- Home >
- Microsoft Banking Accelerator with On-Prem Key Management
The cloud services provided by Microsoft Dynamics 365 are gaining rapid market share in the banking world. A burning question for the security departments is how to take advantage of the cloud services on offer without relinquishing control of their cryptographic keys.
Here we look at some of the benefits offered by MS Dynamics cloud services and how an on-premise key management system should integrate with the Azure Key Vault (or other cloud platforms) to retain control of the lifecycle of cryptographic keys and maintain compliance to banking regulations.
Microsoft’s expansion into banking cloud services
During the last years, Microsoft imposed minimal ramp-up costs and barriers to the cloud, being already present in many banks with Office 365 applications. So instead of requiring disruptive procedural change, Microsoft had the possibility to gradually increase its presence with more apps, deployed with standard policies and as a registered vendor in the legal and purchasing departments.
Also being one of the top 3 cloud service providers supported Microsoft’s success story.
Using the MS Dynamics platform allows a bank to make use of many external applications like analyzing latent potential, seizing opportunities, predicting future behavior or proactively recommending services on user profiles. The external applications are seamlessly integrated in the MS Dynamics Ecosystem.
The MS Banking Accelerator
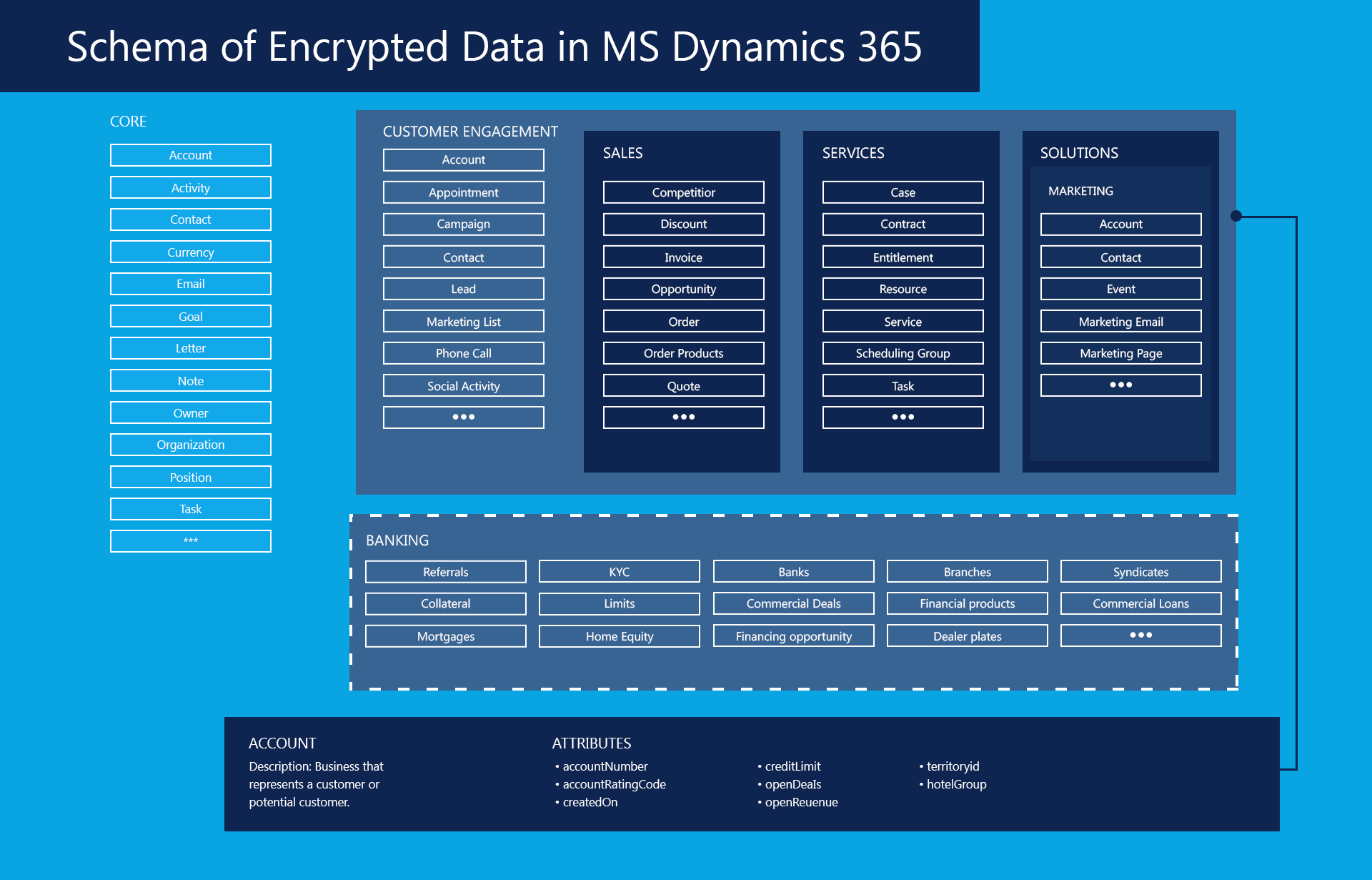
Microsoft extended its proven concept of the Common Data Model (modeling data structures across various business areas into one holistic and integrated concept) to the banking world. The Common Data Model, for banking-specific data, models data structures across both Retail and Commercial Banking, with entities including Know Your Customer (KYC), loans, mortgages, referrals, branch details, credit facilities, commercial deals, syndicate banks and more.
Source: Microsoft
Benefits for the Banks - easy integration and availability of proven data models
Banks have easy access to the proven data structures and can even use templates to model their applications. In consequence available data can be used to generate customer specific offers in a comfortable way .
The bank can orchestrate rapid service innovation, creaming off the best that is available
- Inside the bank’s data center
- Via PSD2 APIs
- Within MS Dynamics
- Within the Dynamics Ecosystem (and instantly available through MS Dynamics) including mobile applications
The good news is that once signed up to Dynamics, no new policies or contractual things need to be coordinated with the legal or purchasing departments. It is just business as usual, most certainly in the responsibility of the concerned managers within their budgetary scope of manoeuvre.
In consequence, the Lego bricks to build the financial service platform are instantly available. It is now up to the bank to create their specific value propositions.
Encryption in MS Dynamics for Banks
MS dynamics uses MS SQL Server Cell Level Encryption (Field-level data encryption) for default entity attributes which contain sensitive user information (e.g., username or passwords) in compliance with FIPS 140-2.
The bank’s security administrator can activate / customize data encryption.
No matter, which applications the bank runs, encryption applies to
- Data at rest in the database (on MS Azure)
- In transit between user devices or between the Microsoft data centers (e.g. during synchronization)
- Public endpoints through TLS.
For end-to-end banking-grade encryption and key management, the main characteristics needed are:
- Consistent encryption policies, and manageable from one central control center
- Auditable and compliant with data protection and banking regulations (PCI-DSS, FIPS 140-2, CC, PSD2, GDPR)
- Flexible and supporting easy and unhampered orchestration of services
- Universal over system boundaries including IBM mainframes and other legacy architecture
- Automated Bring Your Own Key (BYOK)
- Comfortable and Automated “Manage Your Own Key” (MYOK) in the frame of banking grade key lifecycle management
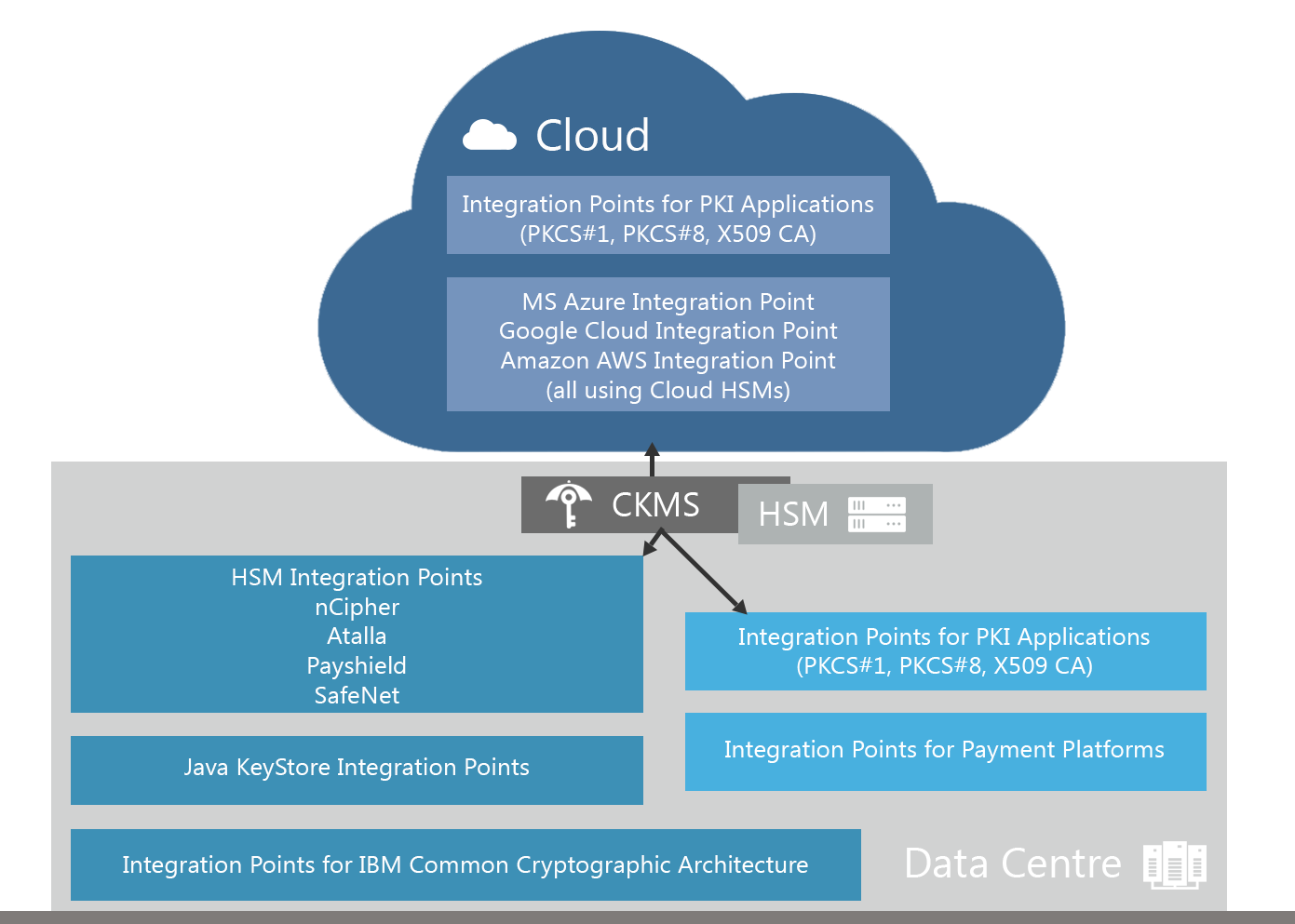
Hybrid cloud model: CKMS in the data center with multiple integration points
Comfortable BYOK and Key Lifecycle Management with Cryptomathic CKMS
Cryptomathic’s Crypto Key Management System (CKMS) integrates with the MS Azure Key Vault for automated BYOK. The Key Vault is the underlying central storage place for key and certificate management for applications (such as MS Dynamics) within the MS Azure environment. Keys are stored in FIPS 140-2 compliant HSMs.
From CKMS, located within the bank’s datacenter, the bank can securely bring their keys and manage the lifecycle of these keys for use within the MS Dynamics landscape.
At a high level, this process is straightforward:
- Keys are generated in the bank’s on-premise key management system, CKMS.
- The keys are then encrypted with Key Encryption Keys (KEKs), and passed to the Azure Key Vault. Keys are never unencrypted outside the HSMs.
- After decrypting the keys inside the Key Vault’s HSMs, only these HSMs can use the keys.
- Banking data is bound to certain regions. For instance European user data must not leave the European area of jurisdiction. To ensure this, Microsoft uses KEKs destined to specific regions. In consequence, e.g., keys from EU users cannot be decrypted or used in data centers outside the EU.
Microsoft does not have access to unencrypted data or passwords. So information stays solely in the hands of the banks. If the bank decides to change the vendor (e.g. change from the Microsoft Banking software to the SAP version), there is no vendor lock-in. The bank is free to change.
If data from the Dynamics world is required for on-premise applications (e.g., the bank’s homegrown applications), the encrypted data can be transferred from MS Azure (where it rests) to the local data center. With the locally available keys, the data can be decrypted in an automated process and used seamlessly.
By integrating CKMS with the MS Azure Key Vault, Cryptomathic provides an all-embracing banking-grade key management infrastructure compliant with banking standards. This enables the bank to position itself as a customer-oriented financial service platform across technical boundaries from the local data center to the cloud.
References
- Read more articles about secure banking-grade key management of MS-Dynamics (cloud or on premise) together with other cloud or datacenter applications (2019 - today), by Stefan Hansen, Ulrich Scholten and more
- Encryption in Microsoft Dynamics 365 (retrieved May 2020), by Microsoft Corporation
- Import HSM-protected keys to Key Vault (retrieved May 2020), by Microsoft Corporation
- Import HSM-protected keys for Key Vault (legacy) (retrieved May 2020), by Microsoft Corporation
- Import HSM-protected keys to Key Vault (preview) (retrieved May 2020), by Microsoft Corporation
- Transform Banking with the Microsoft Dynamics 365 Banking Accelerator (2019), by James Galvin, Chad Hamblin, Carr Phillips at Microsoft
- Selected articles on Key Management in the Cloud (2017-today) by Matt Landrock, Rob Stubbs, Stefan Hansen, Ulrich Scholten, Joe Lintzen and more
-
NIST SP800-57 Part 1 Revision 4: A Recommendation for Key Management (2016) by Elaine Barker
-
Selected articles on Key Management (2012-today) by Ashiq JA, Dawn M. Turner, Guillaume Forget, James H. Reinholm, Peter Landrock, Peter Smirnoff, Rob Stubbs, Stefan Hansen and more
-
CKMS Product Sheet (2016), by Cryptomathic
-
White Paper – Deploying CKMS Within a Business (2017), by Cryptomathic
- Perspectives for Web Service Intermediaries: How Influence on Quality Makes the Difference (2009), by Ulrich Scholten, Robin Fischer and Christian Zirpins
- The power of many: Corporate banking in an ecosystem world (2019), by McKinsey Company
- Platform-based Innovation Management: Directing External Innovational Efforts in Platform Ecosystems (2011), by Simone Scholten & Ulrich Scholten
- Banking-as-a-Service - what you need to know (2016), by Ulrich Scholten
- Banking as a Service – The bank’s perspective (2917), by Gaurav Sharma
- Digital Bank: Strategies to launch or become a digital bank Kindle Edition (2014), by Chris Skinner