4 min read
Random Number Generators and Their Role in Cryptography
Cryptomathic : modified on 23. April 2019

- Home >
- Random Number Generators and Their Role in Cryptography
In this article, we examine the use of random number generators (RNGs) in cryptography, specifically in relation to hardware security modules (HSMs) and encryption key management system (KMSs).
Hardware security modules
Let us start with the HSM. An HSM is a special and “trusted” networked device that is responsible for performing critical cryptographic operations, including key generation, key storage, and key protection. The HSM must be trusted to protect the cryptographic operations from being breached. Trust is in the HSM being free of vulnerabilities that could threaten the integrity of the cryptographic processes performed.
To achieve a trusted status, such as FIPS 140-2 certification, an HSM must:
- Be built from specialized hardware that has been tested and certified in special laboratories.
- Be running a security-focused operating system.
- Have limited access through a network interface that is controlled by internal rules
- Actively hide and protect cryptographic information
The role of RNGs in cryptography
Cryptographic algorithms require keys. A Random Number Generator (RNG), also called a Random Bit Generator (RBG), is needed in the key generation process to create a random (strong) key as well as for other cryptographic purposes such as initialization vectors and nonces. Typically, a True Random Number Generator (TRNG) provides a source of randomness, or “entropy,” to seed a Pseudo-Random Number Generation (PRNG), also called a Deterministic Random Bit Generator (DRBG). RNGs must be capable of generating random numbers at least as quickly as they are consumed.
RNG evaluation requirements
NIST's Federal Information Processing Standard (FIPS) PUB 140-2 has compliance requirements for implementing an HSM. It says that HSMs must use a DRBG that complies with SP 800-90A (Recommendation for Random Number Generation Using Deterministic Random Bit Generators) and an entropy source that complies with SP 800-90B (Recommendation for the Entropy Sources Used for Random Bit Generation).
Developers must demonstrate that their entropy source is sufficiently random through a combination of design and/or test processes, along with continuous checks during operation, as any fault could have catastrophic consequences for generating secure cryptographic keys.
Can RNGs be computer-generated?
RNGs require entropy, and entropy originates from a noise source. Noise sources can be divided into two categories: Physical noise sources use dedicated hardware to generate randomness, whereas non-physical noise sources use system data (such as the output of API functions, RAM data, or system time) or human input (e.g., mouse movements) to generate randomness.
In general, physical noise sources are considered to offer greater randomness for demanding applications such as HSMs. The nature around us is full of random processes. Some electrical parts are classical examples:
-
Avalanche diodes (Zener breakdown noise), reverse biased
-
Atmospheric noise (via attached radio-receiver)
-
Thermal noise in resistor (amplified)
-
Radioactive decay etc.
Such random sources can be divided into two classes: those based on quantum effects and those not based on quantum effects. Quantum-based sources are very complex in implementation but give stable results. Non-quantum sources are more economical, but can give unstable results. The quality depends on various factors, such as temperature.
Implementations
A typical HSM is equipped with a very good hardware RNG installed in highly secured conditions - including a thermostat, a stabilized power source, a very powerful post-processing computer etc.
The advice is simple: do not reinvent the wheel, use an HSM.
HSMs have proper, tested, stable RNGs with documented compliance, e.g. FIPS 140-2.
Where centralized key life-cycle management comes in
Large organizations rely heavily on cryptography solutions and require its availability and throughput at various places in a decentralized environment. Take the example of an international bank: key generation might be required in New York, London, and Hong Kong for various applications related to transaction authorization, document signing, or payment cards. How can the dilemma of business efficiency be solved without compromising security?
In the following, we describe how keys can be created and managed in a centralized way, with applications and key targets at different locations, but where keys are never available unencrypted outside of an HSM. The described solution will ensure auditability and logging at one central location to allow for banking-grade compliance, such as PCI-DSS.
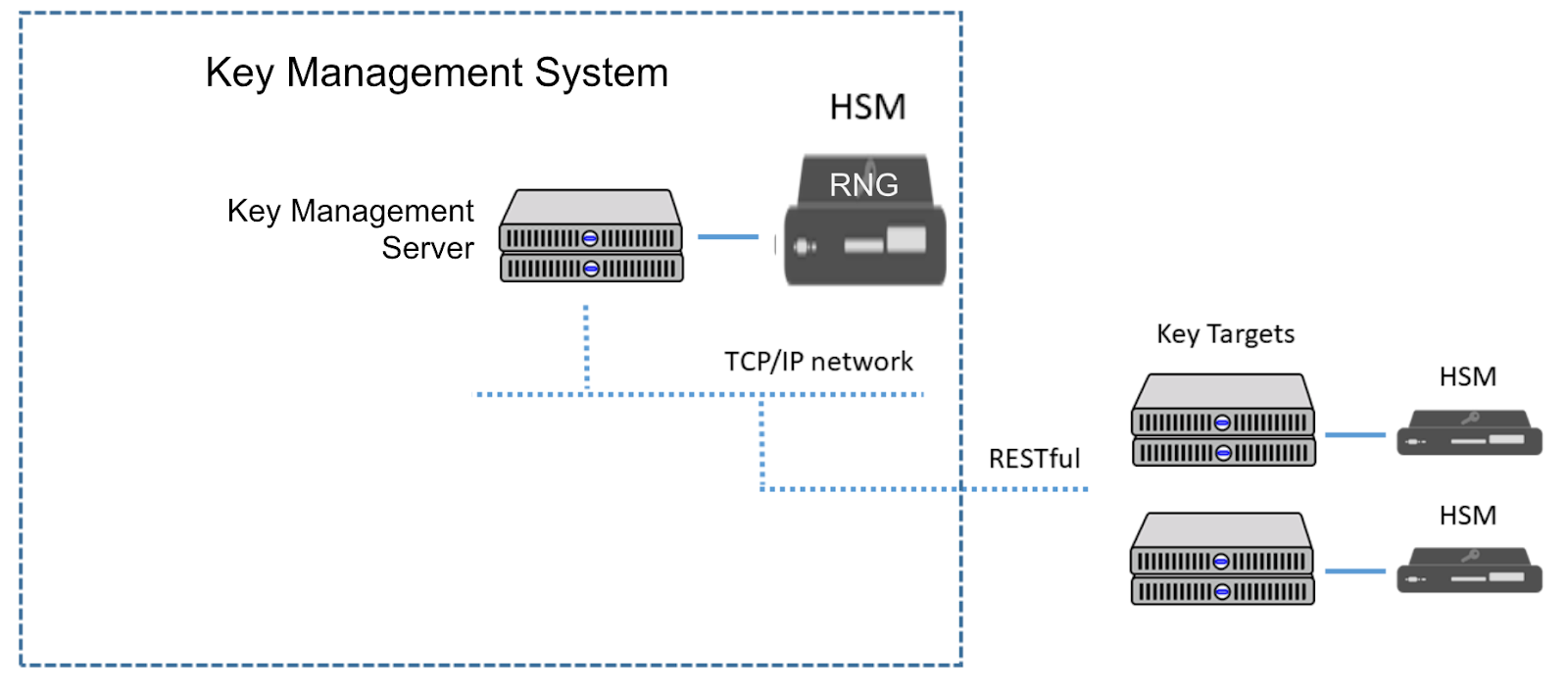
The figure below shows a distributed architecture with centralized encryption key management solutions. Inside the HSM, which is attached to the central key management server(s), the RNG is responsible for generating a variety of keys, including those in charge of administering the security cluster. The KMS will manage the application key that is necessary for one of the key targets or cryptographic applications. Another example of keys are the key encryption keys (KEKs) that are needed for administrative tasks such as key distribution. The KEKs are shared with key targets and used for encrypting application keys when they are pushed from the key management system to the key target.
To provide a high level of security and secure key usage, there should be additional HSMs attached to the key targets. In a distributed scenario, the RNGs within the key management system’s HSM will remotely generate the various application keys, and the key management system server will securely distribute the keys that are needed throughout the business. The lifecycle of the keys is thereby managed from the central key management system, and the keys that are used by the applications are protected by the HSM connected to the key target.
Instead of attempting to keep track of key life-cycles by manual methods, the computerized key management system provides the framework that is needed to automatically manage numerous keys at various locations throughout their life-cycles.
Summary
Certified Random Number Generators should be responsible for the generation of all cryptographic keys. Hardware security modules are the secure hosts for the keys, the RNGs and the key generation process.
Key management systems manage the life-cycle of these keys to allow for banking-grade auditability. To respond to modern business requirements 24/7 across physical barriers and borders, centralized encryption key management solutions can coordinate HSMs and provide availability of cryptographic keys, wherever and whenever they are required in a most secure way. In other words, centralized key management systems can be used to protect multiple applications and their keys from a single point. RNGs generate the keys, HSMs securely store and protect the usage of these keys, but it is the key management system that is working behind the scenes to manage the keys’ life-cycles to ensure their validity.
With this approach, the high value application keys are generated with the central KMS using an HSM with a high quality RNG.