5 min read
Technologies Behind Tokenization For Card Payments And PCI-DSS
The EMV consortium released several standards detailing how “network” tokenization should be handled. There is now a general consensus within the...

5 min read
The EMV consortium released several standards detailing how “network” tokenization should be handled. There is now a general consensus within the...
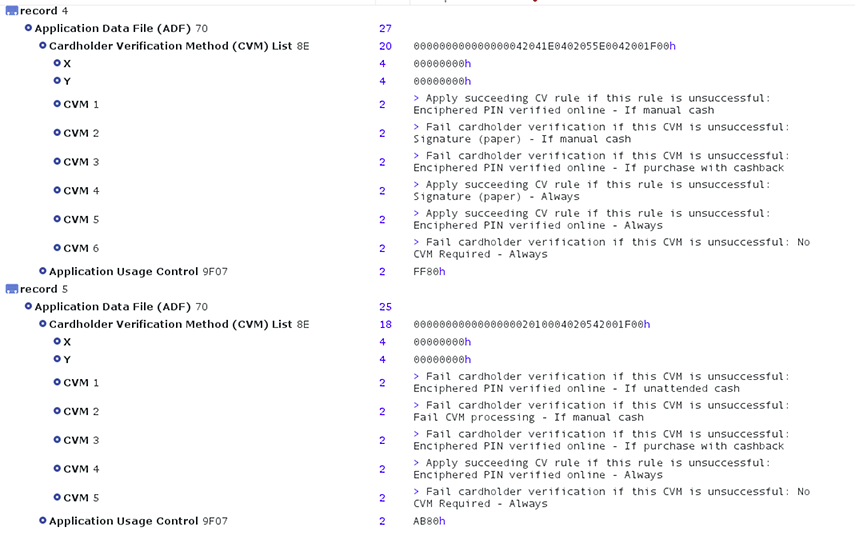
6 min read
EMV is short for EUROPAY-VISA-MASTERCARD. This term is used to refer to standards that have been designed to improve the security of credit and debit...

4 min read
The concept of a token has been used in the digital world for almost 50 years to separate and protect real data elements from exposure. In recent...

3 min read
Crypto-agility, or cryptographic agility, is the capacity for an information security system to adopt an alternative to the original encryption...

3 min read
Part 1 – Increasing Efficiency & Resilience This two-part article discusses how cryptography is employed within organizations today and examines some...

3 min read
Cryptographic keys are used to secure data-at-rest and data-in-transit. Trying to keep them protected yet always available for use is one of the most...

3 min read
Recent revelations in the press have caused industry experts to question just how much trust can be placed in existing cryptographic standards or...