4 min read
Exploring DORA: Key Insights for Financial Compliance
 Edlyn Teske
:
modified on 21. March 2024
Edlyn Teske
:
modified on 21. March 2024

- Home >
- Exploring DORA: Key Insights for Financial Compliance
Cryptomathic solutions support your financial institution towards compliance.
The financial sector is increasingly dependent on technology and tech companies for the provision of financial services, making it vulnerable to cyber-attacks. Cyber risks have already been addressed at EU level, but the rules have been partial, fragmented and often unevenly implemented across Member States.
The Digital Operational Resilience Act (DORA) introduces uniform and harmonized principles to build resilience of entities across the EU financial sector, having significant implications for financial institutions. Our Cryptomathic Key Management Solution can facilitate compliance with the help of Article 9 of DORA (Protection and Prevention).
This blog highlights DORA's implications, demonstrating how Cryptomathic can help.
What is dora?
DORA entered into force on January 2023, as EU regulation 2022/2554 and will be directly applicable in all Member States from January 17 2025, by which Member States must also notify their national laws, regulations and administrative provisions to the European Commission and the three European Supervisory Authorities EBA, ESMA, and EIOPA (the ESAs).
Just like the EU Directive 2022/2555 on Network and Information Systems (NIS2), DORA contains a framework of requirements for cybersecurity risk management and reporting. Whilst both have a binding nature, the key difference is that NIS2 mandates the Member States adopt binding instructions, whilst DORA is directly applicable in all Member States. Furthermore, NIS2 affects a variety of 18 different critical or highly critical sectors, whereas DORA focuses on the financial sector.
DORA applies to a wide range of financial entities including banks, insurance companies, investment firms, payment services that operate in the EU, as well as their ICT third-party providers (as see Figure 1).
Of course, the banking industry as a sector of high criticality is also covered under NIS2. Here, NIS2 delivers a general framework for a high common level of cybersecurity, while DORA substitutes core provisions of NIS2 via lex specialist status.
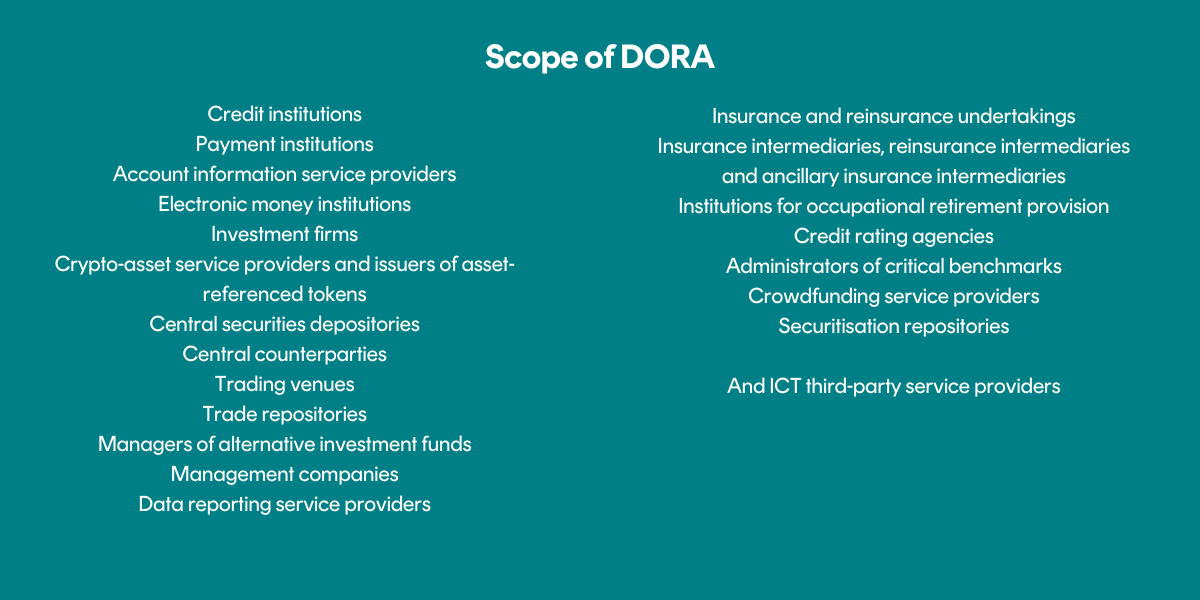
Figure 1: Scope of DORA (Microenterprises may be excluded)
DORA requires that financial entities have policies in place for the management and testing of ICT systems, controls and processes, as well as for managing ICT third-party risk. DORA also provides guidelines on incident reporting and information sharing among financial institutions (cf. Figure 2).
.png)
Figure 2: Topics covered under DORA
Key aspects of the DORA principles on ICT risk management are: Identification, Protection and Prevention, Detection, Response and Recovery, and Communication.
Protection and Prevention: Achieve DORA Compliance with Cryptomathic Key Management Solution!
Cryptomathic’s Key Management Solution is a banking-grade key management solution that is perfectly suited to address the DORA provisions for Protection and Prevention (Article 9):
.png?width=740&height=2537&name=What%20DORA%20requires%20from%20financial%20entities%20(1).png)
Figure 3: Cryptomathic Key Management Solution: a perfect match for DORA provisions on Protection and Prevention
DORA’s Article 15 mandates that some DORA requirements be further specified, including DORA Article 9.2 (ICT security policies, procedure, protocols and tools) and DORA Article 9.4(c) (Human resources policy, identity management and access control). Accordingly, the Joint Committee of the three European Supervisory Authorities (EBA, EIOPA and ESMA – the ESAs) published their first set of final draft regulatory and implementary technical standards in January 2024. JC 2023 86 expands on Articles 9.2, 9.4(c) with explicit requirements from financial institutions:
- Article 6 Encryption and Cryptographic Controls: Rules for the encryption of data at rest, in use (where necessary) and in transit; provisions for cryptographic key management; provisions to update or change the cryptographic technology on the basis of developments in cryptanalysis.
- Article 7 Cryptographic Key Management: To identify and implement controls to protect cryptographic keys through their whole life cycle; to implement methods to replace cryptographic keys in the case of lost, compromised or damaged key; to maintain a register for all certificates and certificate-storing devices and ensuring prompt renewal of certificates.
- Article 20 Identity Management: To implement identity management policies and procedures to ensure the unique identification of natural persons and systems accessing the financial entities' information, along with maintenance of records and lifecycle management process of identities.
- Article 21 Access Control: To implement and maintain a fine-grained, role-based and least-privilege based policy for granting and revoking access to ICT assets; to implement physical access control measures as well as (strong) authentication methods for remote access.
As detailed in Figure 3, the Cryptomathic Key Management Solution is perfectly suited to ensure DORA’s compliance requirements for Strong Cryptography, Key Management, Identity Management and Access Control. Further, its crypto-agile design allows for the seamless update of crypto parameters and algorithms, including the transition to quantum-secure crypto algorithms as the need arises.
DORA Affects ICT third-party providers too!
A significant part of DORA (Articles 28-44) is dedicated to risk management of ICT third-party providers - a critical element of ICT risk management, especially in view of the ever-increasing number of third-party providers.
DORA contains specific requirements on the nature and content of the contractual arrangements that financial institutions enter with ICT third-party providers, and enables monitoring of these contractual arrangements, something that was not fully anchored into EU law before.
For ICT third-party service providers deemed as critical, DORA introduces an oversight framework, along with specifics on penalties for non-compliance - up to 1% of the non-compliant provider’s average daily worldwide turnover - and the requirement of an adequate business presence in the Union to simplify enforcement.
Importantly, DORA assigns management of third-party risk to the full responsibility of the financial entity. Financial entities must:
• Integrate a strategy on ICT third-party risk into their own risk management
• Maintain a register of information in relation to all contractual arrangements on the use of third-party provided ICT services
• Be prepared to document their contractual arrangements with third-party providers to the competent authorities
• Exercise access, inspection, and audit rights over the ICT third-party provider.
Compliance with DORA provisions on third-party risk management can be challenging for financial entities. For example, when a medium-sized financial entity wants to shift their applications and infrastructure onto the cloud using a cloud service provider (CSP), such as Microsoft or Google or Amazon, enforcing the DORA auditing requirements towards these giant providers can become tricky. Some third-party providers may themselves use third parties who in turn use third parties and so on, such that the financial entity is potentially faced with verifying compliance for an entire supply chain.
Protect Your Digital Assets in the Cloud with Cryptomathic Enclave Security Module!
The secure enclave technology offered by CSPs can provide secure and isolated computing environments in the cloud, thereby enabling confidential computing and enhancing overall security in a shared cloud infrastructure. Cryptomathic has leveraged this groundbreaking technology to develop a specialized Enclave Security Module (ESM). The ESM is designed to function seamlessly within the AWS Nitro Enclave environment and serves as a robust alternative to conventional Hardware Security Modules (HSMs). The ESM adds an extra layer of security and reduces the risk of unauthorized access or leaks, ensuring that you are in full control of your cryptographic keys for their entire life cycle even when used in the cloud.
Contact us to discuss with one of our security experts how Cryptomathic can facilitate your financial institution’s compliance with DORA!