5 min read
E-Government Authentication & Signing: Centralized Solutions
Cryptomathic : 05. October 2022

- Home >
- E-Government Authentication & Signing: Centralized Solutions
Achieve Non-Repudiation of Origin (NRO) and Non-Repudiation of Emission (NRE)
This article explains how NRO and NRE processes relating to central authentication and signing can make e-Government more secure.
The term non-repudiation is generally used when there is a legal problem in which a person denies authenticity and integrity of any fact or transaction he has committed.
There are some analogies that can help to explain this concept. If we can go back to the 1986 Football World Cup in Mexico, an event, namely, “The hand of God” was where, in a game between England and Argentina, Argentina star player, Maradona, scored a goal with his hand to lead the South American team to victory and finally, to become the World Cup Champions.
Who apparently didn’t see the hand action? Referees
Who alleged that Maradona scored the goal with his hand (as it really happened)? English players (and the English public of course)
Who celebrated the goal while watching the referees’ reactions and denied the action of the hand goal? Maradona and his teammates
Do video replays clearly show the hand of Maradona during the action? Yes
Videos of that action clearly showed the “Hand of God episode”. However, it was 20 years later (and 20 years of repudiation) that the Argentinian player publicly admitted that he did score the goal with his hand. However, such confirmation will not change the results of the Mexico 86 World Cup. Technology and football rules were not enough to determine non-repudiation.
For a country and its Government, what can be more important than its citizens’ protection and to gain their trust? The citizens of a country become the main client for e-Government processes and we are talking about hundreds of thousands, even millions of people doing transactions.
NRO and NRE; what it means?
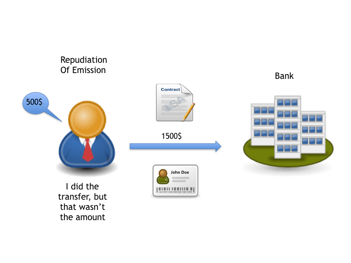
Non-Repudiation of Origins (NRO) makes a link between the message and the sender of the message. It can provide legal evidence that a person, in fact, sent the message.
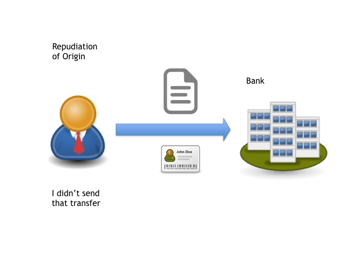
Non-Repudiation of Emission (NRE) makes a link between the sender of the message and the content of the message. It can provide legal evidence that a person sent that specific message.
When conducting a transaction or signing a document in the real world, a citizen is likely to show some form of approved identification to authenticate themselves in-person to the Government department. Secondly, the citizen may also provide their handwritten signature to a paper document in order to establish that the agreement is legally binding and non-repudiable.
In the digital world, secure online access to e-Gov services is commonly provided by using 2-factor- or strong authentication. By leveraging strong authentication, applying a digital signature can provide the same legal value as a handwritten one, provided the approved security and regulatory measures are in place.
Of course, this is not so simple when e-Gov services are spread across numerous entities and online systems that may use different methods of identification and athentication.
One country, One Government, Many citizens
Is it a good practice that every citizen has an identification record in each entity of the Government?
Is it possible to have 100 state entities and 100 identities (for the same citizen)? Is that convenient?
Is it good to delegate all security measures to the variety of devices that the citizen has?
One Government -> One citizen with a unique identity: As an entity, the Government requires that each of its citizens is identified as unique. This correspondence suggests that the Government should have a way to identify their citizens for any transaction or services that the Government offers to them. This means that the various Government entities require identifying its citizens with a unique identity, despite of having different applications and systems. This could imply having unified databases and controls for storing user information identities.
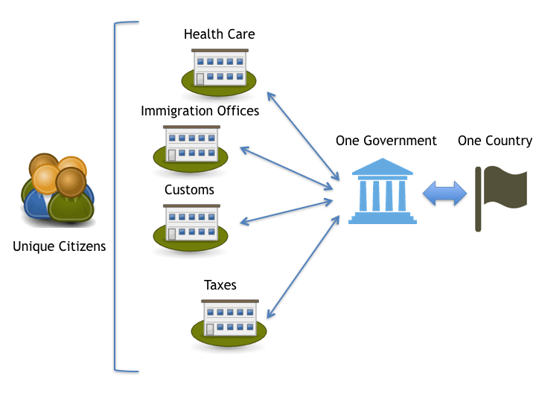
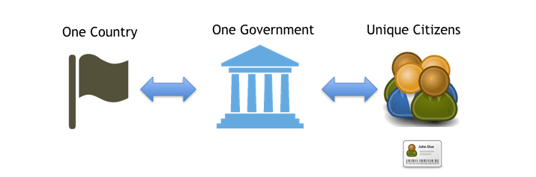 One Citizen -> One Government that offers different services: for the citizen, regardless of the transaction he is performing, he does this by facing only one Government. This suggests that the same identity element should work for identifying the citizen to any Government agency.
One Citizen -> One Government that offers different services: for the citizen, regardless of the transaction he is performing, he does this by facing only one Government. This suggests that the same identity element should work for identifying the citizen to any Government agency.
Government CIO Challenges
A Government CIO will know the advantages of efficient e-Government processes, such as:
- Better and faster interactions with citizens through web portals
- Simplification of procedures
- Use of electronic documentation
- Less paper waste
- Accountability
- Effective communication between Government entities.
There are, however, significant risks within the Government environment with respect to malicious intrusion and data misuse.
The basic principles of Information Security apply equally in the context of E-Government
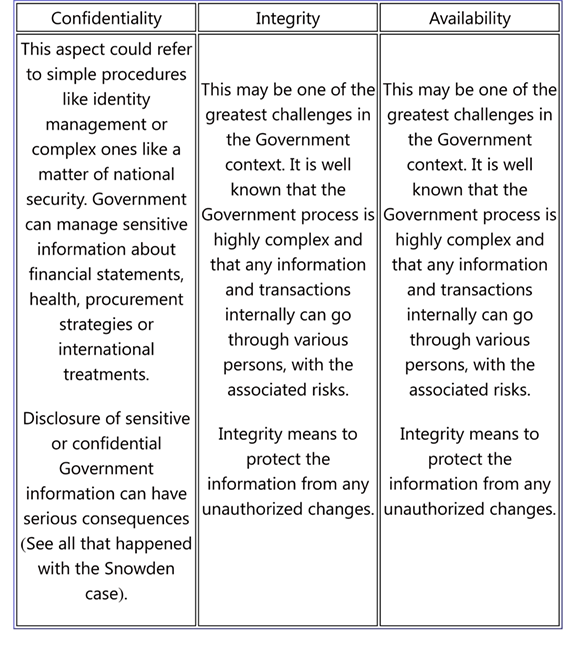
Threat Scenarios
Let’s look this scenario and imagine having 50 identities, which also depend on a private key stored on the user smart device (Smartphone, Laptop, Desktop, Smart TV, Tablet, Phablet.) How can you guaranty local key protection?
For e-Government, the risk should be obvious, being that potential threats are growing in numbers and sophistication.
Furthermore, how can you guarantee NRO or NRE if a citizen has multiple identities from the government’s point of view?
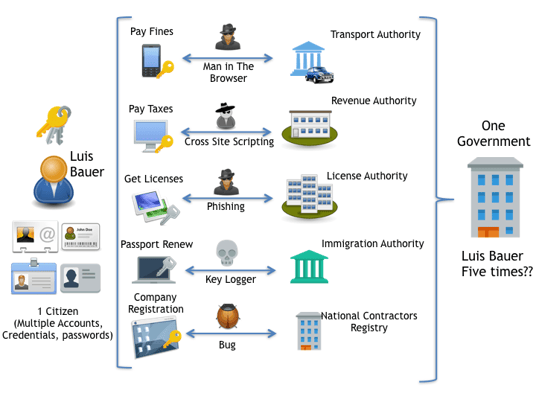
To be even more dramatic and realistic, if any unscrupulous act is successful in acquiring one of the passwords or keys, it would therefore be likely that the other keys are compromised, due to the fact that users tend to use similar passwords for all their accounts (most times with a few variations).
No less important is the functionality/usability problems. For citizens, it is imperative that they feel comfortable using the e-Government processes. Otherwise they will become reluctant to utilize digital processes; thus, encouraging trips to physical agencies to conduct their transactions.
The Centralized Authentication and Signing Approach
The diversity of technology has led to expanding mobility options and therefore, increasing the risks. With centralized signing, it can ensure a high degree of security for the storage of the private keys and large processing capabilities for signing transactions and documents. The signing process goes hand-in-hand with the process of authenticating the identity of the citizens.
Technologically speaking, which factors can be used to authenticate citizens using online services?
- The knowledge of a unique secret (E.g. password, PIN)
- Having a unique device that no one else has (E.g. token, card)
- Being themselves (E.g. fingerprints, DNA)
Adding a second factor for authentication, which is independent of the first factor (like a token or fingerprint in addition to a password), significantly raises the validity of the user identity. In fact, using any two of the three authentication factors above generates much more certainty about the identity of a person.
In the next illustration, you will see the approach to Central Authentication and Signing for e-Government:
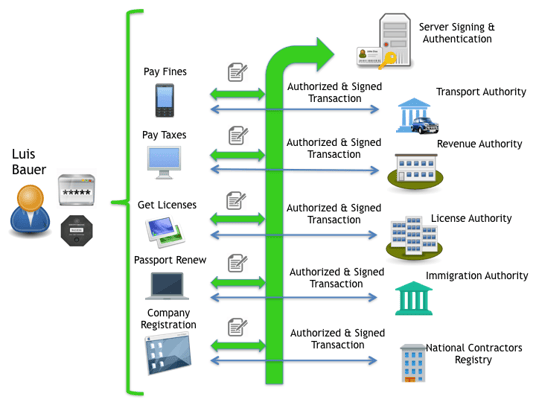
The private key, which is used for encrypting and signing, is safe in a specific hardware security module (HSM), which is physically located outside the premises of the user device and centralized. This reduces the risk of attacks on the user's private keys and streamlines the authentication and signing processes for both the user and individual e-Gov agency.
For NRO and NRE to be in place, any intended and critical transaction should have it guarantees for authenticity (n-Multifactor) and integrity during the operation.
Integrity means that a document or data of a transaction is reliable and stays unaltered during the life of the transaction, including safe storing for evidence. This is where digital signatures come in. Centralized e-Signature technology that can be used by a range of online applications is the ideal approach for any large scale deployment, such as e-Government services.
Steps to strengthen NRO and NRE for e-Government
Some steps that can be taken to strengthen NRO and NRE for e-Government transactions, include:
- Using Multi-factor authentication mechanism (At least two factors).
- Protecting evidence for any important transaction.
- Providing secure storage for the private keys, through specialized hardware.
- Ensuring that they can securely show to their clients what they would be signing using a Trusted GUI (Graphical User Interface), without overloading the clients’ screens.
- Avoiding storage of keys in any user device.
- Using strong algorithm for hashing and encrypting.
- Educating users of internal security policies (E.g. using robust passwords)
- Relaying some aspects of security controls to Trusted Third Parties (TTP); this can play a major role in case of NRO or NRE litigation.
References and Further Reading
- Selected articles on Authentication (2014-16), by Heather Walker, Luis Balbas, Guillaume Forget, Jan Kjaersgaard and Dawn M. Turner
- Selected articles on Electronic Signing and Digital Signatures (2014-16), by Ashiq JA, Guillaume Forget, Jan Kjaersgaard , Peter Landrock, Torben Pedersen, Dawn M. Turner and Tricia Wittig
- REGULATION (EU) No 910/2014 on electronic identification and trust services for electronic transactions in the internal market and repealing Directive 1999/93/EC (2014) by the European Parliament and the European Commission
- Recommendations for the Security of Internet Payments (Final Version) (2013), by the European Central Bank
- Draft NIST Special Publication 800-63-3: Digital Authentication Guideline (2016), by the National Institute of Standards and Technology, USA.
- NIST Special Publication 800-63-2: Electronic Authentication Guideline (2013), by the National Institute of Standards and Technology, USA.
- Security Controls Related to Internat Banking Services (2016), Hong Kong Monetary Authority
Image: "The Library of Congress, Washington, D.C.", courtesy of E. Krall, Flickr, (CC BY-ND 2.0)