3 min read
Turning Cryptography into a Service: Part 1 Overview
Cryptomathic : modified on 15. January 2018

- Home >
- Turning Cryptography into a Service: Part 1 Overview
Part 1 – Increasing Efficiency & Resilience
This two-part article discusses how cryptography is employed within organizations today and examines some of the challenges it raises, both for large, established enterprises and for start-ups within emerging markets such as FinTech, Internet of Things (IoT), and blockchain. hgmnthfjmntf
We show the benefits of shifting to a new paradigm where cryptography is operated as a centralized service with a simpler and more secure application development methodology.

In this part, we will look at the way cryptography has historically been deployed, how the organic growth of security systems results in spiraling inefficiencies, and what can be done to solve it. In the second part, we will look at the challenges of developing new crypto applications in a world where business agility is critical, and what can be done to accelerate time-to-market whilst simultaneously improving security practices.
The Critical Role of Hardware Security Modules
Cryptographic security is at the heart of the modern world, enabling e-commerce and protecting privacy in the digital age. Based on sound mathematical principles, it is employed in an ever-increasing variety of security applications, from authenticating card-based and mobile payments to protecting communications and personal data.
Hardware Security Modules (HSMs) are the mainstay of high-assurance cryptographic operations, providing a certified platform for executing cryptographic algorithms and generating and storing high-quality secret/private cryptographic keys within a tamper-resistant hardware envelope. HSMs are particularly prevalent within larger commercial enterprises, notably in the banking and financial services industry, where they provide tangible security and compliance benefits over software-based cryptography. But they are also being used increasingly by start-ups within the emerging FinTech, IoT, and blockchain industries, where high-assurance cryptography is a key enabler for the underlying technology.

Figure 1: Selection of HSMs
HSM Proliferation
Modern HSMs are extremely powerful, often capable of many thousands of cryptographic operations per second. However, few applications need that much throughput, or if they do (e.g. in the case of batch processing), then only for short bursts. The result is that HSMs are generally idle for most of the time, frequently operating at a utilization level well below 10%. That is not ideal when, as dedicated pieces of mission-critical hardware, HSMs tend to be relatively large, expensive, power-hungry, and require highly skilled and trusted staff to support and maintain them on a 24/7 basis.
To make things worse, production HSMs are usually deployed in pairs for resilience. There may be an additional pair of HSMs for production testing (reference system), another pair for backup (disaster recovery), and a further HSM for ongoing application development and maintenance. That’s a lot of expensive horsepower sitting there doing nothing.
As if that’s not bad enough, each application is typically a standalone project with its own project team, objectives, timescales, and security demands. This tends to preclude HSMs from being shared between applications, resulting in a proliferation of HSMs across the enterprise (see Figure 2).
Overall, this results in a huge amount of wasted capacity and squandered money – both Capex and Opex – which can quickly become unsustainable. But there is another way …
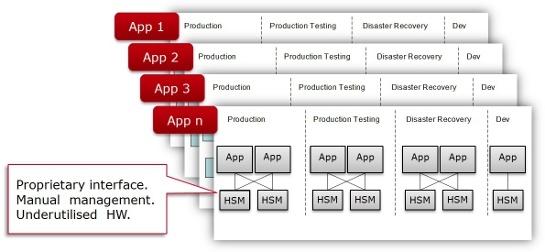
Figure 2: Traditional / Conservative Approach for Deploying HSMs
A New Paradigm for HSM Operations

Now imagine a world in which you can:
- Share HSMs between applications in a secure manner;
- mix-and-match HSMs from different vendors (eliminating vendor lock-in);
- phase out older, less reliable, or unsupported HSMs, and generally reduce the overall number of HSMs in use to a more affordable level (but without sacrificing resilience);
- perform regression testing of new HSM firmware just once, rather than for every application that uses that model of HSM;
- provision for the selection of both hardware and software cryptography as the business and technical circumstances dictate;
- control all HSMs using a single, centralized management tool and a single set of skilled staff;
- scale the estate of HSMs quickly and smoothly according to the total applied load.
Figure 3 illustrates an integrated and centralized cryptographic service model using Cryptomathic’s Crypto Service Gateway (CSG) that can readily enable all the above points, thereby providing significant savings for organizations with large cryptographic infrastructures and offering an excellent way for start-ups to manage their HSMs from day one.
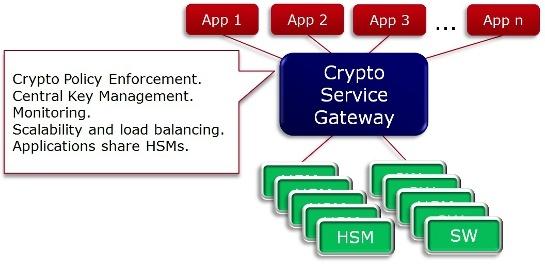
Figure 3: Cryptomathic's Approach for Sharing Cryptographic Resources
However, cost and flexibility are not the only benefits of this approach – the way cryptographic services are deployed also impacts positively on areas such as business agility and compliance. In the second and final part of this article, the emphasis switches from what may be viewed as the passive aspects of operating cryptography within an organization to the more dynamic aspects of deploying cryptography in new or changing business circumstances.
References and Further Reading
Selected articles on HSMs (2013-17), by Ashiq JA, Peter Landrock, Peter Smirnoff, Steve Marshall, Torben Pedersen, and more
