4 min read
TR-34 Key Blocks for the TR-34 Exchange Protocol: Basic Principles
 Martin Rupp (guest)
:
01. December 2022
Martin Rupp (guest)
:
01. December 2022

Among all the various key block formats, the TR-34 format is undoubtedly one of the most sophisticated.
The TR-34 norm is an implementation of the X9.24-2 norm. It proposes a realistic and efficient way of exchanging symmetric keys using asymmetric cryptography. This is basically a certificate-based Remote Key Loading (RKL) protocol.
The TR-34 implementation is used in several areas, especially retail banking. For instance, numerous POS terminals and ATMs use this method for remote key loading. It is also part of the PCI security norm.
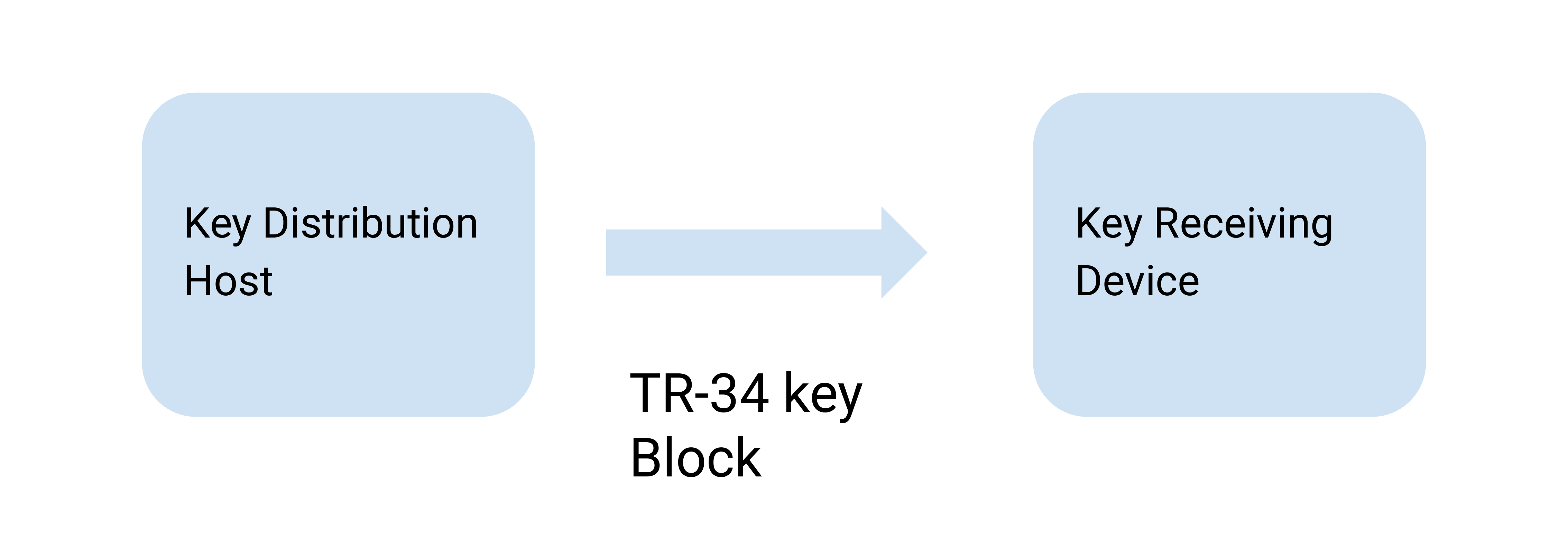
TR-34 defines a key block format inspired by the TR-31 technical report. It transfers cryptographic data from a KDH (key distribution host) to a KRD (key receiving device). The names of these devices define their roles relatively unambiguously.
Usually, the KDH is an HSM (hardware security module) operating in a controlled environment, and the KRD is an ATM or a POS, for instance. The provisioning can be fully automated as follows:
TR-34 Key Blocks
Block Header
A TR-34 key block uses a TR-31 compatible key block header. This header contains various information about the key and its usage. It is not encrypted and may also contain optional key blocks as allowed by TR-31.
A very specific difference with other key block formats is that the header is included twice within the TR-34 key block. Both are in cleartext, at the start of the key block, and encrypted in the key block data.
A key receiving device will need to validate that the deciphered key block data contains a copy of the key block header. That precaution may seem a little redundant since a signature already prevents the tampering of the header. However, it likely appears as a security precaution in case the signature could have been artificially created by engineering a collision, for example.
Encryption
Like a TR-31 key block, a TR-34 key block contains a ciphered block. This is, of course, the key that must be loaded to the key receiving device, which is contained and ciphered within the TR-31 key block.
The symmetric key to be transferred - say Kn - is ciphered inside the whole ciphered block by a symmetric ephemeral key KE. That ephemeral key will be used only once and must possess specific ‘freshness’ properties per the TR-34 implementation.
TR-34 will ship the ciphering key KE with the whole key block. KE will be shipped as a ciphered key itself, namely EKRD. EKRD is the result of ciphering KE with the public key of the key receiving device. The key distribution host unambiguously knows the public key of the key receiving device because they have been previously exchanged and validated since they must originate from the same root certificate authority (CA).
This alone underlines how much more complex (and secure) the TR-34 key block is compared to other block formats. It takes into consideration many different possible attacks and weaknesses and incorporates countermeasures into the format.
Signature
A signature is computed over the ciphered block as for any TR-31 key block. That signature is done by using the private key of the key distribution host.
Additional Specificities of TR-34 Key Blocks
TR-34 key blocks have additional specificities:
- A ‘freshness token’ is added before the key block header. It is used in the ‘one pass’ or ‘two passes’ protocol when exchanging the key block. This prevents, among other things, a possible replay attack.
- A certificate revocation list (CRL) is added at the end of the entire key block after the signature. That CRL gives information to the key receiving device about which key distribution host should not be trusted as compromised. It does not have a significant part in the key exchange itself. The CRL is signed by a CA and cannot be possibly compromised.
Comparison with “Standard” TR-31 Key Block Format
Generalities
Here we show a comparison between a TR-34 key block and a standard TR-31 key block. The TR-34 elements without an equivalent in TR-31 are in grey.
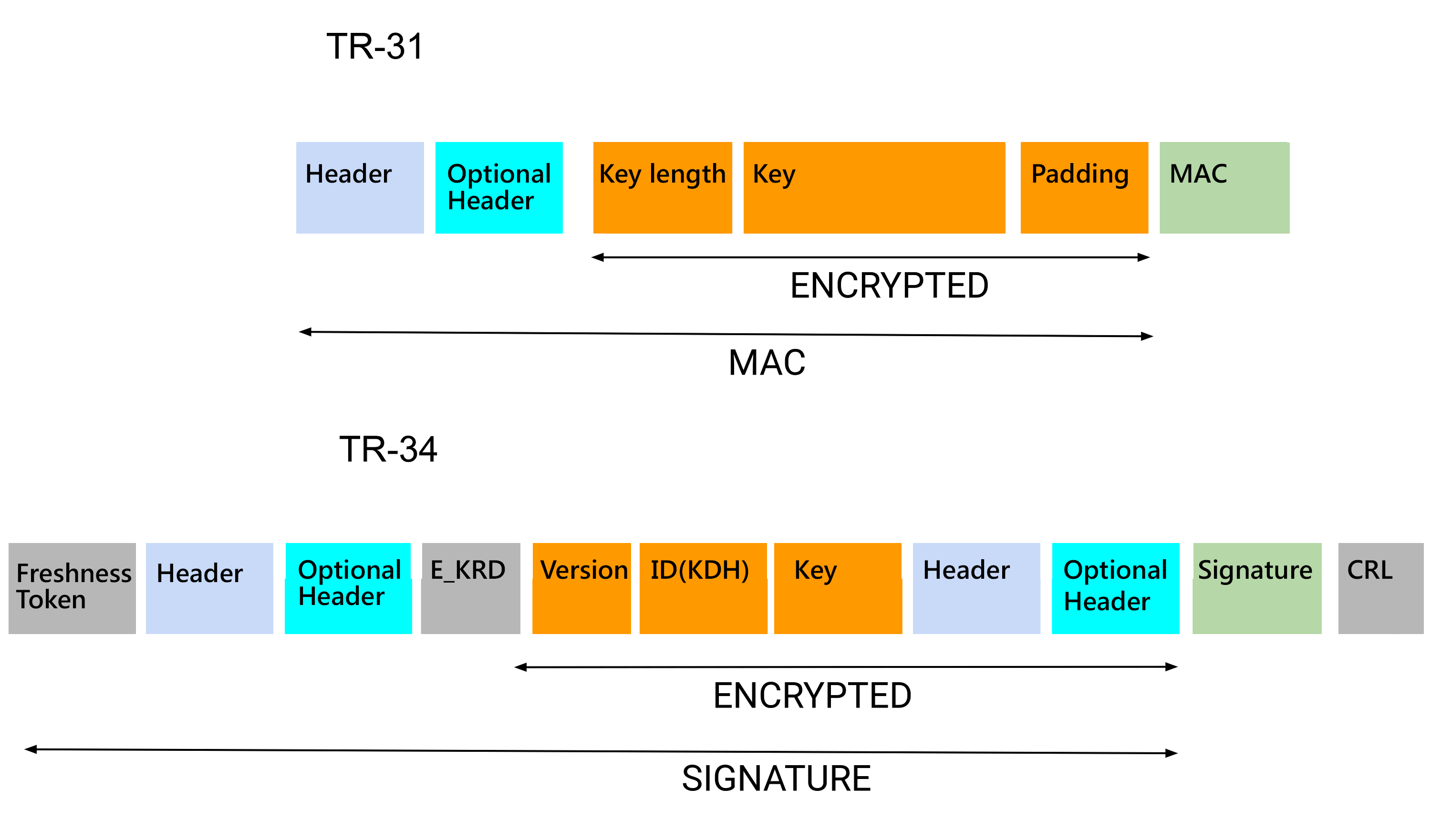
One significant difference between TR-31 and TR-34 key block formats is that TR-34 doesn’t require a symmetric key to be exchanged between the KDH and the KRD before exchanging the key block.
TR-34 Key Header vs. TR-31 Key Header
The TR-34 header is a 16-byte field that coincides with a TR-31 header on many occasions, but with certain proper specificities.
|
Byte |
TR-31 Field name |
TR-34 |
|
0 |
Key Block Version ID |
Not applicable to TR-34 |
|
1-4 |
Key Block Length |
This value has no meaning for TR-34, so any value should be used without possible information on sensitive data lengths. |
|
5 |
Key Usage |
Identical to TR-31 |
|
6-7 |
Algorithm |
Identical to TR-31 |
|
8 |
Mode of use |
Identical to TR-31 |
|
9-10 |
Key version number |
Identical to TR-31 |
|
11 |
Exportability |
In general, that field has no meaning in TR-34 since KRDs never allow export of keys (unless in cases of specific implementation) |
|
12-13 |
Number of Optional Blocks |
Identical to TR-31 |
|
14-15 |
RFU |
Identical to TR-31 |
Summary
TR-34 is a sophisticated norm. Its format comprehends more security elements than most other equivalent key block formats. Therefore, TR-34 is a de-facto choice for loading keys into devices such as ATMs or POS terminals.
References and Further Reading
- More articles on Key Blocks (2019 - today), by Dawn M. Turner and Martin Rupp
- More articles on Key Management (2015 - today), by Matt & Peter Landrock, Stefan Hansen, Dawn Turner, and more
- X9 TR34–2012 - Interoperable Method for Distribution of Symmetric Keys using Asymmetric Techniques: Part 1 – Using Factoring-Based Public Key Cryptography Unilateral Key Transport (August 2012), by the American National Standards Institute
- Information Supplement: PIN Security Requirement 18-3 - Key Blocks (2019), by the PCI Security Standards Council
- Read more articles on the ANSI X9.24-1-2017 (2018 - today), by Martin Rupp, Matt Landrock and more
- ANSI X9.24-1-2017 - Retail Financial Services Symmetric Key Management Part 1: Using Symmetric Techniques (2017), by the Accredited Standards Committee X9 (Incorporated Financial Industry Standards), American National Standards Institute
- ASC X9 TR 31-2018 - Interoperable Secure Key Exchange Key Block Specification (2018), by American National Standards Institute (ANSI)