ENCRYPTION KEY MANAGEMENT SOFTWARE
CRYPTO KEY MANAGEMENT SYSTEM AND CRYPTO SERVICE GATEWAY
WHY IS STRONG KEY MANAGEMENT SO IMPORTANT?
Governments, banks and businesses operating in highly regulated markets need to prove compliance with security standards and protect sensitive data from unauthorized access.
Failing to do so puts you at risk of huge financial and reputational damage.
That’s why so many organizations turn to Cryptomathic.
We’re pioneers in this space, providing services and solutions that deliver the highest levels of security for over 35 years. We understand the requirements of different markets and the pressures you are under as technology advances, regulations change and risks evolve.

As a market leader in key management, we craft our technologies to meet your needs, including:
CONSOLIDATION
Centralized platforms to manage organization-wide use of keys and policies
/What%20We%20offer/Rectangle%2014.png)
CLOUD VENDOR AND INDEPENDENCE
With vendor-agnostic interfaces to support multi-cloud and multi-vendor HSM setups
/What%20We%20offer/Rectangle%2014%20(1).png)
SCALABILITY AND DATA SOVEREIGNTY
Expanding your ecosystem through integrations and interoperability, without sacrificing data sovereignty
/What%20We%20offer/Rectangle%2014.png)
SIMPLIFICATION AND OPTIMIZATION
With easy-to-use solutions that efficiently meet your security management requirements
/What%20We%20offer/Rectangle%2014%20(4).png)
Common questions and challenges we’re asked to help with include:
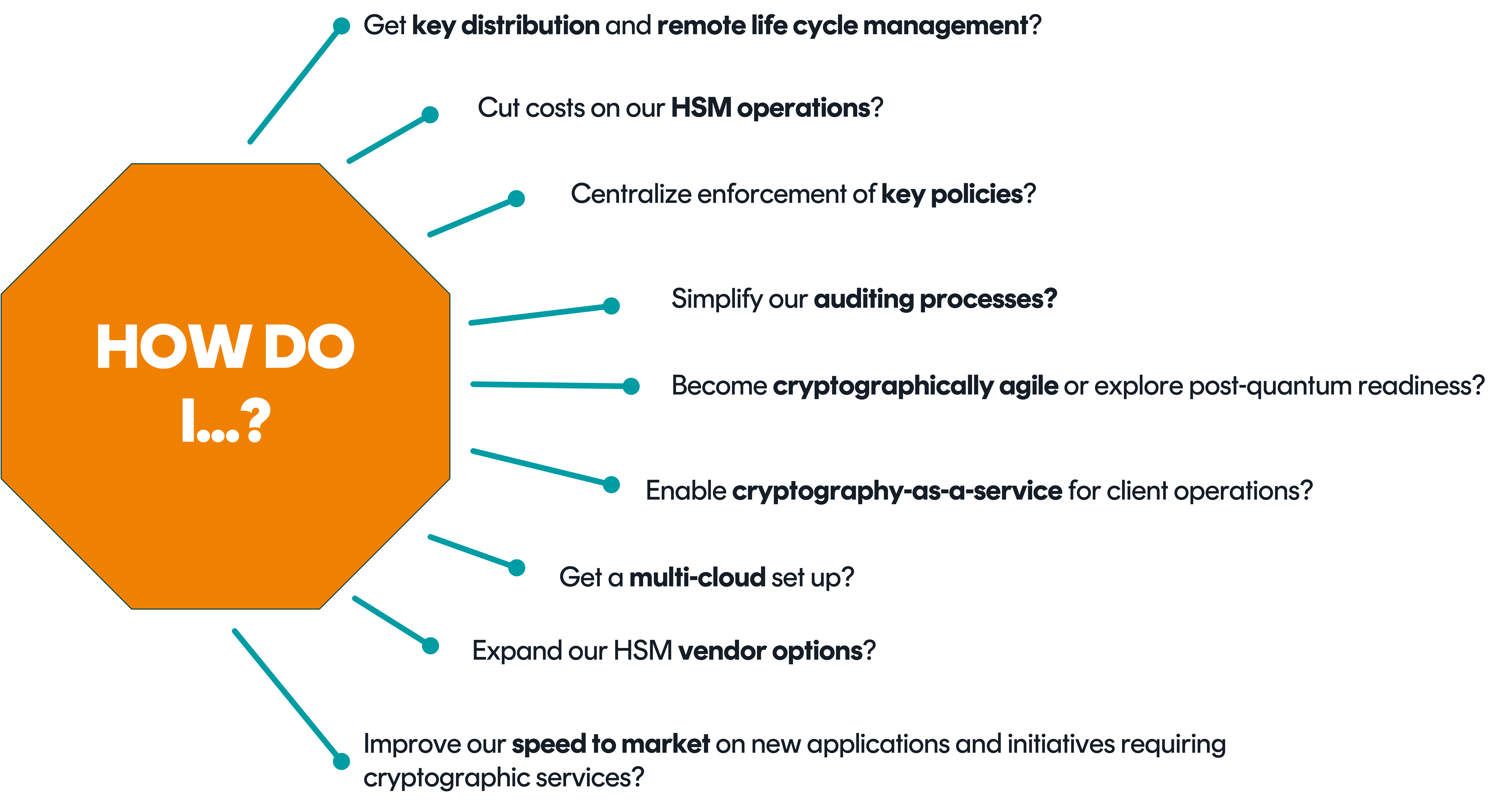
Centralized Key Management Platform
Powerful, flexible enterprise key management and key distribution feature sets
True cryptographic agility
Centralized Key Policy Enforcement across the organization in a single interface
Vendor independence and HSM-as-a-service
Create a consolidated, streamlined, transparent, vendor agnostic HSM-as-a-service offering for your entire organization
Securing multi-cloud setups
Bring your own encryption or keys to your clouds
Simplify auditing
Strong audit and logging trails for each application, in one place
Post quantum readiness
Enable cryptographic agility and centralized enforcement of PQC algorithms
APIs your developers will enjoy
Our APIs are built on a simple powerful Crypto Query Language with zero learning curve
Fits into your existing infrastructure
Integrates to your legacy systems and processes
Data sovereignty, security and privacy by design
Operate in the cloud, on premises or hybrid infrastructure without sacrificing compliance with privacy laws (CCPA, GDPR, Privacy Act, etc.)
Centralize security decisions
All cryptographic decisions for all application can be set centrally
CKMS is your complete key management solution, accessed via a scalable, centralized cryptographic platform, helping you mitigate risks before they happen.
Cryptographic Key Management System (CKMS) benefits:
- Enforce specific roles and clear responsibilities for sets of keys
- Frees staff from manual, repetitive tasks
- Enable staff to concentrate on policy decisions
- Orchestrate delivery of keys between disparate systems
RESOURCES:
How can I meet PCI DSS compliance with key management?
How does CKMS work in action?
Case Study: Swedbank
Where can I get more detail?
Product Sheet
- Acts as a control center for HSM services and policy management
- Solves 50+ common cryptographic challenges, including integration, data encryption, tokenization, transaction authorization, code-signing and key lifecycle management
- Scales effortlessly to deliver agile cryptography from the smallest of applications to the entire enterprise.
- Delivers huge cost and time savings by doing cryptography the right way
RESOURCES:
How can I achieve real-world cryptographic agility?
How does CSG work in action?
Case Study: Barclays
Where can I get more detail?
Product Sheet
Our carefully crafted solutions give you a clear overview and complete control of your cryptographic hardware, policy enforcement, logging, auditing and key management.
Key management
- Import, generate, export and renew keys, as well as enforcing their correct usage (who can use the key and how they can use it)
- Automate complex and repetitive manual key management tasks and liberate skilled staff for higher value tasks
Compliance and auditing
- Audit-log key management processes – in tamper-proof environments – to protect from deliberate attacks and human errors
- Easily demonstrate compliance with standards like PCI DSS and GDPR, and confidently comply with and pass internal/external audits
Health monitoring
- Keep your infrastructure and HSMs healthy with data that allows operators to monitor the status of the entire system, as well as activity on individual HSMs
Trusted access
- Perform admin without restrictions on time or place
- Strong authentication supported by secure PIN entry devices (PEDs) and smart cards. PEDs also support key import/export and key share printing
- Grant applications just enough privilege to complete their necessary functions, via a central policy file – unless something is explicitly allowed, it's forbidden!
Reliability
- Support all widely used cryptographic algorithms, including RSA, AES, 3DES, HMAC and more
- High availability, ensured through clustering of the servers, database and HSMs
- Easily disable or add an HSM in a few clicks with zero downtime to related applications
- Monitor and load-balance operations across a pool of general purpose and specialized HSMs, as appropriate
- Simple integrations with legacy systems and new-build applications via API – avoid steep learning curves!
Typical use cases – an overview
Some typical and proven use-cases for key management include:
- EMV® keys for card issuance and authorization, e.g. BASE24
- ATM and POS remote key loading (RKL)
- HSM application keys, e.g. Atalla, Thales, etc.
- Bring Your Own Key (BYOK) to cloud environments
- Keys for data protection, e.g PCI DSS & GDPR compliance
- X.509 certificates for web servers (SSL/TLS), load balancers and more
Entities that keys can be delivered to include:
- Java Key Store (JCE), PKCS #11 and Microsoft CAPI applications
- Hardware Security Modules (HSM)
- Cloud applications – ‘Bring Your Own Key’ formats
- Payment Platforms – ATM and POS systems; Base24 and zOS integrations
- Integrations with various certificate authorities are also supported.
EMV® is a registered trademark in the U.S. and other countries and an unregistered trade mark elsewhere. The EMV trademark is owned by EMVCo, LLC.
Endorsed Code Signing
Endorsed signing is a unique feature tailored for the code-signing market.
CSG's endorsed signing feature gives you the secure work flows necessary to control what code may be signed. It requires that a minimum mandatory number of authorized ‘endorsers’ endorse a code signing request before a secure signing operation is permitted.
Managed Data Encryption
Tackle a common cryptography headache by ensuring encrypted data can be safely decrypted at a later date, even if the original key has been replaced.
This technique is ideally suited for long-term storage of encrypted data within a business database. Managed encryption is an optional feature that can be made available to any application using CSG.
Managed encryption provides confidentiality, authenticity and integrity (while normal encryption only offers the first of these). This means you can ensure data hasn't been modified while it was stored.
Tokenization
Tokenization protects sensitive data, such as PANs (primary account numbers), as they pass through business systems. The original data is replaced with a token of the same length, using a reversible process.
If you need to comply with PCI DSS, tokenization may provide a way to bring systems out of scope for audits. For more information on PCI DSS compliance, click here.
Confidential Cloud Computing
In the uncertain trust levels of a cloud environment, it’s crucial to take a comprehensive approach to cloud security, incorporating customized security measures and a focus on securing encryption keys.
Our Enclave Security Module (ESM) integrates with CSG to address challenges related to digital asset protection in the cloud.
This includes compliance with complex privacy laws, maintaining control over data and encryption keys, and managing risks from shared infrastructure and potential insider threats.
