3 min read
The Importance of Banking-grade Key Management for IBM CCA
 Martin Rupp (guest)
:
12. August 2022
Martin Rupp (guest)
:
12. August 2022

The IBM Common Cryptographic Architecture (CCA) is a cryptographic platform providing several functions of special interest for securing financial transactions.
The CCA is commonly found in systems handling ATMs. It is important to be able to exchange keys with a system running CCA. CCA supports the management of DES keys using TR-31.
This article provides an overview of IBM CCA and explains why a banking-grade key management system must be able to support the IBM CCA key format.
IBM CCA as part the banks' portfolio of integration points
In our article “End-to-End Banking-grade Key Management - from on-premise to multi-cloud BYOK”, we introduced vital integration points for financial institutions related to cloud environments, applications and infrastructure.
Integration points bundle together the relevant aspects to consider in a crypto process when integrating a key management system into a banking infrastructure.
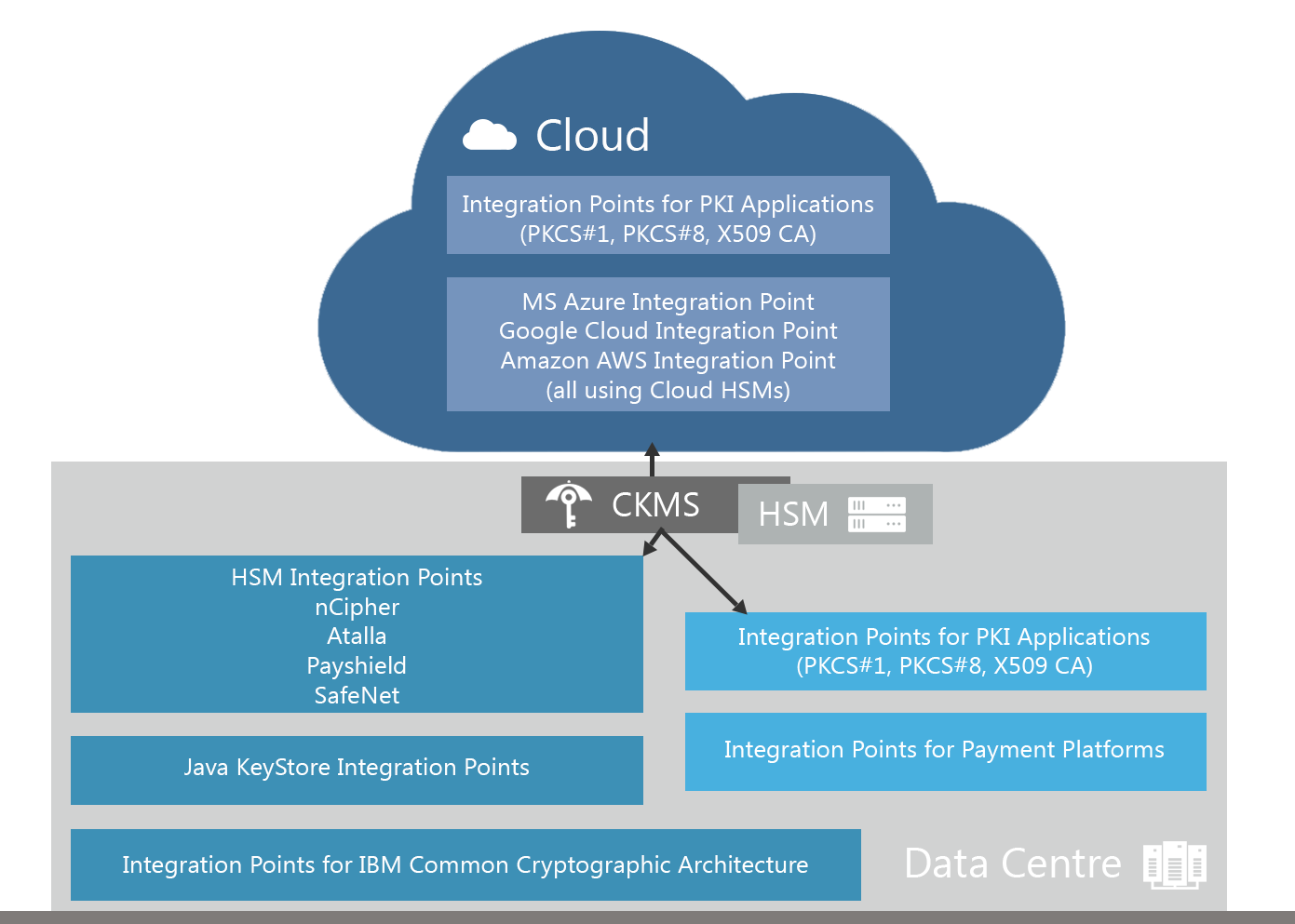
A traditionally important set of integration points relates to the IBM CCA. IBM mainframes play an important role in the banking infrastructure as market-leading infrastructure related to the management of ATM-based transactions.
Although ATM-based withdrawals proportionally lose share in the banks overall portfolio of transactions, it plays an important role in absolute figures. Also, these mainframes are a pillar of virtually every bank’s legacy infrastructure.
Overview of the IBM CCA key format
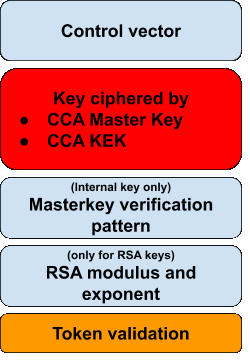
In the CCA format, a key token is a data structure that contains information about a key. It contains a key or several keys. It is the equivalent of a TR-31 key bundle data structure.
CCA keys use control vectors similarly to the ‘attribute field’ of a typical TR-31-‘compliant’ key bundle. In CCA, a control vector is a public data structure that details the permissible usage for an associated key.
When a CCA DES key is encrypted, the key-encryption key is bundled with the control vector through an exclusive XOR operation in order to form the actual key used in the DES key-encryption process.
The CCA control-vector key-typing scheme and the command authorization and control-vector checking performed by a CCA node jointly provide an important defense against misuse of keys and related attacks, comparable to the key bundling mechanism in the TR-31 scheme.
CCA tokens can be used to manage DES or RSA keys. Their operation is way more complex than a key bundle, which is implementing only minimal fractions of TR-31. They are used in many cryptographic devices such as the IBM 4758 Crypto Processor and operate in the processing of financial transactions.
IBM key tokens are divided into two distinct categories:
- internal key tokens and
- external key tokens.
An internal key token is bound to the cryptographic hardware that generates it, because the value of the key itself is encrypted with the co-processor master key.
An external key token does not use a master key bound to a CCA. It makes use of a CCA transport key and a key encryption key (KEK).
Both internal and external keys contain equivalent components to TR-31 key bundle data structures:
- The key encrypted with the CCA Master key or the CCA KEK / transport key
- The control vector (public)
- A Token validation value, used to ensure the integrity of the whole key token
Additionally, an internal CCA key token contains a master key verification pattern used for identification of the Master Key register. If the Key Token wraps an RSA key, then the modulus and exponent are also included in an additional field of the data structure in both cases.
Why a banking-grade key management system must support the IBM CCA format
An organization which deals with architectures using IBM mainframes and/or IBM 4758 devices, must be able to import and export CCA key tokens to and from other formats, especially any TR-31 compliant key block.
 Such a translation is not easy and requires specialized knowledge. Many banks and financial services organizations that operate ATMs and process card transactions will still have IBM mainframes in use for their payments processing infrastructure. It is, therefore, crucial that any key management system that is implemented for such businesses needs to support the IBM CCA format in order to efficiently manage the lifecycle of the keys that are required to secure payments and other confidential data.
Such a translation is not easy and requires specialized knowledge. Many banks and financial services organizations that operate ATMs and process card transactions will still have IBM mainframes in use for their payments processing infrastructure. It is, therefore, crucial that any key management system that is implemented for such businesses needs to support the IBM CCA format in order to efficiently manage the lifecycle of the keys that are required to secure payments and other confidential data.
Of course custom solutions are possible: like having development teams producing “converters” from one format to another in order for their systems to deal with key management software that is unable to understand such a format. But this comes at the price of a potential high security risk factor, the loss of flexibility and crypto-agility.
Tools for securely storing and accessing secrets in the Cloud such as Azure key vault, Amazon KMS or Google Cloud Key management are by design unable to manage the IBM Common Cryptographic Architecture tokens, as they are confined to only work with applications that are deployed in the same cloud. Data-centers can neither be accessed nor managed.
It is important that the crypto infrastructure in financial institutions can control the entire lifecycle of keys while maintaining compliance to international banking regulations and PCI standards.
This includes its ability to understand and manage IBM CCA key Tokens.
References
- Selected articles on Key Management (2012-today) by Ashiq JA, Dawn M. Turner, Guillaume Forget, James H. Reinholm, Peter Landrock, Peter Smirnoff, Rob Stubbs, Stefan Hansen and more
- Selected articles on Key Management in the Cloud (2017-today) by Matt Landrock, Rob Stubbs, Stefan Hansen, Ulrich Scholten, Joe Lintzen and more
- Selected articles on IBM Mainframes in Banking Infrastructure (2019-today) by Martin Schmitt and more
-
NIST SP800-57 Part 1 Revision 4: A Recommendation for Key Management (2016) by Elaine Barker
- CKMS Product Sheet (2016), by Cryptomathic
-
White Paper – Deploying CKMS Within a Business (2017), by Cryptomathic
- Digital Bank: Strategies to launch or become a digital bank Kindle Edition (2014), by Chris Skinner