INTRODUCTION
This document is intended to help stakeholders understand the security challenges and threats around the European Digital Identity wallet (EUDI wallet), and to provide guidance on how to best address those challenges and threats.
Starting with a brief background to the EUDI wallet scheme and its core functionality, this paper presents two approaches to securing the wallet using either risk assessment or threat modelling. Irrespective of the approach taken, understanding the threats is fundamental to implementing secure solutions and, through reference to EU Agency Cyberspace (ENISA) material1, this paper introduces the threat landscape in which the wallets will operate including the actors, the agents and the vectors that will be used to attack the wallet, as well as ENISA and OWASP2 recommendations to securing mobile apps.
This paper also provides an overview of the mobile app security market and attempts to clarify the often confusing terms for the key features that the reader should consider when selecting a mobile app security solution. In addition, it will present the Cryptomathic Mobile App Security Core (MASC) solution along with features and benefits. This document is written for anyone involved in the design, development, consultancy, or support of the EUDI wallet. It is assumed that the reader understands the basic concepts of information technology, IT security and mobile apps.
THE EUROPEAN DIGITAL IDENTITY WALLET
The European Commission promotes the European Digital Identity wallet (EUDI wallet) as part of its effort to digitize the economy and help foster trust services. In practice this means that from the end of 2023 each EU Member State must offer a mobile-based wallet to their citizens, residents and businesses to identify and authenticate online. The scope of this app has been initially described in the Outline of the European Digital Identity Architecture and Reference Framework (The Outline)3, now superseded by The Common Union Toolbox for a Coordinated Approach Towards a European Digital Identity Framework4.
The Toolbox, adopted by the eIDAS Expert Group in January 2023, includes The European Digital Wallet Architecture and Reference Framework (ARF). While still work in progress and non- mandatory, it is expected to be replaced by the European Digital Identify Framework Regulation which willbe mandatory.
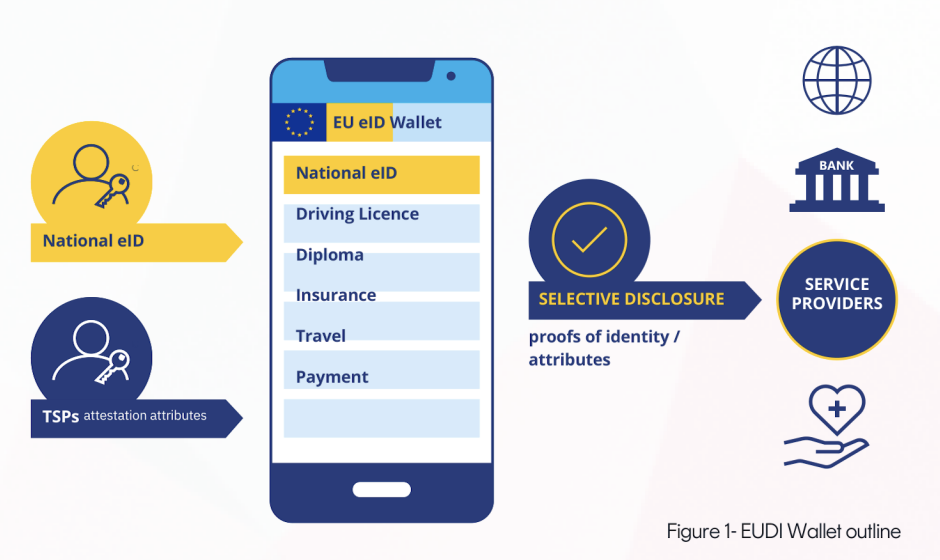
Through the EUDI wallet, which is part ofthe elDAS 2.0 proposal5, users should be able to securely store and selectively share in an app, locally or remotely, on request and under their sole control, identification data based on their national electronic IDs (elDs), as well as other attestations of attributes such as digital travel credentials (ePassports), driver's licenses, university diplomas, and also personal information including medical records or bank account details. The wallet should also allow them to access a variety of online services and sign documents with qualified electronic signatures and seals (QES). More broadly, the EUDI Wallet is a means to store and share digital assets and ensure trust through verified identities, reliable user authentication and legally binding signatures.
However, shifting to a mobile device creates security challenges due to a complex threat model and a significant increase in attack vectors due to the change in form factor, increase in features and expanded eco-system. The EUDI wallet must offer a sufficient level of protection against attacks from adjacent malware that may have been installed by naïve users and against professional and dedicated attacks on an emulated or rooted platform. Attacks could also target the communication channel between the EUDI wallet App and the back-end services or the back-end itself. Exploiting vulnerabilities in the ecosystem could result in forged identities or false claim assertions, including identity theft and data leaks.
Issuance of the EUDI wallet is up to each Member State, but eventually the EUDI wallet is to be used across Member States. The proposal for amendment of the elDAS regulation foresees that the issuer of the EUDI wallet may be the Member State itself, directly or through a mandate, or an independent party recognized by a Member State6. In all cases, issuing an EUDI wallet comes with a huge liability and a high risk for reputational damage, both for the issuer and the Member State. Upon breakage or compromise of an EUDI wallet, the issuing Member State shall, without delay, suspend the issuance and revoke the validity of the European Digital Identity wallet and inform the other Member States and the Commission accordingly. One can easily anticipate the media coverage in hypothetical cases such as:
- Terrorists break into the Belgian identity wallet and present seemingly valid travel documents at Charles de Gaulle airport.
- A Swedish minister presents a counterfeited diploma using her EUDI wallet during the due diligence process prior to her official appointment.
- EUDI wallet vulnerability is exploited by an unknown attacker resulting in the leakage of confidential data for 3 million Danish citizens.
- Hacktivists exploit the Spanish EUDI wallet to obtain social health benefits for 3000 migrants.
The European Commission intends to release an open-source software development kit (SDK) for the EUDI wallet to help ensure interoperability and foster usage. Nonetheless, the reliability for the security of the wallet remains to the issuer and the issuing country.
While the EUDI wallet will implement a number of security features which may include an embedded crypto interface and interfaces a Trusted Execution Environment (TEE) and native Secure Elements (SE), the SDK will not be in a position to mitigate security risks such as reverse engineering, nor will it provide strong device and assurance. EUDI wallet issuers will need to further harden the app and run penetration tests to pass certification.
CORE FUNCTIONALITY OF THE EUDI WALLET
The EUDI wallet must be able to provide mutual identification and authentication between the wallet and external entities. It must be able to perform electronic identification of the EUDl wallet user, and store and manage digital assets and provide qualified electronic attestation of attributes (QEAA) and electronic attestation of attributes (EAA). It must be able to request and obtain such QEAA and EAA from providers, protect them against counterfeiting and unintended information disclosure, and share person identification data (PID) and QEAA and EAA selectively with relying parties, both electronically and visually, with signatures verifying the authenticity of the documents. The PID and attribute presentation must also function offline, without network access.
The EUDI wallet must implement (access to) all cryptographic functions needed for the above functionalities and must provision qualified and non-qualified electronic signatures and seals either locally on the device or using a remote Qualified Signature Creation Device (QSCD).
The EUDI wallet will be able to interact with relying parties, for example citizen portals, banks, online platforms and airports, through its external interface to request attestations with mutual authentication.
While the elDAS 2.0 proposal foresees that the EUDI wallet storage can be local or remote, i.e. located on a device the user holds or in a cloud-based infrastructure, the requirement for offline sharing of identifying data and attested attributes means that, either way, some minimum on-device storage is required that must be adequately protected.
The ambitious scope of the EUDI wallet presents a significant attack surface and requires careful planning in order to deploy a secure solution.
Figure 2 depicts the functionalities of the core EUDI wallet and its interfaces with external entities
APPROACHES TO SECURING THE EUDI WALLET
-
Risk terminology and approaches
Organizations responsible for the development of EUDI wallets will already have their own general in-house approach to protecting the many assets for which they are stakeholders. This approach likely includes various risk management and threat management techniques to be used depending on the type of asset and its status.
For example, a physical safe containing millions of Euros will face different threats and vulnerabilities than the intangible reputation of an organization's brand. Therefore, when treating the associated risks of these two assets, the organization would use different approaches.
The EUDI wallet is designed to control access to verified, sensitive personal information, and provide a means of identifying and authenticating the owner of the wallet for the purposes of interacting with financial services, medical institutions, government agencies and other similar third parties. The value contained in these EUDI wallets, along with their use in authentication to third-party services, is attractive to threat actors.
Further, large-scale deployment is the goal and any EU citizen will be able to install and use the EUDI wallet. Ultimately, the ambition is to have the EUDI wallet on hundreds of millions of unmanaged mobile phones, tablets and other devices. Each device type will have a different set of vulnerabilities that will evolve over time, so the EUDI wallet will likely be under constant across multiple fronts.When discussing potential strategies for securely deploying an EUDI wallet, this white paper will use risk management terms as defined by ENISA7 and NIST8 for consistency.
Figure 3: Risk Management Terms, as defined by ENISA
For existing assets with known vulnerabilities, a risk-based assessment may be most appropriate to identify, evaluate and prioritize risks to be treated. Figure 3 depicts 'risk' in terms of a 'threat', 'asset' and 'vulnerability'.
When designing a new asset (in this case the EUDI wallet), the wallet has not been developed and therefore the vulnerabilities inherent to the asset, have not been identified. Further, it will almost certainly be a design-criteria to minimize the vulnerabilities. Therefore it may be more appropriate to use a model focused on identifying the 'attack surface' of the asset in order to implement appropriate security controls. This paper uses the NIST definition of 'attack surface9.
Here are many terms used to define a 'security measure' to protect the attack surface, whether protection is against a known risk or not. These terms include 'control', 'mitigation', 'risk control' and 'countermeasure'. Since risks evolve over time as the threat landscape changes, new vulnerabilities are discovered and the asset is developed, these terms will be generalized as synonyms and use them interchangeably. Finally, the term 'vulnerability' can also refer to an 'absence of an effective control against a known risk'.
Figure 4: Attack Surface' as defined by NIST
-
Risk Assessment
When protecting an existing asset with known threats and established vulnerabilities, a risk assessment may be the most appropriate technique to enhance the security of the asset.
Figure 5 - Representative Risk Management Process
Context/Triggers
In this case, the context for a risk assessment would likely be an existing EUDI wallet deployment and would include current threats and the known vulnerabilities. The actual assessment could be triggered by a change to threat landscape, the identification of new vulnerabilities, a planned enhancement of the wallet, or a scheduled / ad hoc review.
Identify Risks
The first stage for the responsible parties is to identify the current and potential future risks associated with the EUDI wallet. Analyze Risks Analysis of these identified risks involves assigning a probability of each of them occurring, and the associated impact. When considering the probability of a risk occurring, the Common Vulnerability Scoring System10 is useful and commonly useful tool to quantify a vulnerability in terms of ease of exploit, size of attack surface, level of access required to exploit the vulnerability and the impact of exploit.
Analyze Risks
Analysis also considers existing controls or processes that are designed to minimize the risks. This stage of the risk assessment process is usually specific to the organization and is possibly based on, amongst other things, a mix of statistical analysis, empirical data, expert advice and modelling. The output could be a risk rating (such as high, medium and low), it could be expressed in impact (monetary, technical, operational and societal). As ENISA states: "....the specification of the risk level is not unique. Impact and likelihood may be expressed or combined differently, according to the type of risk and the scope and objective of the Risk Management process"11.
Evaluate and Treat Risks
The organization can then evaluate which of these remaining risks to address and with which priority. For each residual risk, the organization will decide whether to:
- Improve, or optimize controls in the environment to further reduce the risk;
- Transfer the risk to another entity, such as insuring against the risk occurring or contracting another entity to treat the risk. It is worth noting that, even when transferring the risk, the organization is still responsible for the actual risk;
- Decide to avoid the risk entirely. In the case of the EUDI wallet, an example of risk avoidance could be the removal of a fully automated identity proofing process from the wallet. The removal of this process would also remove the associated risks of false positives in the identification proofing;
- Retain or accept the risk for a period of time. Risk retention/acceptance could be an appropriate response to a risk with a low likelihood of occurring and a minimal impact in the event it does occur. However it would be entirely inappropriate if the risk related to identity theft or data leakage.
-
Threat Modelling
For a new development where the vulnerabilities inherent to the asset have not been identified, threat modelling may be a more appropriate methodology and allows the developer to focus on the entire attack surface when developing and deploying security controls, and not just the risks.
Figure 6: Representative Risk Management Process
Figure 6 also includes a feedback loop since the:
- Features and/or the inherent value of the asset, in this case the EUDI wallet, may change over time;
- Threat landscape will change based on geopolitical, social, environmental factors;
- Discovery of vulnerabilities in technology, people and processes is an ongoing process;
- Risks inherent in the asset today can influence the EUDI wallet's features, threats and discovered vulnerabilities tomorrow.
Context/Triggers
Threat modelling likely precedes the initial development of a EUDI wallet but could also be triggered by an enhancement to the wallet, a change to the threat landscape or a scheduled / ad hoc review. The context in modelling will be the planned functionality of the wallet and the entire wallet eco-system.
Identify and Categorize Applicable Threats
The first stages of threat modelling typically involve identifying the attack surface of the wallet. In practice, and taking into consideration that NIST defines an attack surface in terms of a system, "...he boundary, a system element, or an environment...",an effective way to achieve this is to deconstruct the wallet into multiple component parts that support the functionality. In essence you would break the EUDI wallet down into the functionalities and interfaces of the EUDI wallet similarly to Figure 2. Using knowledge of the applicable threats to the EUDI wallet and typical attack vectors, the organization can then either develop or choose one of several available threat models in order to categorize these threats.
Analyze and Evaluate Threats
During the analysis and evaluation of threats, the organization can then prioritize and group threats to devise a strategy to protect their EUDI wallet and ensure appropriate countermeasures (security controls) can be designed into the solution. The three types of security control are:
- Preventive - designed to prevent an attack or minimize the likely success of an attack;
- Detective - designed to notify in realtime or near-real-time of an attack;
- Corrective - (once notified) designed to restore the asset to normal operations following and attack.
Implement Security Controls
In practice, the overall security design of the EUDI wallet willrequire a blend of these types of security control to be implemented. Given the modular nature of the EUDI wallet and the interface, these security controls will be reused frequently. For example, preventing access to sensitive information is a common requirement across all functionalities and interfaces of the EUDI wallet (Figure 2); as is ensuring the runtime integrity of each component. These controls will likely require the implementation of security tools, monitoring tools and processes.
Validate Controls and Identify Vulnerabilities
During the development phase of the wallet, there should be testing of the wallet to validate the effectiveness of these implemented controls and identify any vulnerabilities. The ideal outcome of this methodology is an EUDI wallet with minimal known vulnerabilities over its entire attack surface, not just in the areas of known risk. In doing so, this provides additional assurance that the wallet will be more resilient to as yet unknown threats and attack vectors.
THREATS TO THE EUDI WALLET
Threat Landscape and Actors
In its latest annual Threat Landscape Report12, ENISA provides a thorough analysis on the status of cybersecurity threat landscape, including identification of top threats, major trends, threat actors and attack techniques, impact and motivation analysis as well as relevant mitigation measures. The report states that threat actors are increasing their capabilities, having frequent access to previously unknown (0-day) exploits, developing their hacker-as-a-service business model and developing novel and hybrid threats.
Threats to the EUDI wallet will come from multiple diverse sources across this entire landscape, all with varying motives. This paper will align with the four classifications of threat actors defined by ENISA: State sponsored actors; hacktivists; cybercrime actors; and hacker for hire actors.
Modelling Threats to the EUDI Wallet
When modelling threats, there are several techniques from which to choose depending on the modelling perspective as well as the required level of sophistication.
Organizations will likely have their own approaches but this example will use the Microsoft developed STRIDE13 model to categorize different types of threats as it takes an asset-centric approach to describing them and is a relatively straightforward model to apply.
The name itself is a mnemonic where each letter corresponds to one of the six threat categories as detailed in the following table.
Figure 7: STRIDE Threat Model by Microsoft
It is worth noting that the EUDI wallet must work offline and must therefore store sensitive data like keys, and personal identity documents.
This requires that documents, cryptographic keys and other private information be present on a mobile platform which may be exposed to loss, hardware failures, malware, hackers and thieves. Protecting this sensitive data against copying and viewing by unauthorized parties, while at the same time providing controlled access to authorized parties, is paramount.
The mobile platforms (iOS and Android) are owned by US commercial companies who are not subject to EU legislation. The mobile hardware is mostly manufactured in the Far East and mainland China, therefore, relying solely on the hardware and OS platform's security measures may be risky for vital identification documents like passports and driver's licenses.
The threat actors will then seek vulnerabilities in:
- The people that support the EUDI wallet ecosystem as well as the EU citizens that use the wallet.
- The processes associated with the scheme.
- The technologies with which the EUDI wallets have been implemented and the methods used to implement them.
Broadly speaking, when considering the EUDI wallet itself, there are two attack vectors:
Attacks against the mobile app itself
This is inherent to mobile apps that are published to the Apple App Store, Google Play store and such like to be installed on unmanaged devices. This opens the EUDI wallet up to countless attacks via the app or the device itself, such as using reverse engineering tools, exploiting device memory, altering the user interface or creating similar apps to confuse the user. Mobile app developers can leverage the security features of the OS and run pen tests themselves, but this does not provide a robust enough framework to operate an EUDI wallet.
Attacks against APIs and communication channels
Such attacks will focus on the interfaces between the EUDI wallet and the participants in the wallet scheme primarily to expose personal identity data and personal attributes. Additional attacks could focus on attempting to obtain application logic by probing the interfaces.
Threat agents can be considered an extension to the definition of threat actors and are typically tools, techniques and assets used to exploit vulnerabilities. They will be used in an attempt to exploit the attack surface of the EUDI wallet via one of the two attack vectors.
Examples of threat agents are numerous and include:
- Lost/stolen EUDI wallets in the hands of a threat actor.
- Malware installed on the device which can interact with the EUDI wallet in a malicious manner to log user credentials, output, or probe the app to act in an unintended manner. This includes malicious overlays and screen casting tools.
- Jailbroken/rooted devices.
- A jailbroken device offers less OS guarantees and a rooted device.
- Repackaged apps on the mobile device hosting the wallet that interact with the wallet.
- Mobile apps that incorrectly implement security mechanisms the underlying mobile app platform (e.g. iOS, Android).
- A compromised or monitored network that allows eavesdropping or altered network communications.
- Development and test tools that can interact with the mobile app at a low level to gain a detailed understanding of how the app's security mechanisms work to obtain sensitive information contained within it or change the way in which the app operates.
- Poor code quality can lead to the discovery of vulnerabilities that the attacker can exploit.
Without device and API assurance, it is not sound to launch a EUDI wallet.
ONLINE RESOURCES TO ASSIST IN DEVELOPING AND TESTING YOUR EUDI WALLET
Enumerating the threat landscape associated with the EUDI wallet scheme is a significant undertaking; as is defining the attack surface of the wallet in all its form factors, the back-end infrastructures, the associated processes and the organizations. In that context, irrespective of whether an organization performed a risk assessment (Section 5.2) or threat modelling (Section 5.3) to arrive at its final approach to securing the wallet, ENISA's published Smartphone Guidelines Tool14 is a useful resource against which organizations can reconcile the coverage and comprehensiveness of their security controls.
The guidelines provide recommendations for 152 security measures which are grouped into 13 domains, as follows:
i. Correct handling of runtime code interpretation to prevent the introduction of deliberately malformed inputs to the app in order to alter its operational behavior or to leak information.
ii. Secure data integration with third party code to minimize the risks associated with using third party code in the mobile app. Such risks including deliberate or inadvertent direct access to app itself or user data, or the introduction of a vulnerability into an otherwise secure application.
iii. Protection of the application from client-side injections to protect the mobile app from malicious attacks from sensors and other apps installed on the device, as well as third party services that the device interacts.
iv. Secure handling of authentication and authorization factors on the device to protect credentials that are used to obtain access to mobile backend services and other services and accounts owned by the user.
v. Identification and protection of sensitive data on the mobile device to protect sensitive data such as personal user data and business critical data stored on the device against extraction, for example in the event of device loss or theft.
vi. In-transit protection of sensitive data to prevent the interception and modification of data passing through shared channels including Wi-Fi, cellular networking technologies, Bluetooth and Near Field Communication (NFC).
vii. Device and application integrity to protect the app both from and when operating in an insecure manner where its integrity may be compromised which undermines the security and privacy controls implemented in the mobile application.
viii. Secure software distribution to implement best practices for distributing the software via mobile app stores including security updates.
ix. Consent and privacy protection to minimize the likelihood of unintentional disclosure of personal or private information; and to ensure that user consent is provided for data collection, sharing and usage that takes place on the application.
x. Correct implementation of user authentication, authorization and session management to protect the mechanisms, secrets and data that are used to authenticate and authorize the user from unauthorized access in the event of sharing, loss or theft of a mobile device. These protections should cover the device when the application is dormant as well as in use.
xi. Protection of paid resources to protect the device from possible abuse of access to phone calls, SMS, roaming data, NFC payments, and third-party payment systems.
xii. Security of the backend services and the platform server and APIs to prevent unauthorized access to backend APls and services either directly or via unauthorized connections through the mobile application itself.
xiii. Correct usage of biometric sensors and secure hardware to enforce best practices when enabling biometric sensors to be used in authentication mechanisms.
Another comprehensive and frequently updated resource comes from OWASP Mobile Application Security project15. This includes three core components:
i. OWASP Mobile Application Security Verification Standard (MASVS)
Defines a mobile app security model and lists generic security requirements for mobile apps. To be used during planning and architecture design stages of the mobile app. These requirements map to the OWASP Mobile Application Security (MAS) Checklist.
ii. OWASP Mobile Application Security Testing Guide (MASTG)
Contains a test methodology for verifying the implemented security controls. Includes actual test cases for iOS, Android as well test cases that are common across platforms. Test cases map to the OWASP MAS Checklist.
iii. OWASP Mobile Application Security (MAS) Checklist
Maps the security requirements in the MASVS to test cases in the MASTG to allow reconciliation of tests performed against to security.
The MASVS (prior to v2.0.0) defines two security verification levels, Standard Security (MASVS L1) and Defense-inDepth (MASVS L2) which includes and adds to the Standard Security requirements. It is interesting to note that one of the requirements of MASVS L2 is that a threat model must exist.
An additional verification level called Resiliency Against Reverse Engineering and Tampering (MASVS R) is complementary to MASVS L1 and L2 and is designed to ensure that the "app has stateof-the-art security, and is also resilient against specific, clearly defined client-side attacks, such as tampering, modding, or reverse engineering to extract sensitive code or data."16
As you would expect the verification guide states that MASVS L2 and MASVS R be applied to "All mobile apps that, by design, need to store sensitive data on the mobile device, and at the same time must support a wide range of devices and operating system versions. In this case, resiliency controls can be used as a defense-in-depth measure to increase the effort for attackers aiming to extract the sensitive data". This description can be applied to an EUDI wallet.
In total, there are 84 requirements within the following 8 categories for MASVS L2 + R which can assist through the development lifecycle of the EUDI wallet:
i. Architecture, Design and Threat Modelling Requirements to ensure that security has been explicitly addressed when planning the architecture of the mobile app, and that the functional and security roles of all components are known.
ii. Data Storage and Privacy Requirements to protect against exposure of sensitive data to other apps running on the same device, to cloud storage, backups, keyboard caches etc., either unintentionally or through attack.
iii. Cryptography Requirements to ensure cryptographic best practices are applied within the app.
iv. Authentication and Session Management Requirements to ensure best practices are applied within the app to user accounts and session management.
v. Network Communication Requirements to protect the communication between the app and back-end services.
vi. Platform Interaction Requirements to ensure that the app uses platform APIs and standard components in a secure manner and interact with other apps securely.
vii. Code Quality and Build Setting Requirements to ensure that basic and easy to implement security coding practices are followed in developing the app.
viii. Resilience Requirements (MASVS R) to increase the app's resilience against reverse engineering, tampering and specific client-side attacks
SELECTING A MOBILE APP SECURITY SOLUTION
Terminology
RASP vs App Shielding vs In-App Protection
The importance of implementing appropriate security mechanisms within the EUDI wallet is clear but it can be confusing to determine exactly what protections are needed when researching vendors and solutions.As a starting point, Gartner defines three categories of mobile app security solutions:
Runtime application self-protection (RASP)
A security technology that is built or linked into an application or application runtime environment that can control application execution while detecting and preventing real-time attacks.17
Application shielding
This refers to protection capabilities that are implemented directly within the application, rather than inline or on the hosting system, to prevent and detect attacks such as tampering and reverse engineering. Application shielding can be used for any type of application, but there is currently a particular focus on mobile apps.18
In-App protection
These are security solutions implemented within the application (instead of the network or the operating system, for example) to make the application more resistant to attacks such as malicious data exfiltration, intrusion, tampering, and reverse engineering.19
The Two Types of Mobile App Security Solutions
Solutions classified as providing RASP, app shielding or in-app protection all offer safeguard against reverse engineering and tampering. However, they all fall into one of two key categories:
i. lt secures the app after development: Once development is complete and the app is tested and functional, it is submitted to a service to have software protection mechanisms added to the final code and have its structure altered to make it difficult to reverse engineer and tamper. During this process, configuration settings determine which protections to enable.
Figure 8: Mobile App security solution as a service
Solutions described with terms like 'app shielding', 'app guarding' or similar tend to offer this service. This solution is relatively easy to implement.
ii. It includes a toolkit to secure the app during development: At the outset of the development, a software development kit (SDK) is incorporated to the development environment. The SDK is essentially a suite of security tools that prevent reverse engineering and tampering of the app.
The developer can then focus on developing the functional requirements of the mobile app while leaving the specialist and security-critical parts to the SDK.
Figure 9: Mobile App security solution includes a toolkit
Such solutions are aligned with the 'shift left' approach whereby security is a central design consideration at an earlier stage in the development lifecycle rather than an afterthought. Solutions described with terms like 'in-app protection', 'security core' or similar tend to offer an SDK. They tend to offer increased security coverage, flexibly tailored the specific functionality of the app.
Figure 10: Comparison of Two Types of Mobile App Security Solutions
What to Look for in Your Mobile App Security Solution
Having modelled the threats against your EUDI wallet mobile app and using the STRIDE model (Section 6.2) for this example, you will start to see a pattern emerging for required security measures.
For the threats classified as Spoofing you will require a security measure that provides authenticity. Such an authentication mechanism requires a tamper-resistant environment (integrity protected) in which to run, as well as access to secrets that are protected against Information disclosure.
For threats classified as Repudiation you will require a nonrepudiation countermeasure. Such a security measure requires that the information is integrity protected and authenticated (using public key cryptography). Again, this points to a security measure that runs in a tamper-resistant and confidentialityprotected environment.
Threats classified as Elevation of privilege will require the development of appropriate authorization mechanisms. Again, to be robust, they will need to be protected from tampering and information disclosure.
There are few threats that can be categorized as Denial of service for the mobile app itself, however a standard countermeasure is to ensure connections are appropriately authenticated. Again, this requires mechanisms that are protected from tampering and information disclosure.
Thus, the foundation of secure mobile app development is mechanisms that protect the integrity and confidentiality of the app and its contents, essentially protecting against Information disclosure (using anti-reverse engineering security measures) and Tampering (using anti-tampering security measures).
Therefore, you should choose a mobile app security solution that has comprehensive coverage of security measures against Information disclosure and Tampering, both while the app is running (dynamic) or not running (static). Using such a mobile app security solution as the foundation, the EUDI wallet developer can feel confident in implementing the other security measures directly into the app.
The following table describes the security measures to look for when selecting your mobile app security solution and the rationale for each.
Figure 11: Security Measures Relevant for Selecting a Mobile App Security Solution
Figure 12: (Continuation) Security Measures Relevant for Selecting a Mobile App Security Solution
Certain of the security measures in Figures 11 & 12 can be classified as protection against information disclosure, against tampering, or against both. Further, security measures can provide protection while the app is running (dynamic), dormant (static), or both. The following diagram depicts which security measures from Figure 13 fall into which classification.
Figure 13: Classification of security measures
INTRODUCING THE CRYPTOMATHIC MOBILE APP SECURITY CORE
Cryptomathic Mobile App Security Core (MASC)20 is a security software development kit (SDK) for the EUDI wallet, elD apps, mobile banking apps etc., comprising of multiple layers of mutually reinforcing mobile app security components that are provided with a simple, easy-to-use API. It enables app developers to focus on developing excellent business applications while leaving the specialist security critical parts to MASC.
Protecting applications in a hostile environment is a cat-and-mouse game with attackers. Released over 10 years ago, MASC stays ahead by providing an evolutionary security framework through regular defense mechanism refinement and updates and randomized protections, disrupting the business model of fraudsters attempting to exploit the protection of targets long-term. MASC features multiple layers of security, including: libraries for security protocols, TLS authentication with pinned certificates and third-party libraries integrated for malware detection and device fingerprinting.
MASC offers technology for reverse engineering resistance, jailbreak / root detection and secure configuration and operation of generic mobile apps. To provide 360-degree protection, there are additional mechanisms for obfuscation, anti-tamper and anti-debug, as well as a reporting scheme allowing for live monitoring and dynamic analysis of the current threat landscape. A central part of MASC is the ability to provide the application with secure storage and independent cryptographic functions. The storage builds on and extends key stores offered by the device or OS and can be used to protect critical cryptographic keys, for instance application keys or communication keys for entities like the backend services
-
How MASC Helps in Following the ENISA Guidelines
The ENISA Smartphone Guidelines Tool suggests a total of 152 security measures to address the challenges and threats discussed thus far. Some of these measures are to be taken care of server side, while others are to be implemented within the app itself; and of those, 47 security measures are relevant to the mobile app security solution space. MASC supports the implementation of 44 of these 47 security measures (94%)21, as detailed in Figure 14.
Figure 14: MASC support for relevant ENISA Security Measures (relevant to Mobile App Security solutions)
-
How MASC Helps in Following the OWASP MAS (based onMASVS v1.5)
OWASP Mobile Application Security Verification Standard (MASVS) as detailed in Section 7.2 suggests a total of 84 security requirements to address the challenges and threats discussed thus far. Of these, 52 security requirements are relevant to the mobile app security solution space. MASC can support the implementation of 49 of these 52 requirements (94%)23, as detailed in Figure 15.
Figure 15: MASC support for relevant OWASP MAS Requirements (relevant to Mobile App Security solutions)
SUMMARY
The EUDI Wallet will likely be part of our daily life, whether it is used to access public services, open a bank account, board an airplane, purchase car insurance, apply for a new job, or some other function. Given the central role it will play, the EUDI wallet will likely be under constant attack from a variety of vectors, including hackers, statesponsored entities and organized cybercriminals. To be regarded as trust anchor, both on a national level but also in all EU member states, as mandated by the revised EIDAS regulation, the EUDI issuer needs to carefully consider its risk mitigation strategy and develop a defense model encompassing both proactive measures and reactive measures. For most issuers, issuing a mobile app with rich and security sensitive functionality on a such a large scale is a new territory.
Foundational to the secure development and deployment of your EUDI wallet is a focused risk assessment and/or threat modelling to gain a comprehensive understanding of the associated risks and/or threats associated with the wallet. This process will be invaluable to ensure and maintain secure operations and user confidence in the mobile app, specifically to:
- Plan and implement the necessary preventive, detective and remediation measures;
- Identify requirements to enhance in-house technical resources & skills, processes and security tooling. Mobile app security is a complex field and requires a skillset that differs from mobile app development and DevOps;
- Reference and update to reflect changes to the threat environment or prior to changes to the wallet app itself.
In addition to providing industry best practice, reputable online resources such as ENISA Smartphone Guidelines and OWASP Mobile Security Standard can be used to reconcile the coverage and effectiveness of your security measures. The Cryptomathic Mobile App Security Core (MASC) fulfills key selection criteria for an effective mobile application security solution to complement your approach to secure software lifecycle development. This mobile security product featuring a mobile app security SDK and a back-end assurance services offers an evolutionary security design, continuously enhanced and refined over 10 years, that provides protection measures to not only be resistant to the threats of today but also responsive to emerging ones. With 94% coverage against ENSIA security controls, MASC is a highly valuable security solution for EUDI Issuers.
Furthermore, MASC does not come at the cost of sovereignty for an EU-based EUDI issuer. Cryptomathic develops, maintains and supports the MASC solution out of Denmark with no external dependencies. With the vast majority of mobile devices being manufactured in China and India, and the operating system owned and developed by US corporations, protecting the core of the wallet app with mobile app security developed and tested in the EU by an EU company provides you with reassurance that you will have control over security measures. The loyalty of MASC's customer base over the decade is testament to its ongoing effectiveness.
