header or payload without modification of the integrity check data.
There is an important leeway in the construction of the header field that contains the non-sensitive key attributes. The sensitive key attributes, contained in the encrypted payload may contain information such as the ciphering mode, cleartext key length, etc.
The integrity mechanism can be a MAC (Message Authentication Code), a signature using RSA for example, or an integrity mechanism from a key wrap.
A very important restriction is that the Electronic Code Book mode SHALL NOT be used to encrypt this [a given] field if the field is longer than one block. This is because of the AES-ECB known ciphertext / plaintext attack and frequency analysis in such cases that allow a possible deciphering of one block.
Acceptable cipher modes are, according to the standard:
- Cipher Block Chaining (CBC);
- Counter with CBC-MAC (CCM);
- Counter with CBC-MAC (CCM);
- AES Key Wrap.
Note that while there is a wide range of mechanisms available for integrity checks, the encryption itself of the sensitive information (including the key) must be performed only by Triple-DES or AES.
Summary
ANSI X9.24-1-2017 defines Cryptographic Key Blocks as a very important and critical aspect of symmetric key encryption techniques in the context of Retail Financial Services. The definition of Cryptographic Key Blocks by the standard is very rigorous and requires a strict implementation. It is also worth noting that some PCI requirements are now migrating towards the use of key blocks, such as TR-31.
To support the broadest range of integrations with applications, Cryptomathic's CKMS supports a range of proprietary and standardized ‘Key Block’ formats. These define, at bit level, the formats expected for keys to be exchanged with different systems.
Supported formats include.
- Atalla Key Block
- BASE24 Key Exchange
- IBM CCA
- MasterCard OBKM
- PKCS#8 Cryptogram
- TR-31
References, Side Notes and Further Reading
- Read more articles on the ANSI X9.24-1-2017 (2018 - today), by Martin Rupp, Matt Landrock and more
- ANSI X9.24-1-2017 - Retail Financial Services Symmetric Key Management Part 1: Using Symmetric Techniques (2017), by the Accredited Standards Committee X9 (Incorporated Financial Industry Standards), American National Standards Institute
- ASC X9 TR 31-2018 - Interoperable Secure Key Exchange Key Block Specification (2018), by American National Standards Institute (ANSI)