7 min read
Digital authentication - factors, mechanisms and schemes
Cryptomathic : modified on 05. January 2017

- Home >
- Digital authentication - factors, mechanisms and schemes
Indiana University defines authentication as "the process of determining whether someone or something is who or what it is declared to be." Similarly, digital authentication is about having suitably secure mechanisms in place to be able to confirm whether an individual or online user is who they say they are.
This article gives a comprehensive insight into digital authentication and the IT-enabled processes and architectures needed.
Historically, the way in which we identify ourselves to an action or situation has been changing, since earlier times. The earliest forms of identifying a person were practically based on eye contact and physical appearance. Then, in ancient Mesopotamia, the Sumerians used seals in form of a cylinder shaped stone, ceramic or glass with particular symbols that gave authenticity to their writings. Over the years, the hand-written signature evolved as the most common way of authentication (often supported by a stamp). Signatures could become quite artistic; the stylish "k" of John Hancock's signature under the US Declaration of Independence literally wrote history. In recent decades. technically enabled authentication has become increasingly important.

Identification and Authentication
Today, for many day-to-day tasks, an authentication process is needed, from e-banking, to accessing a building to travelling throughout the world. Authenticating a persons identity is a way of protecting people and their assets, but also for making people responsible for their own actions. Authentication of a person is often delegated to technically enabled processes that have been verified and regulated by a government's or agency's rigorous procedures.
For identification, we have driver's licenses, passports, national identity documents, military documents, residential and Social Security cards. All these documents could have some elements in common that can be used to authenticate the person's identity, like fingerprints, handwritten signatures and even pictures of the person. Aditionally, for a person to get these documents for the first time, they must pass through a series of prerequisites that add to the identity of the person, like checking their banking account, credit cards and residential services invoices to prove their identity.
 An identity document (ID) can be described as a document to prove someone’s identity with certainty. Historically, they came in various forms depending on the country. The most accepted identification document worldwide is the passport, that maintains some international standards.
An identity document (ID) can be described as a document to prove someone’s identity with certainty. Historically, they came in various forms depending on the country. The most accepted identification document worldwide is the passport, that maintains some international standards.
For digital operations, things get a bit more complex. However, authentication principles are very similar, meaning that a set of fingerprints still has its validity as a biometrical authentication factor with software that recognizes fingerprints. There is a variety of different methods for authenticating users online (passwords, OTPs, biometrics, etc.), where the most secure methods combine different authentication factors.
Authentication Factors
For digital identity, considering that at first glance it looks a little abstract, there are three accepted mechanisms that give life to digital authentication:
 Knowledge Factor (Something the person knows)
Knowledge Factor (Something the person knows)
(E.g. passwords, challenges, PIN, ID numbers, etc.)
- Possession Factor (Something the person has)
(E.g. Token, Cards, mobile phone, Matrix, etc.)
- Biometric Factor (Something the person is)

(E.g. Fingerprints, voice patterns, Retinal or Iris Scan, etc.)
 It is no secret that the most convenient and convincing factor of the three is the biometric, but at the same time it is one of the most expensive. However, each factor may have its own weaknesses, but by combining at least two of them, the authentication itself can become very robust and strong. The recommendation is to always use multifactor authentication, in which at least two factors are used.
It is no secret that the most convenient and convincing factor of the three is the biometric, but at the same time it is one of the most expensive. However, each factor may have its own weaknesses, but by combining at least two of them, the authentication itself can become very robust and strong. The recommendation is to always use multifactor authentication, in which at least two factors are used.
Types of authentication
 Passwords (Knowledge Factor): Based on a string of information that is only known by the person, a pasword is presented to the entity that makes the authentication. This is the most common type of authentication used and at the same time, one of the most vulnerable. A poorly chosen password may fall into the known category of low hanging fruit, in which the password is usually: the same login, the user´s name or last name, date of birth, blank password, qwerty and in the best case, common dictionary words. The most common threats are social engineering, insecurely stored passwords, etc.
Passwords (Knowledge Factor): Based on a string of information that is only known by the person, a pasword is presented to the entity that makes the authentication. This is the most common type of authentication used and at the same time, one of the most vulnerable. A poorly chosen password may fall into the known category of low hanging fruit, in which the password is usually: the same login, the user´s name or last name, date of birth, blank password, qwerty and in the best case, common dictionary words. The most common threats are social engineering, insecurely stored passwords, etc.
 One Time Passwords (Possession Factor): This is also a password, but can only be used once and it changes dynamically with each use. This type of password can be used with digital devices (tokens) that the user has in his possession or the password is simple printed in a coordinates arrays paper (cheaper but more vulnerable).
One Time Passwords (Possession Factor): This is also a password, but can only be used once and it changes dynamically with each use. This type of password can be used with digital devices (tokens) that the user has in his possession or the password is simple printed in a coordinates arrays paper (cheaper but more vulnerable).
 Challenge-Response (Knowledge & Possession Factor): In this type of authentication, a token (Possession) is normally used, unblocked by a PIN (Knowledge) and a challenge is generated from the authentication system (knowledge). The only thing that travels over the network is the challenge and the challenge response (The PIN never travels through the network).
Challenge-Response (Knowledge & Possession Factor): In this type of authentication, a token (Possession) is normally used, unblocked by a PIN (Knowledge) and a challenge is generated from the authentication system (knowledge). The only thing that travels over the network is the challenge and the challenge response (The PIN never travels through the network).
 Network Challenge-Response (Two Factors & Channels): In these cases, we use a different way to generate the challenge and response. Usually this is done through something that is owned and possessed by the user and can be controlled by them. It could be an SMS or a voice call that the authentication system sends to them. Note that the mechanism does not use the same channel that the application may use through the data network. It is also common to use an Email, which delegates its authentication to the Email Company such as Google, Microsoft or even a Social Network.
Network Challenge-Response (Two Factors & Channels): In these cases, we use a different way to generate the challenge and response. Usually this is done through something that is owned and possessed by the user and can be controlled by them. It could be an SMS or a voice call that the authentication system sends to them. Note that the mechanism does not use the same channel that the application may use through the data network. It is also common to use an Email, which delegates its authentication to the Email Company such as Google, Microsoft or even a Social Network.
 Software Tokens: They use the same hardware token concept, but it is done through software and is installed on the user´s device through a secure provisioning process. It is much cheaper, but also has all the vulnerabilities that all software may have, for example, malware.
Software Tokens: They use the same hardware token concept, but it is done through software and is installed on the user´s device through a secure provisioning process. It is much cheaper, but also has all the vulnerabilities that all software may have, for example, malware.
 Public & Private Key / Digital Certificates (Knowledge and Possession Factor): Digital Certificates are the product of a complex process that is part of a public key infrastructure (PKI). The digital certificate stores the user´s public key, which is distributed to its peers, while only the user has access to the private key that also is protected by a passphrase. Remember that there is always a unique mathematical correlation between the public and the private key (One used to encrypt or sign and the other used to decrypt and verify the signature). All the interactive exchange is performed through the Secure Socket Layer (SSL) protocol.
Public & Private Key / Digital Certificates (Knowledge and Possession Factor): Digital Certificates are the product of a complex process that is part of a public key infrastructure (PKI). The digital certificate stores the user´s public key, which is distributed to its peers, while only the user has access to the private key that also is protected by a passphrase. Remember that there is always a unique mathematical correlation between the public and the private key (One used to encrypt or sign and the other used to decrypt and verify the signature). All the interactive exchange is performed through the Secure Socket Layer (SSL) protocol.
 Hardware Tokens: (Possession and Knowledge Factors): These devices are capable of securely storing the private key and the corresponding digital certificate, so this is not stored in any other device (such as in the case of a software token). To access these devices, such as USB tokens, you should use a password or passphrase (Knowledge factor). Smartcards are also used as hardware tokens, but not being USB, they would require the appropriate readers (additional costs).
Hardware Tokens: (Possession and Knowledge Factors): These devices are capable of securely storing the private key and the corresponding digital certificate, so this is not stored in any other device (such as in the case of a software token). To access these devices, such as USB tokens, you should use a password or passphrase (Knowledge factor). Smartcards are also used as hardware tokens, but not being USB, they would require the appropriate readers (additional costs).
 Fingerprints, Iris or Retina Scanning (Being Factor): For this type of authentication it is required that the user has access to specialized devices that can scan fingerprints, retina or maybe the iris. Also, it can be done by voice recognition. Increasingly, manufacturers are introducing this type of readers or scanners on their devices (Laptops, Phones, Computers, tablets, etc.)
Fingerprints, Iris or Retina Scanning (Being Factor): For this type of authentication it is required that the user has access to specialized devices that can scan fingerprints, retina or maybe the iris. Also, it can be done by voice recognition. Increasingly, manufacturers are introducing this type of readers or scanners on their devices (Laptops, Phones, Computers, tablets, etc.)
Authentication Schemes
- Local Authentication
- Centralized Authentication
- Global Centralized Authentication
- Global Centralized Authentication and Web Application (Portal)
Local Authentication
In this authentication scheme, each application retains data related to user credentials and typically is not shared with other applications. This scheme can result in the user of the service having to maintain and remember many different types of credentials according to the service that they require access to. As an example, it can be mentioned that different government agencies, in which each one of them offer their own services, manage isolated credential databases.

Centralized Authentication
Under this scheme, each user runs the same credentials to access the various services required. Still, each application is different and must have the interfaces and necessary agreements to interact with the central system to finally authenticate the user. In this way, the user can have easier access to important information across a range of services, including the access to private keys that could be used to sign documents.

Global Centralized Authentication
With this scheme, the user can access the authentication services directly through a third party, so it can access all the services that they need.

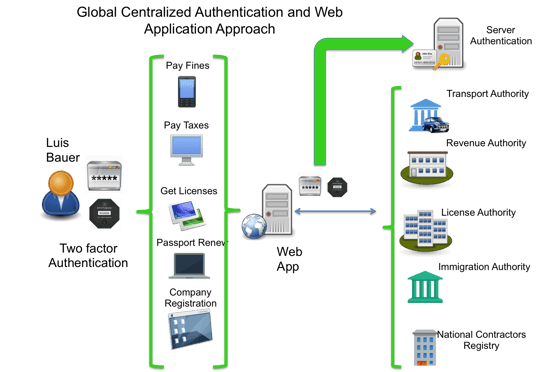
Global Centralized Authentication and Web Application (Portal)
This form of authentication, ideally for E-Government, uses common applications and web portals to access a wide range of services, from which it can use a single authentication mechanism with at least two factors, so the required services can be accessed, including the possibility to sign documents.
Mobile Authentication
 The use of mobile devices is not new and it is no secret that there has been of massive use for several years. From laptops to smartphones, tablets and wearables, these mechanisms involve greater versatility in the use of the services, but increase the risk significantly. Still, the mere fact of it being a mobile device means it has already passed through a regular provisioning process and signing contracts provided by the mobile operator. Mobile can be used for an out of band authentication, reducing risk and making it difficult for a black hat hacker to compromise all factors together. That being said, authentication by SMS or a voice call is a valid mechanism that could be used as a
The use of mobile devices is not new and it is no secret that there has been of massive use for several years. From laptops to smartphones, tablets and wearables, these mechanisms involve greater versatility in the use of the services, but increase the risk significantly. Still, the mere fact of it being a mobile device means it has already passed through a regular provisioning process and signing contracts provided by the mobile operator. Mobile can be used for an out of band authentication, reducing risk and making it difficult for a black hat hacker to compromise all factors together. That being said, authentication by SMS or a voice call is a valid mechanism that could be used as a  second factor authentication in the possession factor field “something the user has… and owns”. Also, many of these devices today come with biometric authentication (local), but this feature indicates that biometric authentication may not be too distant to integrate with systems, and with lower prices.
second factor authentication in the possession factor field “something the user has… and owns”. Also, many of these devices today come with biometric authentication (local), but this feature indicates that biometric authentication may not be too distant to integrate with systems, and with lower prices.
Authentication and Digital Signing working together
It is essential that the authentication process maintains a minimum of two factors of different categories. With this, there are more guarantees to securely access the desired service. One of the services that provides significant advances in terms of Non Repudiation of Origin (NRO) and Non Repudiation of Emission (NRE) should be the access and use of a user's private key for signing documents, whose scope is legal, as supported by The Regulation (EU) N°910/2014 on electronic identification (EIDAS). That being said, the private key used to sign and accessed by n-Factor authentication should be protected by specialized hardware, so that only the user in control of all the authentication factors can access this key to sign their documents. If this is centrally managed and protected, the necessary auditing mechanisms that can serve as legal evidence in any legal process can be performed.

The Future
The evolution of all services into the digital world, such as signing e-documents, also requires the security mechanisms to evolve, including of course authentication mechanisms. The use of passwords will remain for some time and even more so those types that use certificates with PKI. Multifactor authentication is a must and biometric technology use is obviously increasing. Also, mechanism that may use patterns for the behavior of the user through the use of the application (E.g., behavior and usage statistics in the application, key press patterns, average amounts used in transactions, etc.) may be used in the future. All this of course, also using the Multifactor authentication.
References and Further Reading
- Selected articles on Authentication (2014-16), by Heather Walker, Luis Balbas, Guillaume Forget and Dawn M. Turner
- Selected articles on Electronic Signing and Digital Signatures (2014-16), by Ashiq JA, Guillaume Forget, Peter Landrock, Torben Pedersen, Dawn M. Turner and Tricia Wittig
- REGULATION (EU) No 910/2014 on electronic identification and trust services for electronic transactions in the internal market and repealing Directive 1999/93/EC (2014) by the European Parliament and the European Commission
- Recommendations for the Security of Internet Payments (Final Version) (2013), by the European Central Bank
- Draft NIST Special Publication 800-63-3: Digital Authentication Guideline (2016), by the National Institute of Standards and Technology, USA.
- NIST Special Publication 800-63-2: Electronic Authentication Guideline (2013), by the National Institute of Standards and Technology, USA.
- Security Controls Related to Internet Banking Services (2016), Hong Kong Monetary Authority
Image: "Basic Authentication", courtesy of Paul Downey, (CC BY-ND 2.0)

