THE DIGITAL SIGNING SOLUTION & SUITE FOR THE EIDAS ECOSYSTEM AND BEYOND
THE CORE BUILDING BLOCKS TO CREATE YOUR OWN QUALIFIED ELECTRONIC SIGNATURE SERVICE
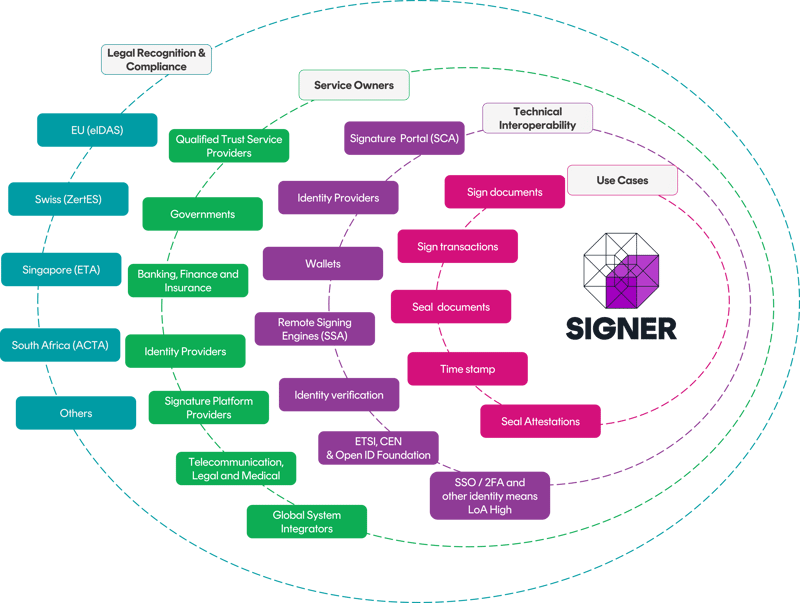
Signer is a product suite that enables qualified trust service providers, governments, system integrators, and financial institutions to create a highly scalable and performant qualified remote electronic signature or sealing service
Signer is a modular solution used by our customers and partners to create the ideal electronic signing architecture for several use cases across qualified signing and sealing. The modular approach allows organizations to reuse existing infrastructure such as identity management, signing portals or established business flows with minimal disruption that will affect your customers.
Signer is also a great fit if you are building a new remote signing service from scratch and need flexibility to have it your way.
Signer consists of 3 modules that align with the eIDAS regulation.
The three modules are:
1. Signature Creation Application (SCA)
2. Signing Server Application (SSA)
3. Remote Qualified Signature/Seal Creation Device (rQSCD)

Qualified Trust Service Providers
Our technology is the underlying architecture for many qualified trust service providers across EU. We offer the modules to create a qualified remote signing service to serve private and public customers, and we are often brought in to consult and optimize existing solutions with our certified technology and expertise without breaking the flows for existing customers. We provide guidance and products that are compliant-by-design to reduce the ever-increasing compliance burden for qualified trust service providers.
National Signing Services
Our solution is behind several state signing services, often supported by system integrators on their behalf. Our good relationship with global system integrators stems from our commitment to standards. Industry and internet standards and standardized APIs make it easy for developers to integrate to other systems and easy for larger IT service companies to bid on government RFPs with confidence. We back this with a cost structure that increases long-term predictability to minimize the project’s risk for all involved parties.
Banking, financial services, insurance, and other high-trust companies
We support many companies in the high trust segment like banking, financial services, and insurance (BFSI). Signing is often used to onboard customers and digital remote onboarding can be a great customer experience or even a differentiator for companies with an international customer base or clients travelling a lot. QES offers the legal certainty needed to support high value transactions, and along with the ability to offer full privacy and confidentiality for your clients, is a winning formula. Further, BFSI brings existing infrastructure that makes the composability of our suite attractive to repurpose, for example identity management solutions.
Signature platform, Identity Providers and companies wanting to become qualified trust service providers
Are you looking to add qualified signatures to your offering? We have supported many customers to tap into the growing eIDAS ecosystem and open new doors to customers in the more security sensitive segments. Whether you want to be your own qualified trust service providers or want to take advantage of a service, we can get you to market quickly with a range of products and services that supports you in this journey.
One signature platform, multiple levels of trust
Not every document carries the same risk profile - why apply identical security measures to all? Cryptomathic SIGNER is a unified signing platform that allows organizations to seamlessly choose between Qualified, Advanced, and Simple electronic signatures. This flexibility ensures each workflow is secured with precisely the level of assurance it requires, without unnecessary complexity or cost.
Efficient signing flows, governed by a unified policy library
- One centralized policy library, no code changes and no tool swapping - Select the appropriate level of signature assurance for each transaction via API or UI toggle, all without any code modifications.
- Optimized user journeys - High-risk transactions require signers to undergo Know-Your-Customer (KYC) verification, while everyday users enjoy a streamlined, low-friction signing process that improves speed and conversion rates.
- Cost control - Incur the expense of Qualified-level identity verification only when warranted by a document’s risk profile, keeping routine signature operations efficient and cost-effective.
Deliver the right level of trust for every transaction, without the complexity of juggling multiple signature tools.
Signing and Sealing: Signer is a dual-purpose solution
Despite Signer being used in a wide range of contexts, we normally work with 2 overarching use cases: signing and sealing. Signer can solve both use cases and is a highly cost-effective solution especially if you have both use cases.
Signing is done by a person (natural person) and is used to show agreement between two or more parties in, for instance, a contract. A natural person can also sign on behalf of a company or organization.
Sealing on the other hand is done by an organization (legal entity) to prove authenticity, integrity and to offer non-repudiation for documents or data. In other words, the organization stands by issuing this document and a seal is the proof. Sealing is currently seeing a lot of attention due to the rise of AI supported fraud.
%20Used%20for%20Agreements%20Contracts%20Onboarding%20customers%20Financin%20(4).png)
A flexible signing suite for any use case
eIDAS is an EU legal framework that defines how to sign electronically, but that can be implemented in many ways.
Our signing suite enables full flexibility to create a composable signing architecture.
The animation below shows 11 architectures all solving different use cases.
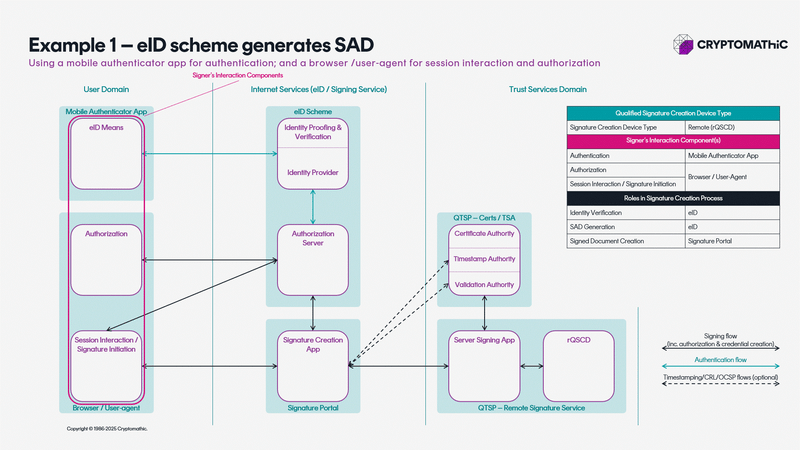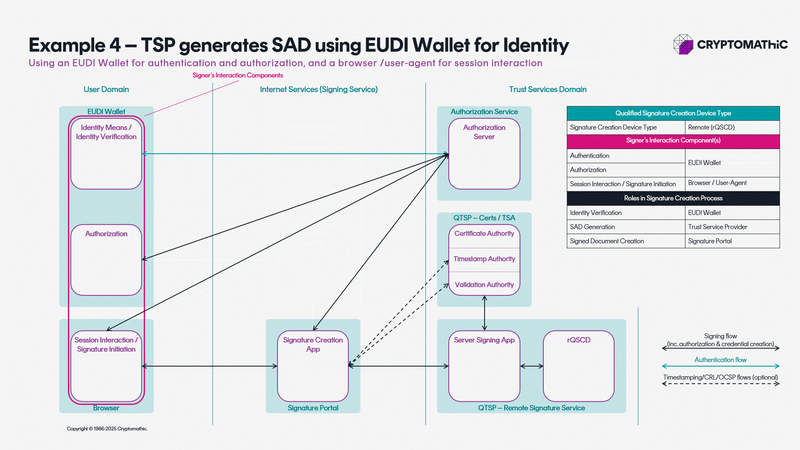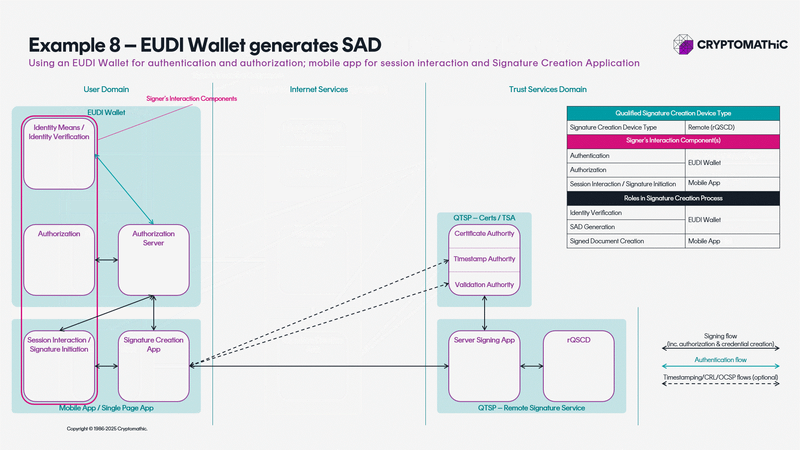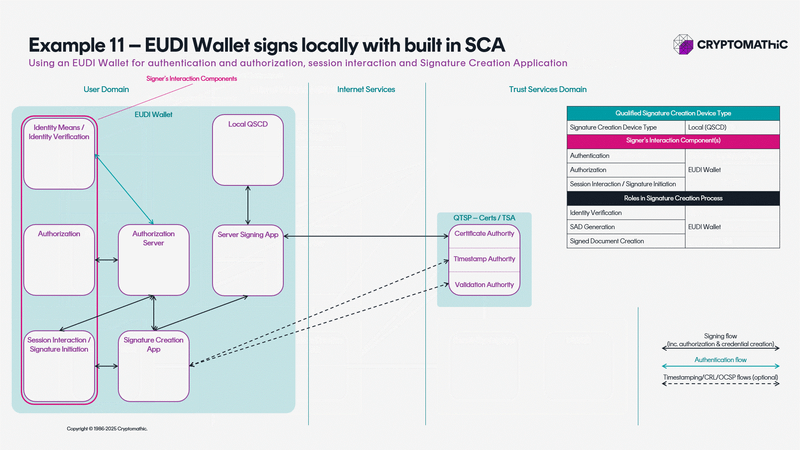
A BUYERS GUIDE TO SELECTING THE RIGHT QUALIFIED SIGNING AND SEALING SOLUTION
Incorporating a Qualified Electronic Signature solution is essential for organizations that require the highest level of legal assurance, security, and compliance in their electronic transactions.
It not only ensures adherence to regulatory standards, but also enhances trust and efficiency in digital interactions.
In this guide, you will find a list of essential questions to ask your supplier. One list helps vet the supplier, while the other qualifies the product.
All questions are structured as yes/no, and you want to see ‘Yes’ answers!
This is a general list that may slightly vary depending on the use case. However, a vendor that checks all these boxes will be well-equipped to future-proof your operations, and support your business’ long-term scalability.
Download Buyers Guide

WHAT OUR CLIENTS SAY
Previously, our clients had to print, sign and send documents manually for compliance reasons.
Now they can do it in a smart, easy and time-saving way. Thanks to the Cryptomathic Signer solution they can sign their contracts digitally in e-Banking – while meeting all legal and compliance requirements
Andreas Kubli, Head Multichannel Management & Digitization, UBS Switzerland
