3 min read
EBA On Customer Authentication Under PSD2: Inherence
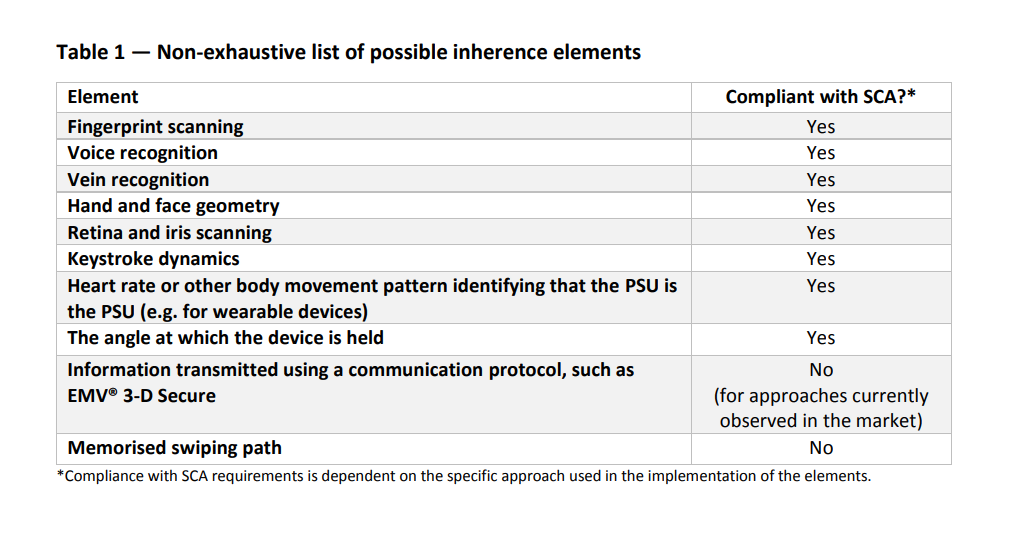
A fundamental objective of the Revised Payment Services Directive (PSD2) has been to reduce the risk of fraud to the maximum extent possible and...
3 min read
A fundamental objective of the Revised Payment Services Directive (PSD2) has been to reduce the risk of fraud to the maximum extent possible and...
5 min read
The World Wide Web Consortium or W3C as it is commonly known was founded in 1994 by the original architect of the World Wide Web, Tim Berners-Lee. It...
4 min read
Cryptographic algorithms can be categorized into three classes: hash functions, symmetric, and asymmetric algorithms. This article sheds light on...

3 min read
Financial institutions and solution providers are busy implementing the requirements of Strong Customer Authentication (SCA) under the Revised...

3 min read
Throughout the last decade, social media has played a vital part in our lives and has significantly shaped the younger generations.

3 min read
Credit cardholders are generally protected from liability if unauthorized transactions are made with their credit cards because of consumer...

3 min read
This article discusses the secure HTTPS Protocol intended for web-resources and its principles of operation as well as its strengths and weaknesses....

5 min read
When it comes to conducting transactions, the possibility of fraud is always a risk that cannot be overlooked. In person, an individual may present...

3 min read
Non-repudiation is a legal concept that is widely used in information security. It refers to any service which provides proof of the origin of data...