2 min read
Key Management – A Question of Ownership
This article looks at the problems associated with key management that are common in many businesses today, where there is no clear ownership; then...
2 min read
This article looks at the problems associated with key management that are common in many businesses today, where there is no clear ownership; then...

2 min read
In a retail financial services environment, the compromise of a symmetric cryptographic key is a critical security breach. Such a situation is...
3 min read
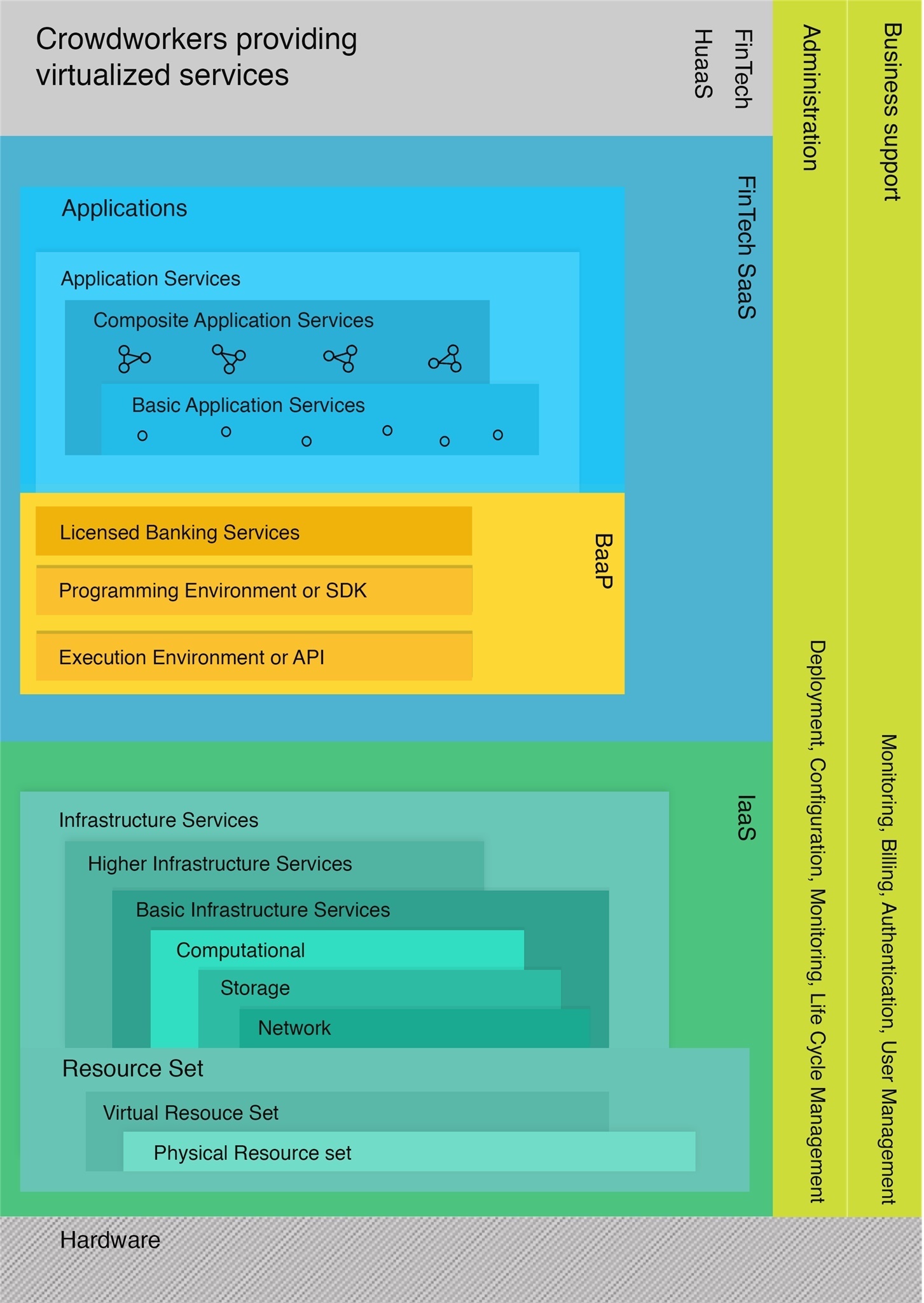
Consumer behavior have shown a dramatic shift toward a preference for seamless digital banking solutions. Many banking customers now want simple and...

3 min read
The European Banking Authority's (EBA’s) new ICT and Security Risk Management Guidelines provide guidance for cybersecurity requirements for...

3 min read
In the last couple of months, facts regarding breaches that occurred during December 2018 at PostBank, the national postal bank operator of South...

3 min read
Invented by Mohamed Atalla, the Atalla key block is the root of all key blocks. All over the globe, hundreds of millions of financial transactions...

8 min read
This article discusses the main phases involved in the life-cycle of a cryptographic key, and how the operational lifetime of a key and its strength...

6 min read
With data protection standards, such as GDPR, and the sheer mass of data that companies collect and accumulate, the protection and control of...

3 min read
A well-rounded solution for securing digital transactions includes the use of both symmetric and asymmetric cryptography and keys. Each method of...