4 min read
Hash Functions & Algorithms: What Are The Differences
Cryptomathic : modified on 24. October 2019
- Home >
- Hash Functions & Algorithms: What Are The Differences
Cryptographic algorithms can be categorized into three classes: hash functions, symmetric, and asymmetric algorithms. This article sheds light on their differences, purposes, and main fields of application.
1. Security Services
A lot of security services such as confidentiality, integrity, authentication, and non-repudiation can be provided by using cryptographic algorithms.
1.1 Confidentiality
Confidentiality serves the purpose of ensuring that information is not revealed to unauthorized entities. Confidentiality is achieved by transforming the understandable information into a state that is unintelligible except to authorized entities. This transformation mechanism is called encryption. Decryption of unintelligible data is performed to restore it to its original state. Both symmetric and asymmetric algorithms can provide encryption. Confidentiality is not only important for data at rest but also for network communication data.
1.2 Data Integrity
Integrity is a mechanism that assures that the data has not been altered in an unapproved way. The integrity of data is maintained at the creation, transmission, and storage phases. Alteration of data includes insertion, deletion, and substitution breaches. Digital signatures and message authentication codes (MAC) are the cryptographic mechanisms that can be used to notice both intentional and accidental alterations.
1.3 Authentication
There are 2 types of authentication services that can be achieved using cryptography solutions, i.e., source and integrity authentication. Source authentication assures the identity of the entity that originally generated or crafted the information. Integrity authentication validates that data has not been modified and that the integrity of the data is protected.
1.4 Non-Repudiation
Non-repudiation is the guarantee that no one can deny a transaction. The term "non-repudiation" is frequently used for digital signatures and email messages. When a data hashing algorithm is combined with public or private keys, data origination authentication can be achieved. The well-known technique of data origin authentication is using digital certificates.
2. Importance of Guidance on Cryptographic Algorithms
The proper approach to incorporate security services for applications and protocols dealing with data security is the use of cryptographic methods. A lot of public/open source and proprietary algorithms are available. Users and developers are presented with many new choices in their use of cryptographic mechanisms. Adoptions of obsolete or less known/indigenous algorithms may result in a security breach of data and information. Public and NIST approved algorithms have undergone rigorous security testing and cryptanalysis prior to their approval, to assure that the algorithms provide satisfactory security. The document “NIST Special Publication 800-57 Part 1 Revision 4” provides background information and establishes frameworks to support appropriate decisions when selecting and using cryptographic mechanisms.
3. Importance of Keys in an Algorithm
 Keys in the field of cryptography solutions are analogous to the pattern/PIN/password or physical key applied to a security locker. Appropriate encryption key management solutions are essential for the operative use of cryptography. If an attacker is able to find out the combination of security locker, whatever state-of-the-art and however strong technology, the locker will fail. A security locker is analogous to an encryption algorithm. If the keys are not managed properly, encryption algorithms will be compromised.
Keys in the field of cryptography solutions are analogous to the pattern/PIN/password or physical key applied to a security locker. Appropriate encryption key management solutions are essential for the operative use of cryptography. If an attacker is able to find out the combination of security locker, whatever state-of-the-art and however strong technology, the locker will fail. A security locker is analogous to an encryption algorithm. If the keys are not managed properly, encryption algorithms will be compromised.
The 1st and last phases in the life of a key are generation and destruction respectively.
The other phases in the life of a key are securing storage, distribution, modification, renewal, backup/archival, revocation/suspension etc. Keys require encryption key management solutions and protection in all phases of life. The protection may include compromise, modification and unauthorized disclosure. NIST publishes Federal Information Processing Standards (FIPS) and NIST Recommendations that stipulate cryptographic procedures for protecting unclassified and sensitive information.
 4. Classes of Cryptographic Algorithms
4. Classes of Cryptographic Algorithms
Cryptographic algorithms can be categorized into three classes. This categorization is defined on basis of the number of cryptographic keys that are required for the algorithm.
- Hash Functions
- Symmetric-Key Algorithms
- Asymmetric-Key Algorithms
4.1 Hash Functions
Hash functions are the building blocks for modern cryptography. A hash function is a cryptographic algorithm which is used to transform large random size data to small fixed size data. The data output of the hash algorithm is called hash value or digest. The basic operation of hash functions does not need any key and operate in a one-way manner. The one-way operation means that it is impossible to compute the input from a particular output. The basic uses of hash functions are:
- Generation and verification of digital signatures
- Checksum/Message integrity checks
- Source integrity services via MAC
- Derivation of sub-keys in key-establishment protocols & algorithms
- Generation of pseudorandom numbers
4.2 Symmetric-key algorithms
Symmetric-key algorithms also referred as secret-key algorithms use a single cryptographic key for encryption and decryption purposes. They convert data in a way that is problematic for an opponent to decrypt the data without the key. Symmetric keys are securely generated and distributed to the sender and receiver and are unknown to any other entity. But if a symmetric-key algorithm is being used by more than one receiver then the key has to be shared with all entities. If the key is compromised from one entity, communication of all the entities will be compromised. Symmetric Algorithms are further divided into Block & Stream algorithms. A block algorithm breaks the input into fixed-size blocks and then progresses the crypto operations. Stream algorithms perform “bit-by-bit” crypto operations. Primary purposes of symmetric key algorithms are:
- Confidentiality is achieved as encryption and decryption is performed using single key.
- Integrity and source authentication is achieved by using Message Authentication Codes because the MAC is generated and validated by the same key.
- Generation of pseudorandom random numbers
4.3 Asymmetric-key algorithms
Asymmetric-key algorithms are commonly referred to as “public-key algorithms”. They use two mathematically associated keys knows as public and private keys. One key is used for data encryption, and the other is used for decryption of data. The combination of a public and private key is called a key pair. The private key is always kept secret by the owner. The public key is distributed to the public and everyone can access it. The private key cannot be deduced from the public key. The public key is mostly bound to an identity by a Certificate Authority. Asymmetric-key algorithms are mostly based on mathematical problems like integer factorization and discrete logarithm problem. Main uses of asymmetric algorithms are:
- Creation of digital signatures
- To establish/distribute session keys such as in case of TLS protocol
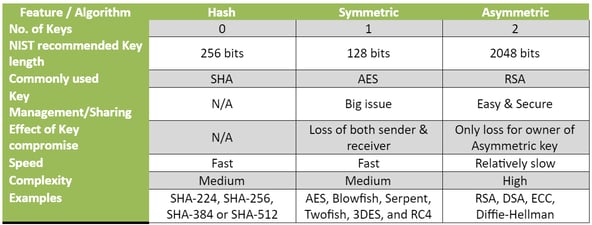
5. Differences between Hash functions, Symmetric, and Asymmetric algorithms
A tabular chart is listed based on some characteristics of the algorithms.
6. Combination of Symmetric and Asymmetric algorithms
Due to the above characteristics, symmetric and asymmetric algorithms are sometimes used in a hybrid approach. Asymmetric ciphers are characteristically used for identity authentication performed via digital signatures & certificates, for the distribution of symmetric bulk encryption key, non-repudiation services and for key agreement. Symmetric ciphers are used for bulk encryption of data due to their fast speed.

References and Further Reading
- Selected articles on Key Management (2012-16), by Ashiq JA, Chuck Easttom, Dawn M. Turner, Guillaume Forget, James H. Reinholm, Matt Landrock, Peter Landrock, Steve Marshall, Torben Pedersen, Maria Stokes, John Trankenschuh and more
- NIST Special Publication 800-57 Part 1 Revision 4 Recommendation for Key Management Part 1: General (2016), by Elaine Barker, Computer Security Division Information Technology Laboratory, National Institute of Standards and Technology
- Predictions 2017: Customer-Obsessed Enterprises Launch Cloud’s Second Decade (November 2016)
- “Cybersecurity Incidents What Happened.” (2016), the United States Office of Personnel Management.
Image: "Hash Tag", courtesy of Michael Coghlan, (CC BY-SA 2.0)
