3 min read
Optimizing eIDAS with Digital Signature Deployment Models
Cryptomathic : modified on 15. December 2021
- Home >
- Optimizing eIDAS with Digital Signature Deployment Models
The eIDAS regulation provides both the technical and legal framework for electronic identification and digital signatures that the banking sector needs to fully digitalize its processes and go paperless.
When deploying eIDAS compliant digital signature services, Cryptomathic proposes three potential commercial models for financial service providers:
 Full Trust Service Provider: Cryptomathic’s technology installed on-premise, where the financial institution becomes a fully Qualified Trust Service Provider (QTSP).
Full Trust Service Provider: Cryptomathic’s technology installed on-premise, where the financial institution becomes a fully Qualified Trust Service Provider (QTSP). - Trust Service Provider “light”: Provide remote signatures as a service, where Cryptomathic operates the back-end signature services under SLA on the institution's behalf, and the financial institution becomes a QTSP.
- Signing Service Provider: For trust service provision where the financial institution receives access to an API for QES services and becomes a Registration Authority (RA).
This article focuses on the Signer Service Provider model, where the financial service provider merely operates as a registration authority. This has the advantage of significantly reducing the work involved and allows the financial institutions to focus improving the customer experience.
The general idea: Becoming a Signing Service Provider
This model delivers fully managed trust services, enabling the financial service provider to offer eIDAS compliant signing to their customers. The financial institution receives access to an API for QES services and maintains its existing liability as a Registration Authority (RA). The financial institution remains in control of all valuable customer data and is the single point of contact to the customer. Its legal liability is limited to RA. The Qualified Trust Service Provider is liable for the complete remainder of the signing process.
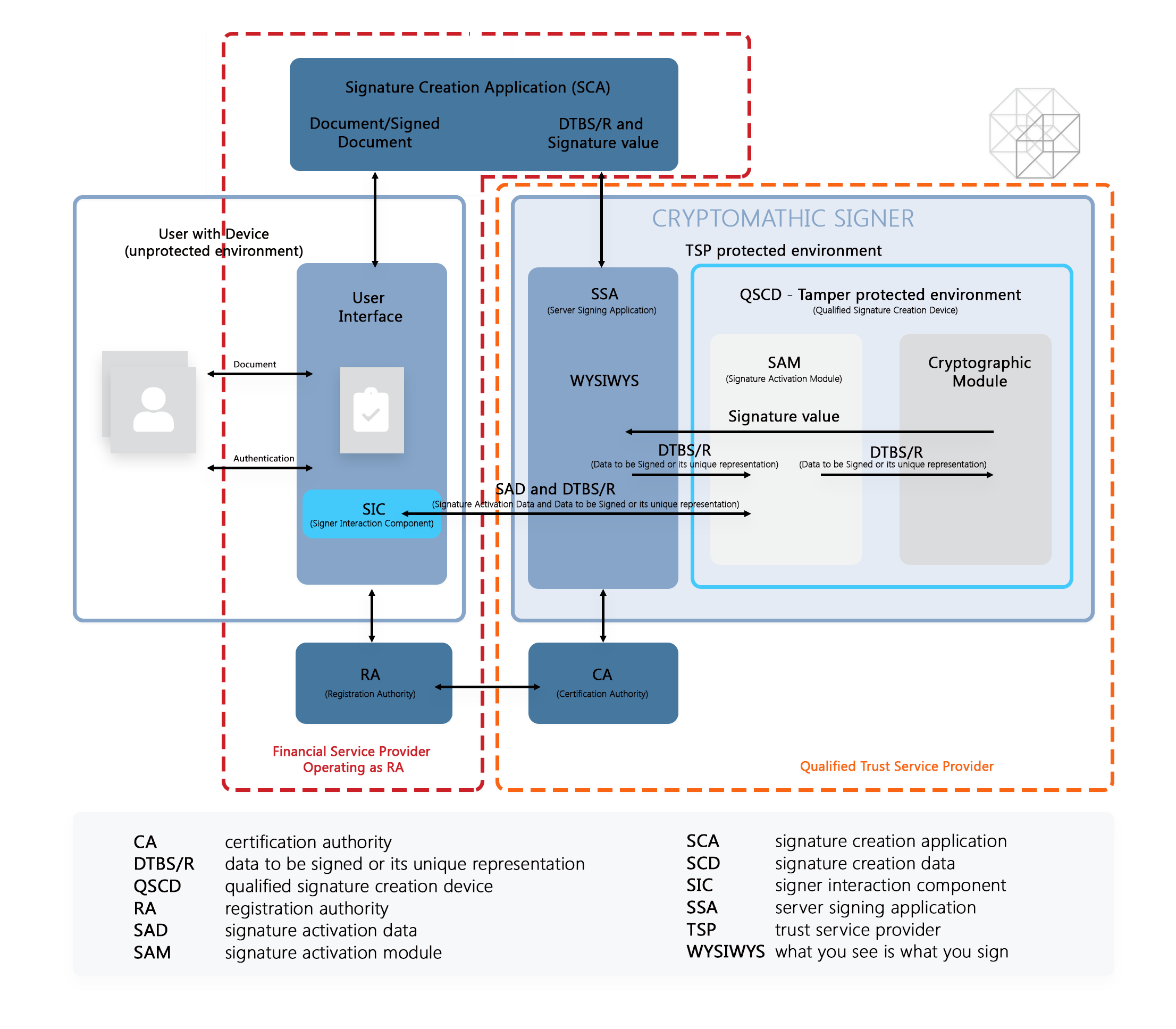
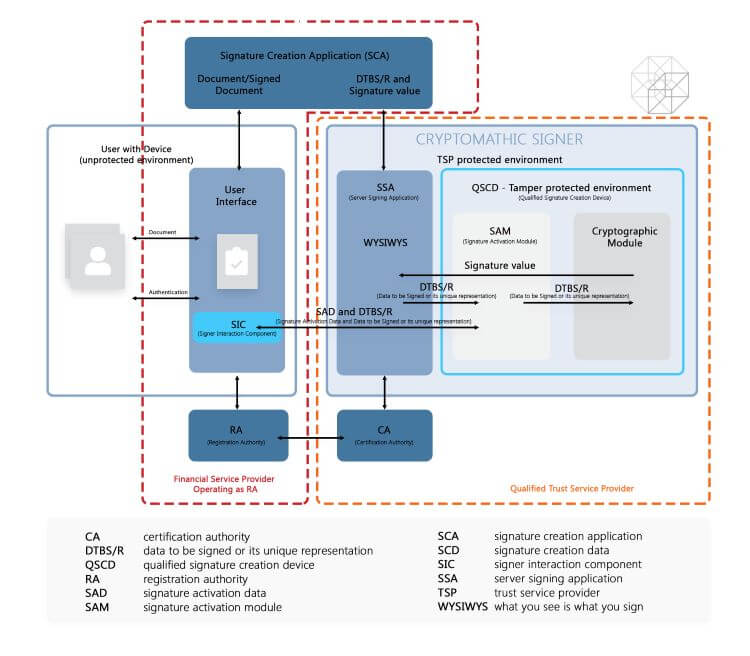
Figure: Financial Service provider operating as Registration Authority, backed by a QTSP
For a deeper understanding of the remote signing process, please look at the article: eIDAS-compliant Remote Signing with EN 419 241-2 Certified Qualified Signature Creation Devices.
Obligations of Registration Authorities
As a Registration Authority, a financial service provider has the following obligations:
- They must validate the identity and additional personal details of the certificate or information relevant to the purpose of the certificates according to associated procedures.
- They must maintain all information and documentation concerning certificates and manage their issuance, renewal, revocation, and reactivation.
- They must notify the CA of requests for certificate revocation.
- They must inform the CA of all aspects of certificate management, including issuance, renewal, and reactivation requests.
- They must validate with due diligence the reason for revocation that might affect the validity of the certificate.
- They must perform its certificate management operations in compliance with procedures established by the Trust Service Providers and current laws.
- Where applicable, they must make available to the subject the technical procedures used for signature creation data, for example, the private key, and electronic signature verification, for example, the public key.
Advantages of Being a Signature Service Provider & Registration Authority
Financial service providers will benefit from the following advantages when they operate merely as a Registration Authority:
- Direct contact with their customers. (one face to the customer)
- A significantly reduced workload as a Trust Service Provider takes care of eIDAS-compliant qualified signature creation in the back-end.
- Reduced requirement for audits because under Article 20 of the eIDAS Regulation, once qualified status is granted, the Trust Service Provider will have to provide a new conformity assessment report to their Supervisory Body every 24 months or when requested by the Body to maintain their qualified status.
This is the typical choice of banks, which operate at a limited number of locations, wanting to focus on core competencies and end customer business.
Business relationship with Cryptomathic
Cryptomathic offers a qualified trust service, provided as-a-service, audited and ready to be integrated with the bank’s processes:
- The financial service provider
- gets access to an API and can leverage its legacy IT setup.
- enforces the terms of the CP/CPS for eIDAS or other legislation
- may connect to additional certificate service providers
- operates the registration authority function
- The appointed TSP(s)
- are legally liable for the signature service
- delegate the RA + Authentication to the financial service provider. This delegation will be assessed with respect to conformity by an external auditor
Comparison of the 3 available packages offered by Cryptomathic
The following infographic compares the 3 different packages offered by Cryptomathic based on their technical implementation.
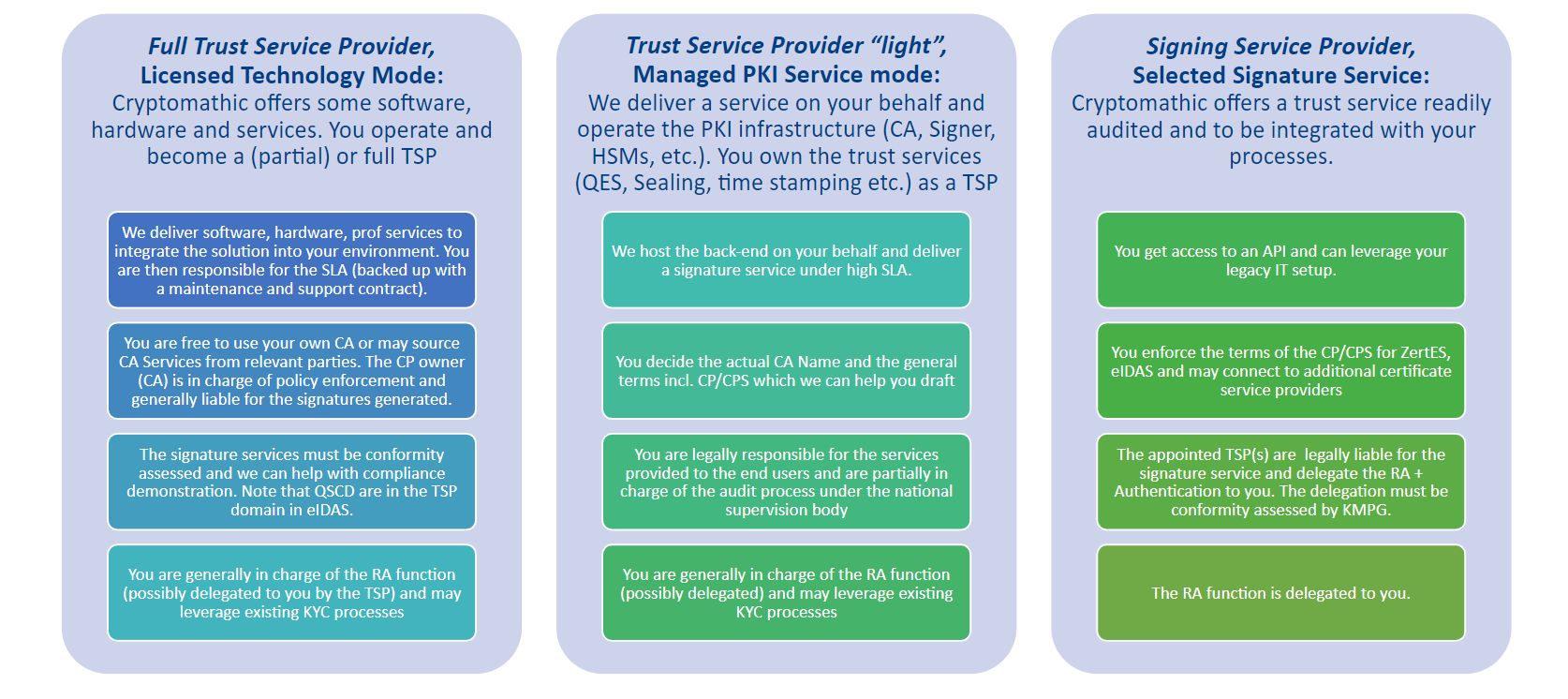
Figure: Implementation / Delivery Options
References
- Selected articles on eIDAS (2014-today), by Gaurav Sharma, Guillaume Forget, Jan Kjaersgaard, Dawn M. Turner, and more
- CEN/TC 224 - Trustworthy Systems Supporting Server Signing Part 2: Protection Profile for QSCD for Server Signing (05.2018), by AFNOR
- Conformity assessment of Trust Service Providers - Technical guidelines on trust services (2017), by the European Agency for Cyber Security
- Mutual Recognition Agreement of Information Technology Security Evaluation Certificates, VERSION 3.0 (Jan, 2010), SOG-IS
- Trustworthy Systems Supporting Server Signing Part 2: Protection
Profile for QSCD for Server Signing (2019) by CEN/TC 224 - About The Common Criteria (retrieved October 2020), by Common Criteria
- Digital Trade and Trade Financing - Embracing and Shaping the Transformation (2018), by SWIFT & OPUS Advisory Services International Inc
- REGULATION (EU) No 1316/2013 establishing the Connecting Europe Facility, amending Regulation (EU) No 913/2010 and repealing Regulations (EC) No 680/2007 and (EC) No 67/2010(12/2013), by the European Parliament and the European Council
- Selected articles on Electronic Signing and Digital Signatures (2014-today), by Ashiq JA, Gaurav Sharma, Guillaume Forget, Jan Kjaersgaard , Peter Landrock, Torben Pedersen, Dawn M. Turner, and more
- The European Interoperability Framework - Implementation Strategy (2017), by the European Commission
